Issue
- Disable HIPS for troubleshooting purposes
- Enable HIPS protection
- Verify that HIPS is enabled on your system
Details
Click here to expand
The Host-based Intrusion Prevention System (HIPS) protects your system from malware and unwanted activity attempting to affect your computer negatively.
HIPS utilizes advanced behavioral analysis coupled with the detection capabilities of network filtering to monitor running processes, files and registry keys. HIPS is separate from Real-time file system protection and is not a firewall; it only monitors processes running within the operating system.
Users can define a custom ruleset to replace the default ruleset; however, this requires advanced knowledge of applications and operating systems and is not recommended in most situations.
Solution
Disable HIPS protection for troubleshooting purposes
Press the F5 to open Advanced setup.
Click Detection Engine → HIPS, and click the toggle next to Enable HIPS to disable it.
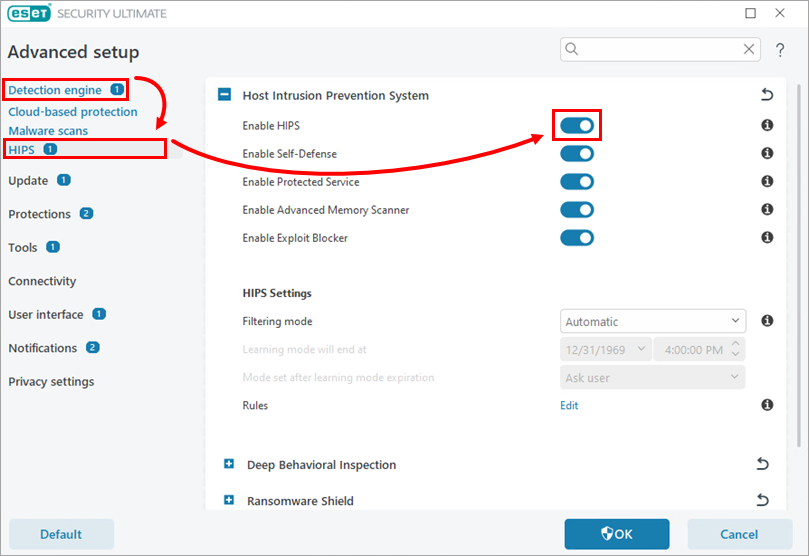
Figure 1-1 Click OK.
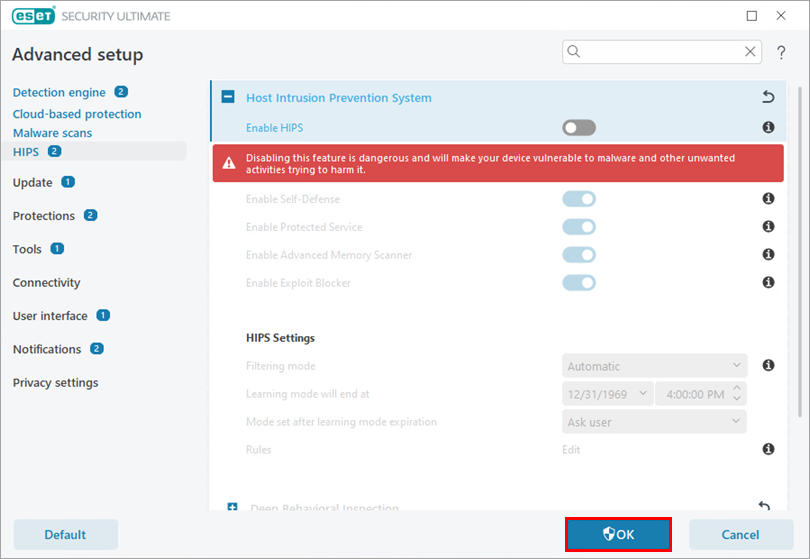
Figure 1-2 Restart your computer. After your computer restarts, HIPS will be completely disabled. The ESET program window will display a red border to indicate that maximum protection is not ensured and your computer is vulnerable to threats. Be sure to re-enable HIPS after you finish troubleshooting.
