Issues
Solution
Install ESET Cyber Security version 7
-
Uninstall any previously installed antivirus software on your system.
-
Download version 7 of ESET Cyber Security and double-click the appropriate installer file to begin the installation.
-
Double-click the Install ESET Cyber Security icon.
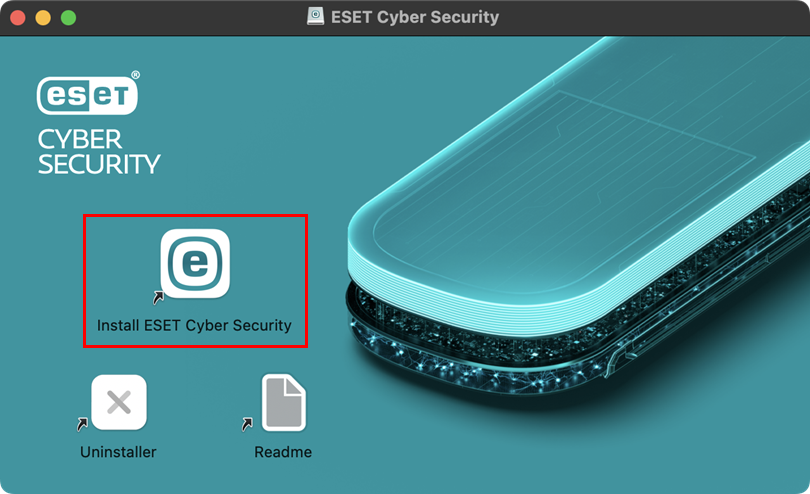
Figure 1-1 -
Click Continue.
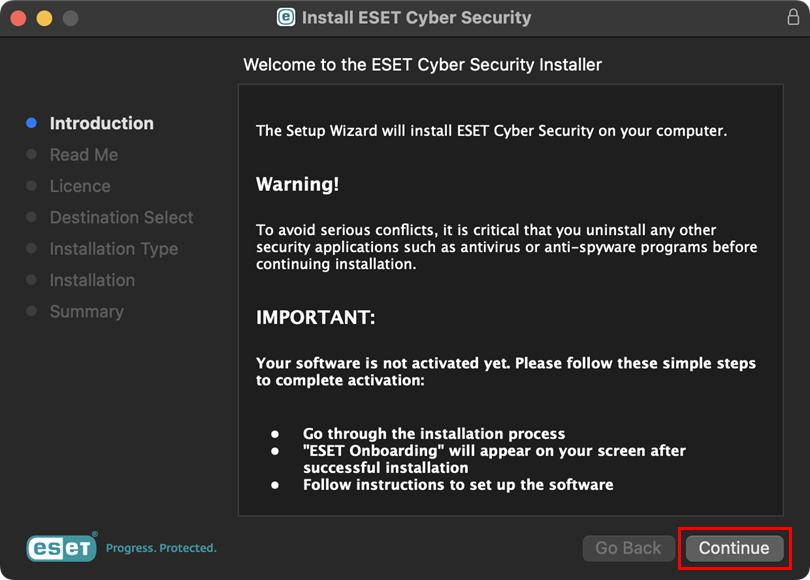
Figure 1-2 -
Click Continue.
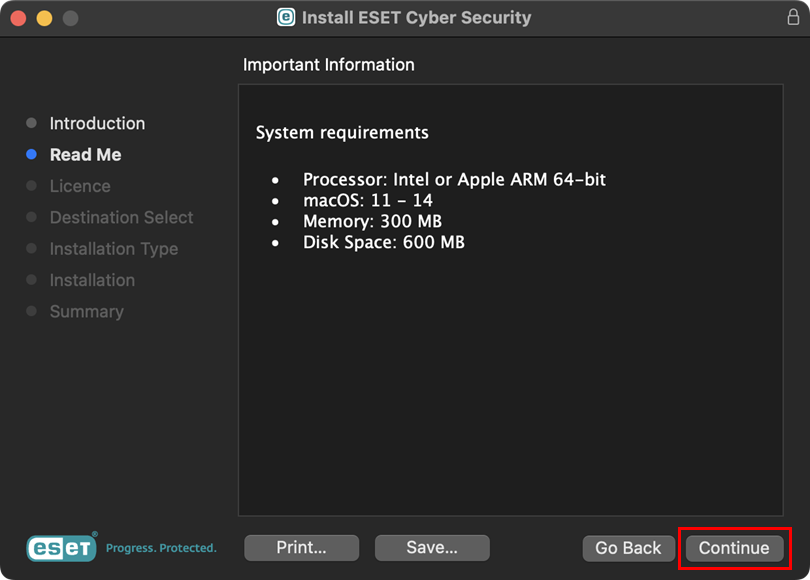
Figure 1-3 -
Click Continue. In the dialog window, click Agree.
