Issue
- ESET PROTECT On-Prem
- ESET PROTECT
- ESET Vulnerability & Patch Management
- ESET Endpoint Security and ESET Endpoint Antivirus for Windows
- ESET Endpoint Antivirus for Linux
- ESET Mail Security for Microsoft Exchange Server
- ESET PROTECT Hub
- ESET Business Account
- ESET MSP Administrator 2
- ESET Inspect On-Prem and ESET Inspect
- ESET Secure Authentication On-Prem
- ESET Endpoint Encryption
- ESET Endpoint Security for Android
- ESET Endpoint Security and ESET Endpoint Antivirus for macOS
- ESET Server Security for Linux
- ESET Gateway Security for Linux
- ESET Direct Endpoint Management plugin for ConnectWise Automate
- ESET Direct Endpoint Management plugin for N-able N-central
- ESET Direct Endpoint Management plugin for NinjaOne
- ESET Direct Endpoint Management plugin for DattoRMM
Solution
ESET PROTECT On-Prem
- In version 11.0 and earlier, generating
.pdfreports do not work for ESET PROTECT On-Prem installed on Red Hat Enterprise Linux Server 8 – To fix this issue, you can buy and install a third-party QtWebKit4 package. This issue is resolved in version 11.1 and later. - Computer names written in Hebrew are unreadable after a report is exported. To fix this issue, Windows server users can enable language support. On the Windows server, navigate to Control Panel → Clock, Language, and Region → Region → Administrative → Change system locale, and select the check box next to Use Unicode UTF-8 for worldwide language support. Linux users must install additional Left to Right direction (LTR) compatible fonts.
- macOS Ventura (13) device reported as encrypted with third-party software even if it is not encrypted (and no ESET Full Disk Encryption options are offered). Workaround: Use a Software Install task (with an ESET Full Disk Encryption license) to install ESET Full Disk Encryption.
- When configuring the password-protected settings in an installer with ESET Endpoint Antivirus/Security version 9.0 or 9.1 for Windows, the settings may not be applied correctly. We recommend configuring password-protected settings directly in the ESET PROTECT Web Console by creating a policy and assigning it to specific computer groups to ensure the settings are applied accurately and consistently.
ESET PROTECT
- Some Windows 7 computers with legacy BIOS may be incorrectly identified as eligible for ESET Full Disk Encryption deployment by ESET PROTECT.
- macOS Ventura (13) device reported as encrypted with third-party software even if it is not encrypted (and no EFDE encryption options are offered).
- Workaround: Use a Software Install task (with an ESET Full Disk Encryption license) to install ESET Full Disk Encryption.
- When configuring the password-protected settings in an installer with ESET Endpoint Antivirus/Security version 9.0 or 9.1 for Windows, the settings may not be applied correctly. We recommend configuring password-protected settings directly in the ESET PROTECT Web Console by creating and assigning a policy to specific computer groups to ensure the settings are applied accurately and consistently.
- MSP administrators using ESET Cloud Office Security cannot filter MSP customers in the ESET Cloud Office Security dashboard.
- Linux endpoint 11.x and later users can activate Vulnerability & Patch Management, however, activation is limited to supported distributions. Therefore, V&PM cannot be activated on all Linux endpoints and activation attempts will fail for unsupported distributions (even if incorrectly indicated as eligible in ESET PROTECT).
- Available patches shown in ESET PROTECT may not list all related dependencies for Linux endpoint and server products v12.0 running on RHEL, Amazon Linux, Oracle Linux, AlmaLinux, or Rocky Linux. When these patches are applied, not-listed dependencies are also automatically upgraded.
ESET Vulnerability & Patch Management
- After scanning for vulnerabilities on MS Windows Server, the report does not display any vulnerabilities in the operating system.
- Linux endpoint 11.x and later users can activate Vulnerability & Patch Management, however, activation is limited to supported distributions. Therefore, V&PM cannot be activated on all Linux endpoints and activation attempts will fail for unsupported distributions (even if incorrectly indicated as eligible in ESET PROTECT).
- Available patches shown in ESET PROTECT may not list all related dependencies for Linux endpoint and server products v12.0 running on RHEL, Amazon Linux, Oracle Linux, AlmaLinux, or Rocky Linux. When these patches are applied, not-listed dependencies are also automatically upgraded.