Enable HIPS protection
Click Enable HIPS. If the Security alert does not appear on the Overview screen, click Setup → Computer protection and click the toggle next to Host Intrusion Prevention System (HIPS).
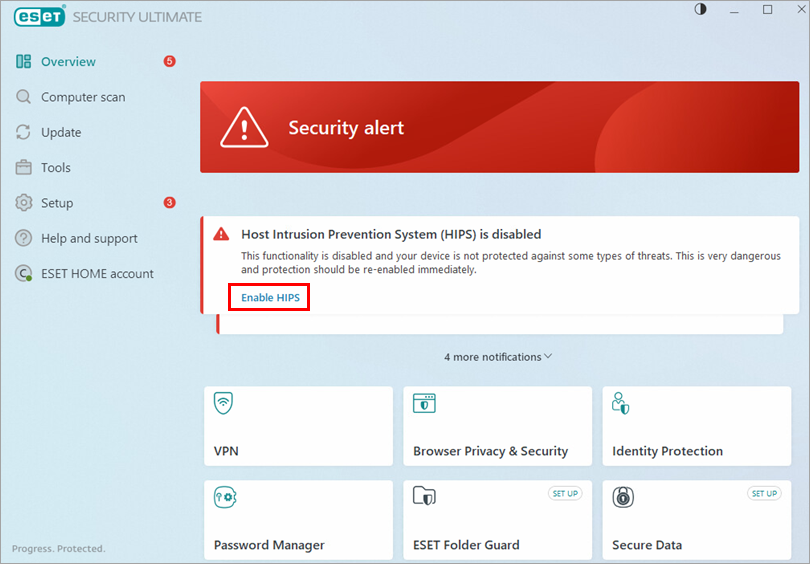
Figure 2-1 Click the toggle next to Enable HIPS to enable it.
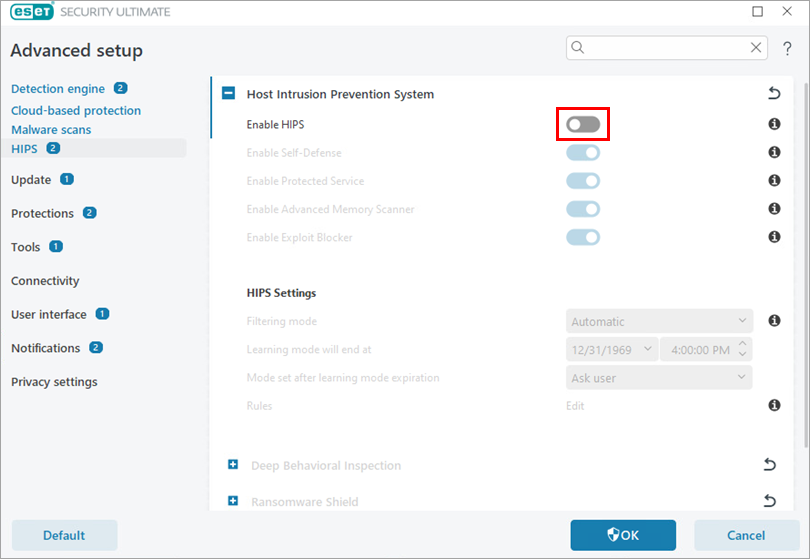
Figure 2-2 Click OK and restart your computer for the changes to take effect. When your computer has finished restarting, maximum protection will be restored and your computer will be fully protected.
Verify that HIPS is enabled on your system
Click Setup → Computer protection.

Figure 3-1 - Ensure the toggle next to Host Intrusion Prevention System (HIPS) is enabled. If HIPS has been disabled on your system, click here for instructions to re-enable HIPS.

Figure 3-2