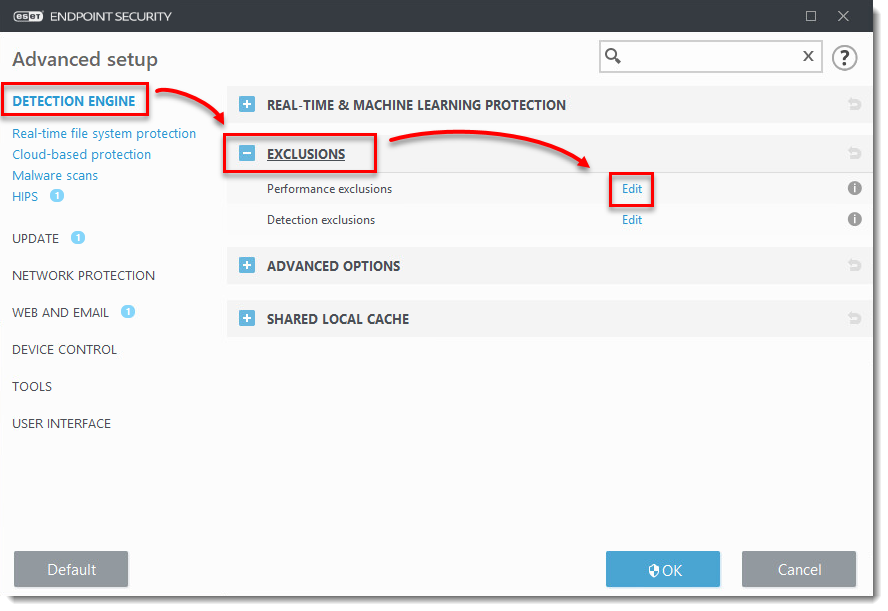
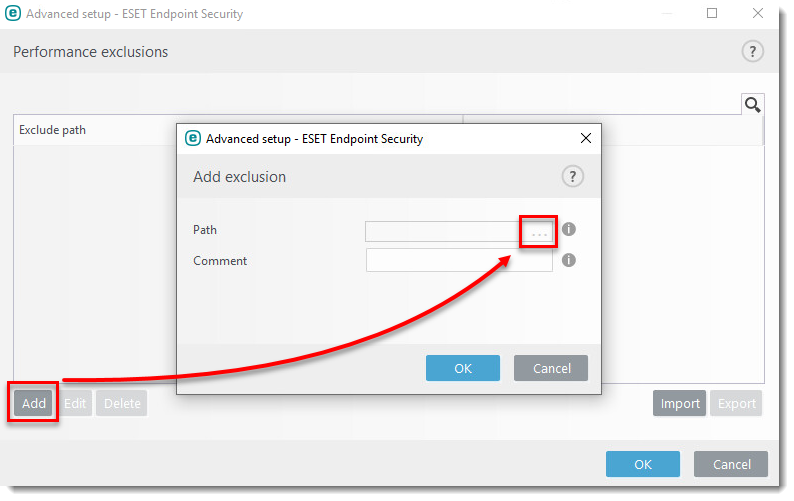
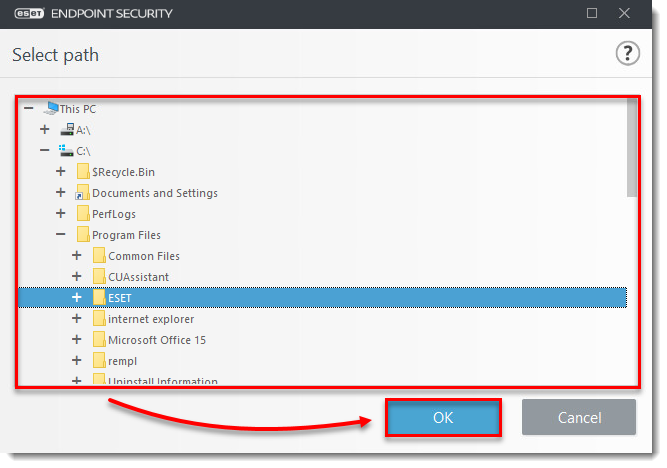
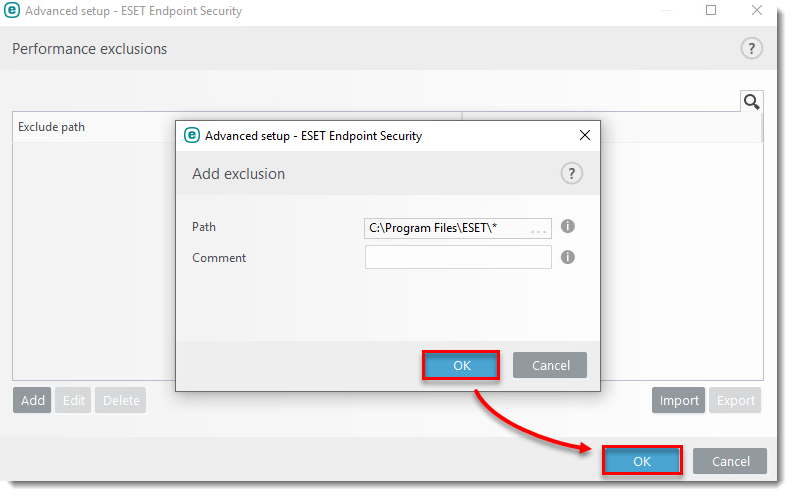
Issue
- File-level scanning of some email servers, backup software, Customer Relationship Management (CRM) software, etc. causes abnormal system behavior
- Use ESET Configuration Editor to create a configuration that excludes specific applications or folders from Real-time scanning
- Processes Exclusions
- Detection Exclusions
Solution
If you are still experiencing issues with your application, it is possible that you need to exclude it from Web access protection if it connects to the internet. Visit Unblock a safe website on an individual workstation in ESET endpoint products.