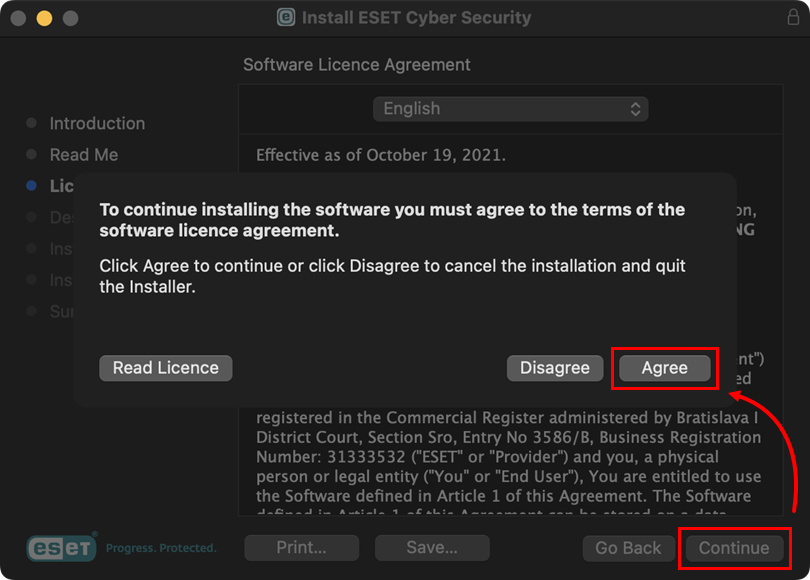
Figure 1-4 -
Select the software installation option and click Continue.
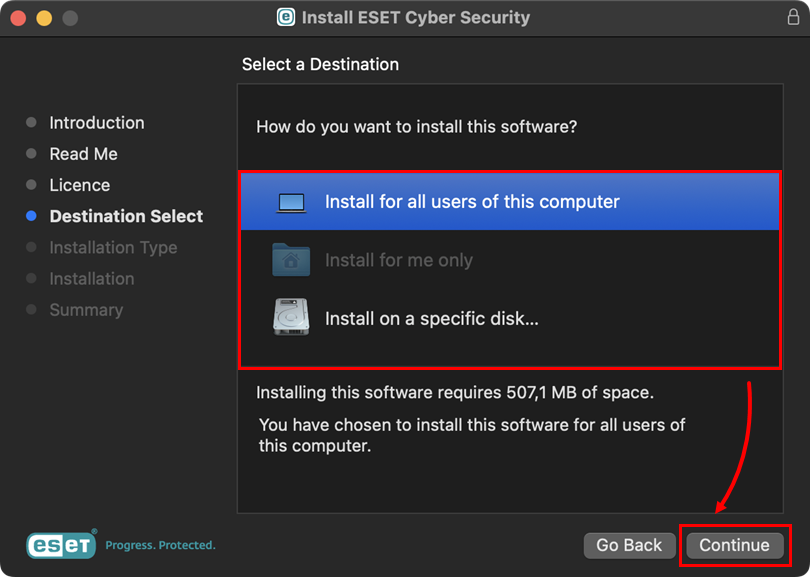
Figure 1-5 -
Click Install.