ESET Endpoint Security and ESET Endpoint Antivirus for Windows
- During a push install to client computers on the network, you may see the error message "Remote Registry Opening (ESET Security Product Info) Result Code: 5 (Access is denied.)". This signifies a permissions conflict.
- Ransomware Remediation folder exclusions require manual post-editing for every entry to be functional—an asterisk needs to be appended.
Check the permissions of a specific user
-
Click the Start button, type regedit and click the Registry editor icon on the left-side menu or press the Enter key.
-
Right-click HKEY_LOCAL_MACHINE and select Permissions from the menu.
-
In the Permissions for HKEY_LOCAL_MACHINE window, click Advanced.
-
Verify that the button shows Disable inheritance and select the check box next to Replace all child object permissions entries with inheritable permissions entries from this object. Click OK.
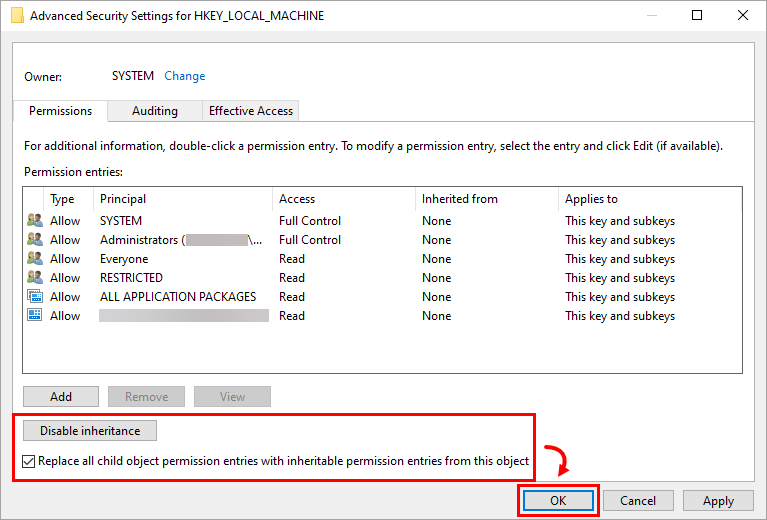
Figure 1-1 -
Click OK to exit the Permissions window.
ESET Endpoint Antivirus for Linux
- Applications installed under Snap (e.g., Firefox) may not be scanned for known vulnerabilities, so their vulnerabilities may not be listed.
- Vulnerability assessment is not available in Linux Mint version 21.3
ESET Mail Security for Microsoft Exchange
- During the ESET Mail Security for Microsoft Exchange Server installation on a system with Microsoft Exchange Server 2013 SP1 installed, or when updating your Microsoft Exchange Server 2013 with SP1 while already running ESET Mail Security for Microsoft Exchange Server, you may receive the error message "0xC00CE503: MSG_E_COMMENTSYNTAX Incorrect syntax was used in a comment". To resolve this issue, apply the Microsoft hotfix.
- Vulnerability scans currently cannot list vulnerabilities for the Windows Server Operating systems.
ESET PROTECT Hub
- See the known issues in ESET PROTECT Hub (the link is only accessible to registered ESET PROTECT Hub customers, and you must log in to view the content).
ESET Business Account
- ESA user quantity might exceed the specified margin.
- Activated EFSU and ESET Full Disk Encryption devices might not appear with an Offline license file after activation.
- ESET Cloud Office Security reactivation might end with issues.
- Multiple license removals might end in an unexpected error.
- Duplicated activated devices might appear when a license is migrated from ESET License Administrator to ESET Business Account.
- The number of activated devices displayed on the dashboard might not synchronize with product usage.
- Downgrading a license to a Home product might not apply to an ESET Business Account.
- You can deactivate licenses with only up to 200 seats.
- Filtering by LastSeen status or sorting by ascending/descending order does not work in the Activated Devices section of EBA.
ESET MSP Administrator 2
ESET Inspect On-Prem and ESET Inspect
- ESET Inspect On-Prem (all versions): When installing or upgrading the ESET Inspect server using the ESET PROTECT version 11.1, the user account being used in this process requires the ESET Inspect server permission set and also the Client task (the whole category) permission set for the installation or upgrade to work correctly.
ESET Secure Authentication On-Prem
- ESET Secure Authentication version 3.0.69.0 not sending radius attributes
- Cannot restart or reinstall the ESET Secure Authentication service (Active Directory integrated mode)
ESET Endpoint Encryption (EEE)
- Logins using the Network Login authentication type are not migrated in an upgrade from a previous version.
