Issue
- ESET Windows endpoint products with TLS filtering enabled cannot connect to an intranet or localhost site using HTTPS
- You are asked for the password repeatedly, but the credentials are rejected
- Single sign-on does not work with TLS filtering enabled in ESET endpoint products when accessing intranet sites using HTTPS
- Credentials must be entered manually using an HTML form
- Create an exception on the affected computers to resolve the issue
- Disable the "Extended Protection for Authentication" feature on the server
Details
Click to expand
This situation can occur if the authentication is based on protocols such as SPNEGO (WWW-Authenticate: Negotiate), Kerberos, and NTLM and if Channel Binding Tokens are used.
This behavior is a security feature of the underlying authentication protocol.
Solution
Create an exception on the affected computers
Press the F5 key to access Advanced setup.
Click Protections → SSL/TLS and next to Certificate rules, click Edit.
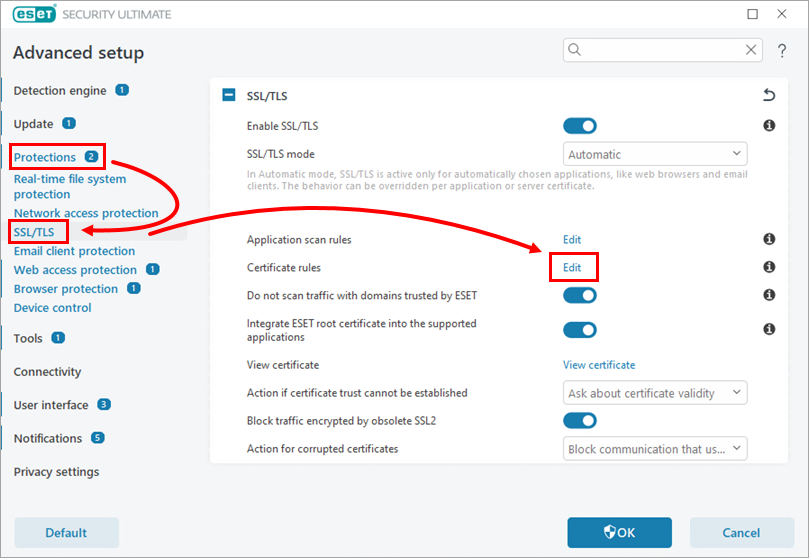
Figure 1-1 Click Add.
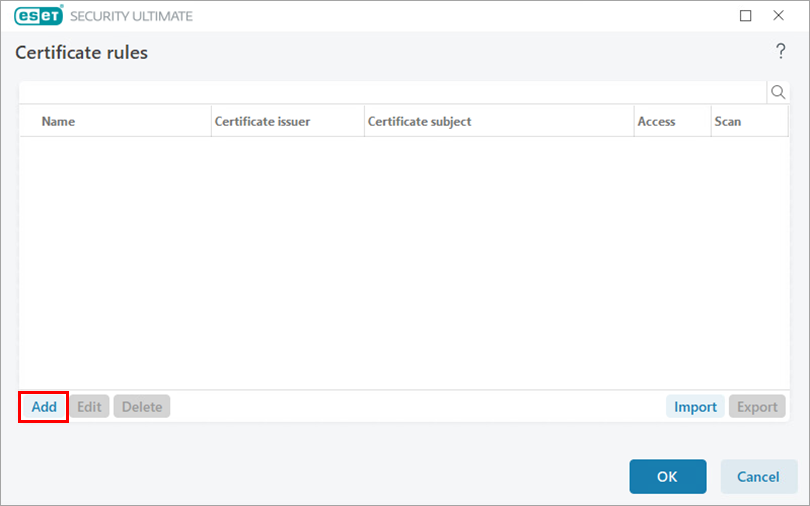
Figure 1-2 Click URL, and in the URL address field, type the server's domain name. Click OK.