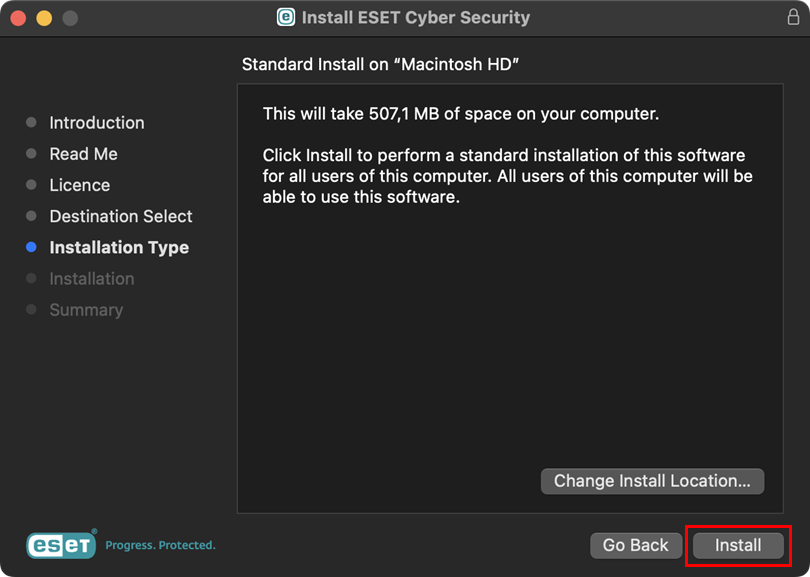
Figure 1-6 -
When prompted, confirm the action by typing your administrator Password or using a Touch ID, and click Install Software.
-
The installation may take a few minutes to complete. When The installation was successful screen displays, click Close.
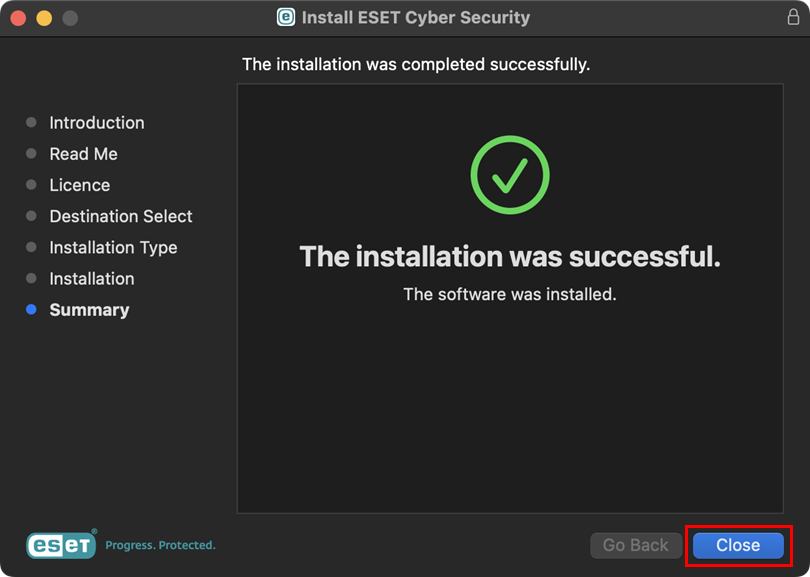
Figure 1-7 -
Click Continue.
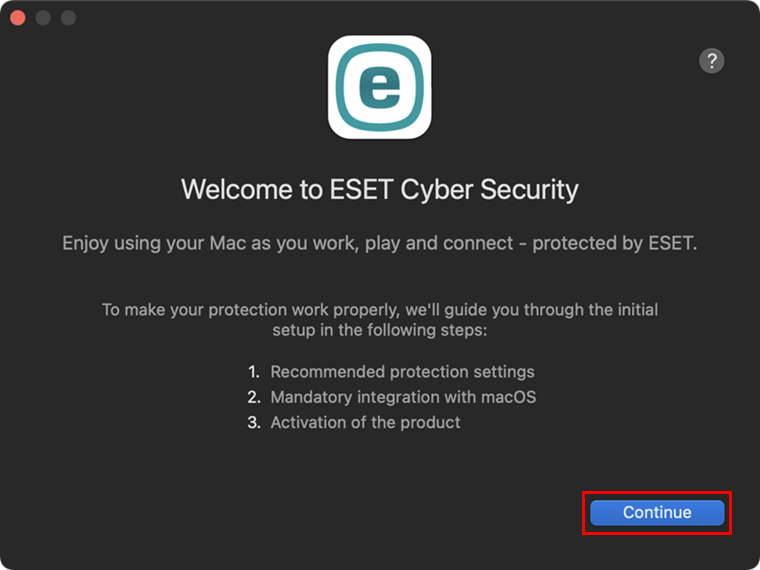
Figure 1-8 -
Click Enable All and Continue.
