Issue
- You received a "Weak router password", "Update your router's firmware", "Malicious network redirection", "Open network services", or "Malicious router settings" notification in your ESET product
- The primary DNS server has changed on your router
- Google or Facebook is blocked by your ESET product
- You received an "Address has been blocked", "Access to the IP address was blocked", or "Threat found" message
- Your ESET product detects a Win32/Sality, Win32/RBrute or Win32/Fareit threat
- How can I protect myself?
- My router is infected. What should I do?
Details
Click to expand
For more information about this operation, visit the following ESET resources:
- Win32/Sality newest component: a router’s primary DNS changer named Win32/RBrute
- Wi-Fi virus Chameleon infects whole cities ‘like airborne disease’
- DNS poisoning attack defined
- Secure your router: How to help prevent the next internet takedown
Win32/RBrute.A scans the internet for router administration pages in order to change the entry for their primary DNS server. The rogue DNS server then redirects users to fake websites that are part of the Win32/Sality operation.
At the time of our investigation, the following routers have been targeted by Win32/RBrute.A:
- AirLive WT-2000ARM
- Cisco routers matching “level_15_” in the HTTP realm attribute
- D-Link DSL-2520U
- D-Link DSL-2542B
- D-Link DSL-2600U
- Edimax AR7084
- Huawei EchoLife
- TP-LINK
- TP-Link TD-8816
- TP-Link TD-8817
- TP-Link TD-8817 2.0
- TP-Link TD-8840T
- TP-Link TD-8840T 2.0
- TP-Link TD-W8101G
- TP-Link TD-W8151N
- TP-Link TD-W8901G
- TP-Link TD-W8901G 3.0
- TP-Link TD-W8901GB
- TP-Link TD-W8951ND
- TP-Link TD-W8961ND
- TP-Link TD-W8961ND
- ZTE ZXDSL 831CII
- ZTE ZXV10 W300
Solution
How can I protect myself?
- Keep your ESET product up to date—Specialists at the ESET virus lab analyze online threats every day and release regular updates to continually improve the level of protection for ESET users. By default, your ESET product updates the modules several times a day. These updates enable rapid detection of emerging threats and keep your computer protected from sites and downloaded files you might be redirected to because of DNS poisoning.
- Keep the software on your router updated—New security patches and firmware updates help to protect your router from misuse. Check your router administration page or configuration tool regularly for firmware updates.
- Change the default username and password—Routers often use the default credentials for an initial configuration. Default login information is easy to guess and can be found on the internet. Change the default login information to a unique username and strong password.
- Disable remote management—This feature allows a user to configure, upgrade and check the status of your router remotely. We recommend that you disable remote management when you are not using it to minimize exposure to attacks on your router from outside of your local network.
- Consider changing the name of your access point—Choose an access point name that does not contain the device name, manufacturer name or other information that reveals what type of router you are using. This is a simple change and it makes an eventual attack a bit more challenging.
- Disable Universal Plug and Play—If UPnP is not a service that you use, you should disable this option in router settings. With UPnP enabled, your router is more vulnerable and your network can be accessed without authentication.
- Restrict access to the router's web interface to your LAN only—Allow only a specific range of IP addresses located on your LAN (local area network) to access your router's web interface. For example, if your IP address is 192.168.2.25 and it is inherited from the router's DHCP server, allow the subnet/range of IP addresses from 192.168.2.1 to 192.168.2.254 (Figure 1-2 is an example of a router administrator page—your page may be different).
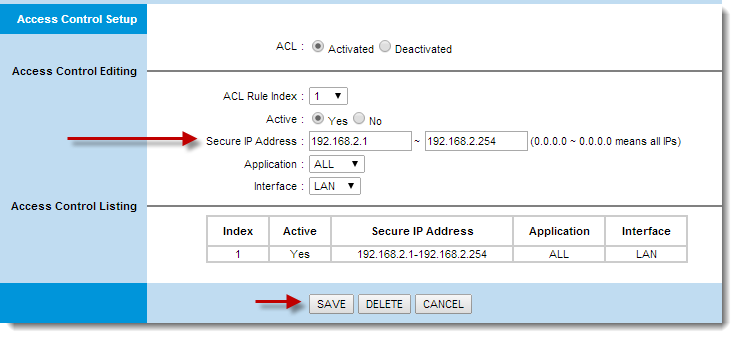
Figure 1-1
Click the image to view larger in new window
My router is infected. What should I do?
- Verify that your ESET product is up to date and receives module updates.
- Reset your router to use default settings.
- Change the password for your router.
- Ensure that remote management on your router is disabled.
- Restrict WAN (Wide Area Network) access to your router.
- Restart your computer.
- Clear your browser cache.
- Run a computer scan to verify that your computer is not infected.
If the router you are using does not use current security technology, you can lessen the risk to your system by purchasing a newer router.