Issue
- Enable OpenSSL 3.x support for ESET PROTECT On-Prem
- Certificate error for agents using earlier operating systems
- Upgrade OpenSSL 1.1.1 to OpenSSL 3.x
Solution
Certificate error for agents using earlier operating systems
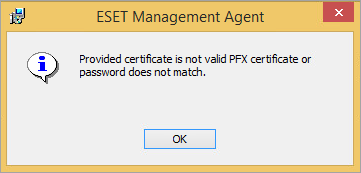
You receive the following error when deploying agents on computers running older operating systems: Provided certificate is not valid PFX certificate or password does not match.
-
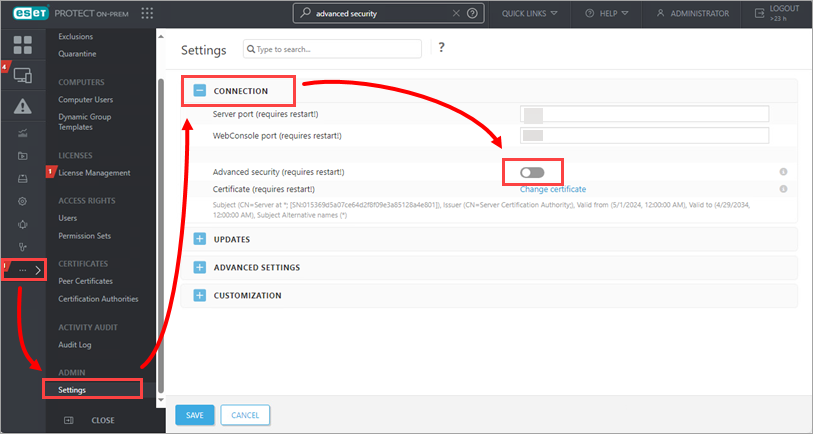
Click More → Settings, expand Connection, disable the toggle next to Advanced security and restart the server service.
-
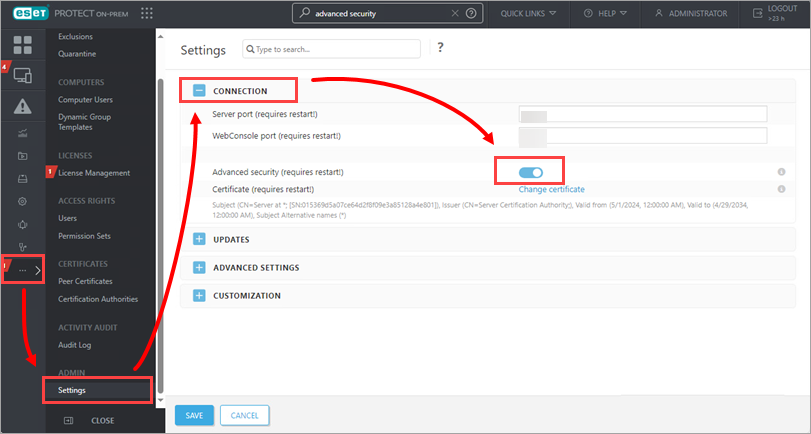
Click More → Settings, expand Connection, enable the toggle next to Advanced security and restart the server service.
-
Select the new certificate when generating installers or deploying agents using the agent deployment task.
-
Create a new agent policy to distribute the new certificates to clients on an older operating system.
Upgrade OpenSSL 1.1.1 to OpenSSL 3.x
Existing ESET PROTECT On-Prem environments that use OpenSSL 1.1.1 can upgrade to OpenSSL 3.x.
-
Download and build/install OpenSSL 3.x on the server.
-
Run the ESET PROTECT Server installation command again to link to the OpenSSL 3.x libraries.
-
Create Certificate Authority and Peer Certificate. The new certificates will facilitate the OpenSSL 3.x algorithms.
-
Create a new agent policy to distribute the new certificates to eligible clients. The original certificates are still available and can be used to connect earlier devices that do not recognize the new CA.