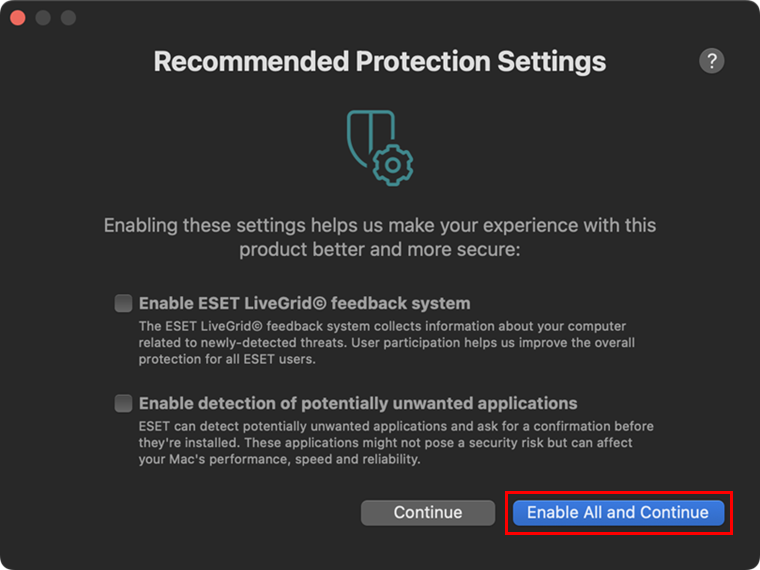
Figure 1-9 -
After the installation, you will receive System Extension Blocked system notification. Click Open System Settings and allow system extensions for your ESET product for Mac. When the system extensions are allowed, click Continue.
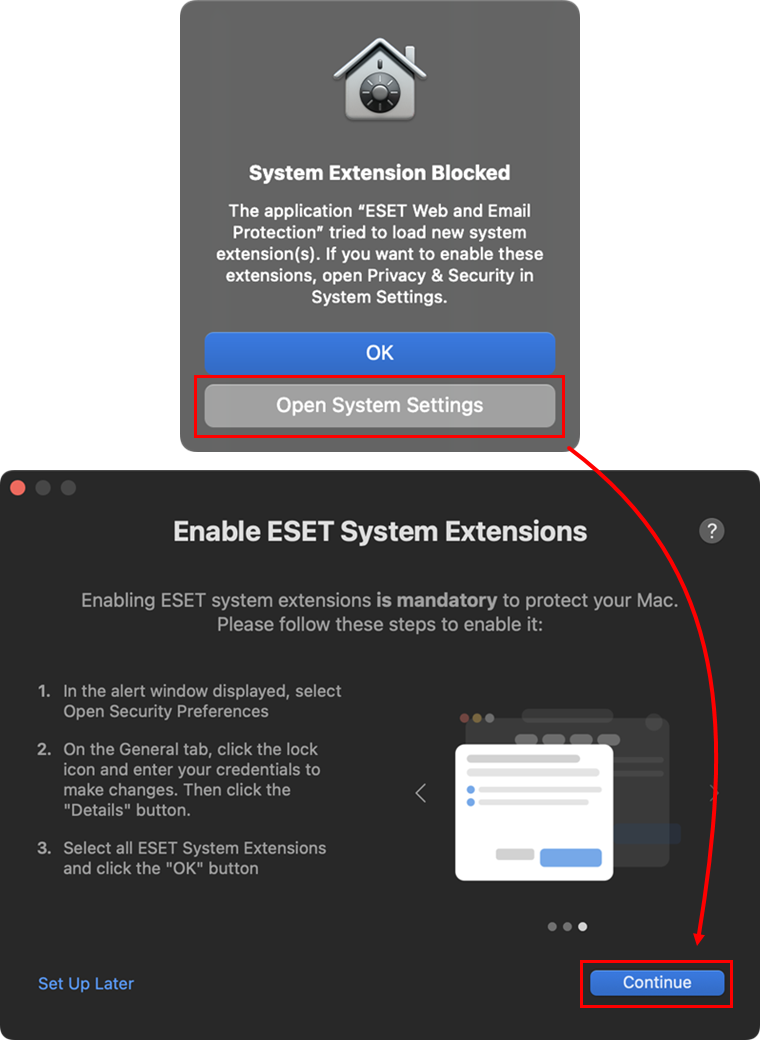
Figure 1-10 -
After allowing system extensions, you must allow your ESET product to add proxy configurations for ESET Web and Email Protection to work. Apple requires this option to increase your protection. Click Allow.