- Uploading an EEE for a macOS client package into an EEE server in non-multi-tenant mode will fail. You can verify the version number on the login screen. For example, 3.3.0.321 MT indicates the server is in multi-tenant mode. 3.3.0.321 indicates it is in non-multi-tenant mode and will experience failure.
- When installing a Windows 10 Feature Update, the process fails with the message 0xC1900101 - 0x20017 The installation failed in the SAFE_OS phase with an error during BOOT operation.
- When upgrading a Windows 10 system to the 1903 build, installing the update can cause the system to crash when booting.
- Full Disk Encryption Login Screen Size – In earlier versions, the pre-boot FDE login window does not fill the screen fully. The login screen is initialized as an 80x25 character screen, and the graphics card will scale the screen automatically to fit the resolution. On some devices (for example, Microsoft Surface), the scaling of the login screen is controlled by the firmware or the display. Starting with v4.9.2, support has been added to improve the graphics for high-resolution screens and a zoom feature has been introduced.
- Some DELL Latitude systems fail to boot after they have been Full Disk Encrypted.
- In EEE client v5.3.71 and v5.3.75, after initiating Full Disk Encryption on a computer managed by Direct Endpoint Management (DEM), Safe Start will fail and, encryption will not start. Continue using the previous version of the EEE client until the bug fix is released in a later version.
DELL systems fail to boot after ESET Full Disk Encryption
The following DELL Latitude systems are known to be affected when Legacy BIOS is enabled and SATA Operation is set to either AHCI or RAID On:
- E7250
- E7350
- E7450 (7000 Series Ultrabook)
- E5250
- E5350
- E5450
- E5550 (5000 Series Laptop)
Systems starting in UEFI mode are not known to be affected. Certain versions of the BIOS in these DELL Latitude systems are known to have a bug, which causes Full Disk Encryption to be unable to access the disk correctly during start. A black screen with a flashing cursor displays when starting your computer.
This can occur directly after the system is Full Disk Encrypted but can also occur at a later time after numerous successful restarts. This affects not only ESET Endpoint Encryption Full Disk Encryption but also many other manufacturers of software disk encryption.
A DELL-provided BIOS update might fix the issue.
ESET Endpoint Security for Android
- Due to changes in Stock Android by Google, ESET Endpoint Security for Android can no longer execute the relevant steps related to the Wipe command. To ensure at least some data security on Android 6 devices, this command behaves the same way as Enhanced factory reset. Among other things, for example, the process will end up with a restore to factory default settings.
- Due to changes in Android 7, Google enables the user to deactivate an active device administrator and uninstall the app in a single action. Users can now uninstall EESA without entering the admin password.
- If you have an active app on your device with screen overlay permissions on your Android 6 (Marshmallow) device, you cannot grant permissions to any other app, including your ESET product. To enable permissions for your ESET product, you must disable screen overlay permissions for the app.
ESET Endpoint Antivirus and ESET Endpoint Security for macOS
Version 8.x (ESET Endpoint Security for macOS)
- The previous versions, 7.1 or 7.2, wrongly migrated TSN RTP settings from version 6. If the user upgrades from version 6 to a previous version of the 7.1 or 7.2 build, we highly recommend installing the 8.0 build, opening the RTP TSN → For all file operations settings and disabling the Advanced heuristic setting. This setting was wrongly set to On by migration from version 6.
- The proxy password is not encrypted in the configuration dump.
- Full disk access is lost after the macOS Sonoma restart.
- This is a macOS issue that Apple knows about and will fix in upcoming minor macOS releases.
- We added a workaround for this to version 8.0, and the full disk access is not lost, at least on real hardware.
- It may be still lost in virtual environments. The workaround stays the same as for version 7.4.
Version 7.4 (ESET Endpoint Antivirus for macOS)
- In versions 7.3 to 7.4.1500.0, the onboarding wizard is shown during the remote installation. When the onboarding wizard is running, the product does not communicate its statuses into the ESET PROTECT Web Console, resulting in the admin being unaware of the current state of the product.
- Workaround:
- Main Method: Create a dummy configuration file before launching the remote installation. For a detailed guide, visit Onboarding wizard displayed during a remote installation of ESET Endpoint Antivirus for macOS
- Alternative Method 1: The local user exits the onboarding wizard.