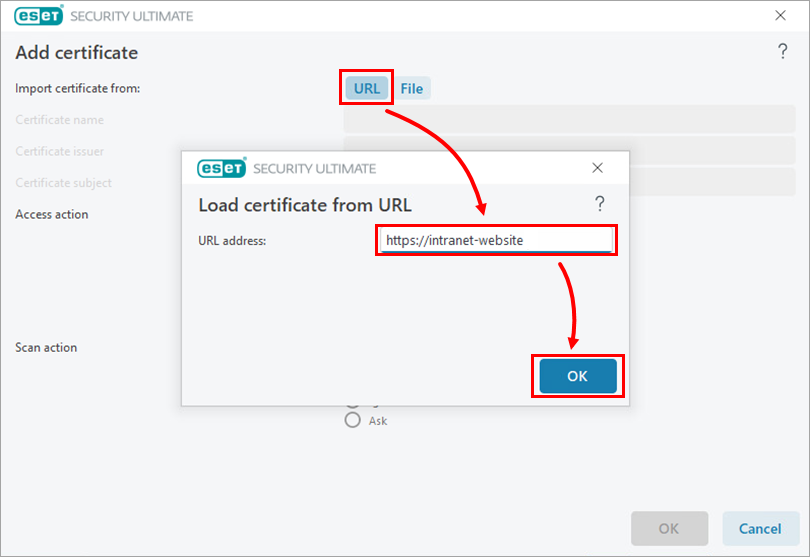
Figure 1-3 Next to Scan action, select Ignore and click OK.
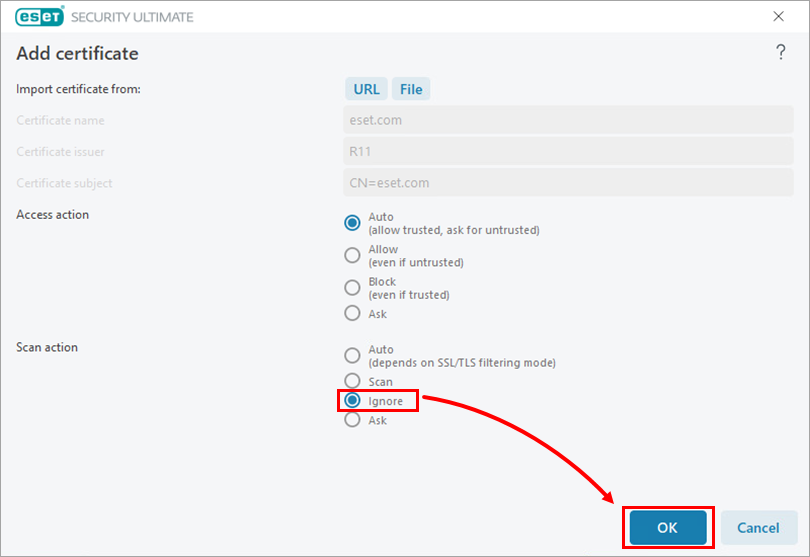
Figure 1-4 Click OK → OK to confirm the configuration change.
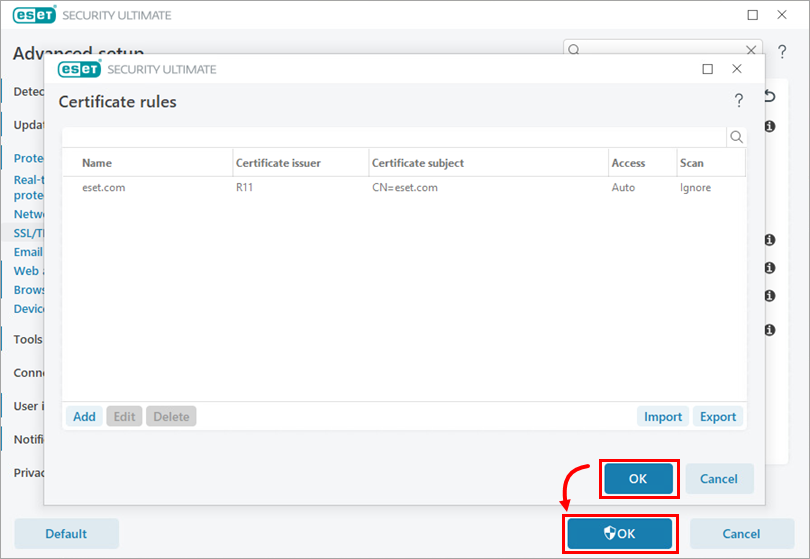
Figure 1-5
If you manage ESET endpoint products remotely using ESET PROTECT, apply these settings as a policy.
Disable the "Extended Protection for Authentication" feature on the server
Disabling this feature will leave your server vulnerable to Man in the Middle attacks and is not recommended. We recommend that you attempt the solution above.
For more information see:
- https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/design/best-practices-for-secure-planning-and-deployment-of-ad-fs ("Utilize extended protection for authentication")
- https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/troubleshooting/ad-fs-tshoot-iwa#channel-binding-token