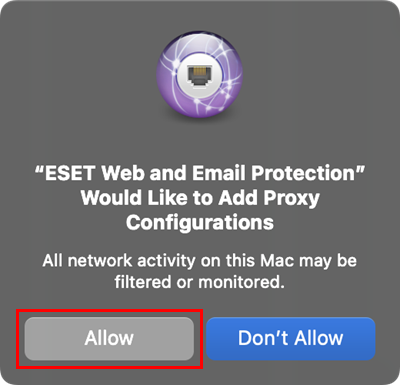
Figure 1-11 -
After adding proxy configurations, you must allow your ESET product access to user-protected data to receive full protection. Click the open System Preferences link and allow full disk access for your ESET product for macOS. When Full disk access is allowed, click Continue.
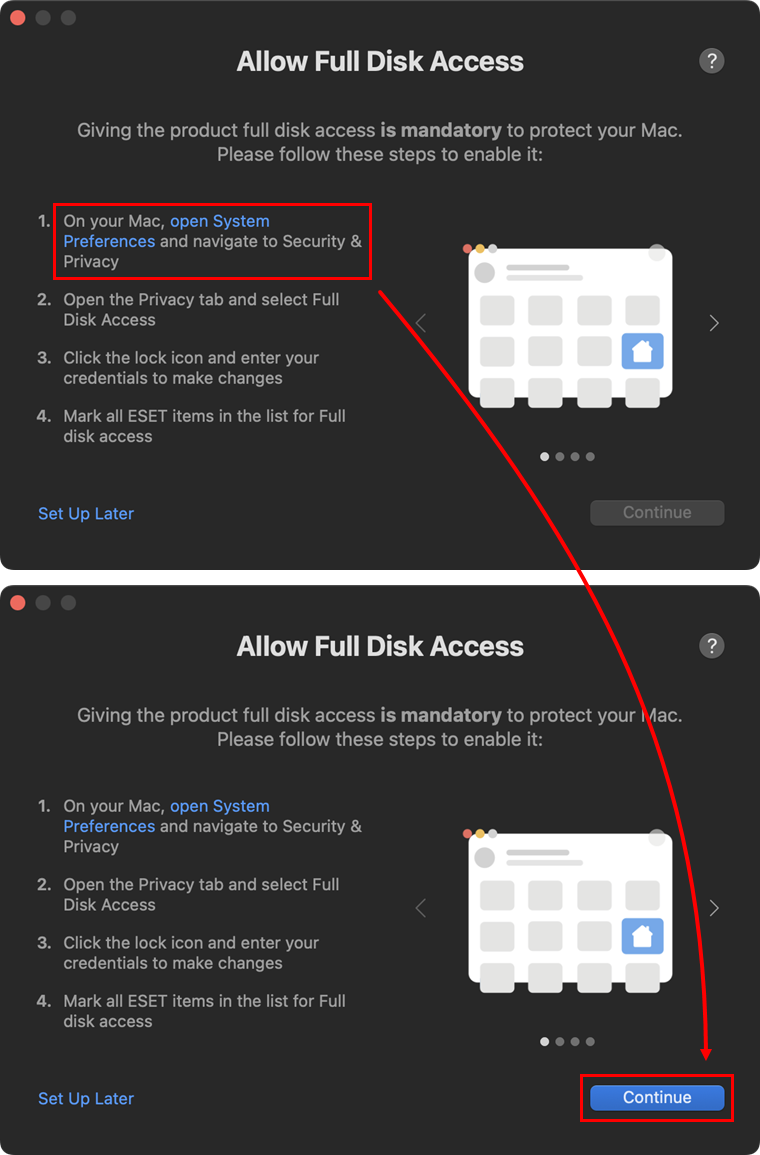
Figure 1-12 -
Click Activate with an Activation Key.