- Alternative Method 2: After the installation, restart the endpoint device. This will exit the onboarding wizard, and the product will launch correctly.
- Workaround:
- The previous releases of version 7.1 and 7.2 wrongly migrated the TSN RTP setting from version 6. If the user upgrades from version 6 to version 7.1 or 7.2, we highly recommend installing version 8.0, navigating to TSN RTP → For all file operations and disabling the Advanced heuristic setting. The migration from version 6 wrongly enabled this setting.
Version 7 (ESET Endpoint Antivirus for macOS)
- Information to know before upgrading to ESET Endpoint Antivirus for macOS 7.
- When upgrading from version 6 to version 7, it is required to restart the system after the upgrade is finished and before allowing Full Disk Access for the main app.
Version 6
- On macOS Sonoma (14), the drop-down menu with the list of Wi-Fi networks is empty in Firewall settings → Zones.
- The Scheduler tool in ESET Endpoint Security for Mac and ESET Endpoint Antivirus for Mac running on macOS Big Sur (11) cannot run scheduled tasks for sandboxed applications. For example, all applications downloaded from the Apple store are sandboxed. You can find more information about Sandbox in the Apple documentation.
- The Scheduler can still create tasks for ESET applications and other non-sandbox applications.
- A computer scan that is triggered from ERA and finds malware displays an action window on the endpoint computer that requires user interaction.
- Solution: Use Strict Cleaning when triggering scans from ERA.
- Media Control settings are not migrated to Device Control during an upgrade from version 6 to 6.1 and later.
- Mail protection cuts off an email when sending it with ISO-2022-JP encoding.
- Upgrade to version 6 can only be done from ESET NOD32 Antivirus 4 Business Edition version 4.1.100 and later.
- Folders used as storage for several OS X Server services must be excluded from scanning.
- You cannot deactivate the Endpoint License from ESET License Administrator.
- The Scan on File action blocks communication between VMware Fusion from version 7 and vCenter on OS X from version 10.10.4.
- Solution: You must set exclusions and exclude the following folder:
- On macOS High Sierra (10.13) and earlier:
/System/Library/Preferences/Logging/Subsystems - On macOS Mojave (10.14):
/private/etc/*.*/Applications/VMware Fusion.app/Contents/*.*/Library/Preferences/Logging/*.*
- On macOS High Sierra (10.13) and earlier:
- Solution: You must set exclusions and exclude the following folder:
- Cleaning
loginwindow.pliston macOS High Sierra (10.13) only works if you upgrade with products that have the same application bundle name. - The firewall may fail in ESET Endpoint Security for Mac 6.10.900.0 on macOS Big Sur (11). We advise disabling all application-specific rules for the firewall in ESET PROTECT On-Prem policies before you upgrade ESET Endpoint Security to 6.10.900.0 on macOS BigSur (11). To partially compensate for these changes, we advise dividing your policies into two policies. The first policy will have the same firewall settings as your earlier policy but will only be applied to computers with macOS Catalina (10.15) and earlier. The second policy will be for computers with macOS Big Sur (11), where the application-specific rules will be removed.
- Text is missing in firewall dialogues in your ESET product for Mac.
Products affected:- ESET Cyber Security Pro 6.10.600.0 and later
- ESET Cyber Security 6.10.600.0 and later
- ESET Endpoint Security for Mac 6.10.900.0 and later
- ESET Endpoint Antivirus for Mac 6.10.900.0 and later
ESET Server Security for Linux
ESET Gateway Security for Linux
- In certain configurations, you may experience problems with video streaming on your network. For example, your media player may be unable to fill its video buffer, causing lags or synchronization issues during your video conferences.
Optimize ESET Gateway Security to prevent video streaming issues
If you encounter these or similar symptoms, we recommend you add a scanning exception for the problematic streaming address to the http directory of the ESETS configuration directory. To exclude a streaming address from scanning, use the following instructions:
-
Append the streaming address you want to exclude from scanning to the whitelist_url file. To add an exception, replace the streaming address example in the following command with the address you want to exclude and run the command:
echo "streaming.address.com:80/*" >> /etc/esets/http/whitelist_url -
To finalize adding/removing URL addresses, you must restart the ESETS daemon. Use the following command to execute an immediate restart:
/etc/init.d/esets_daemon restart
For more information, use the following command to read the esets_http man page:
man esets_http