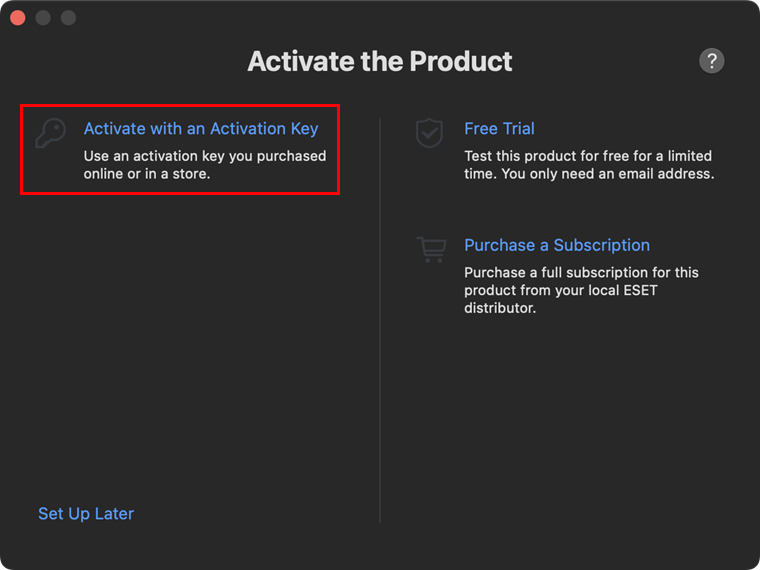
Figure 1-13 -
Type or copy/paste your Activation Key and click Continue.
If you do not have an Activation Key or did not receive an email with subscription information following your purchase, retrieve your subscription information.
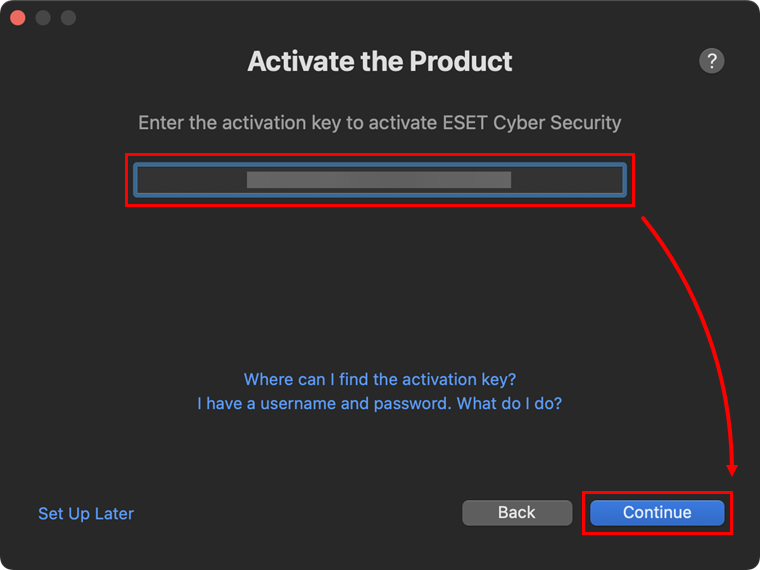
Figure 1-14 -
In the Allow Notification window, click Open System Preferences and click the Allow Notifications toggle to enable it. You can also allow notifications by clicking Allow on the system notification. When the notifications are allowed, click Continue.
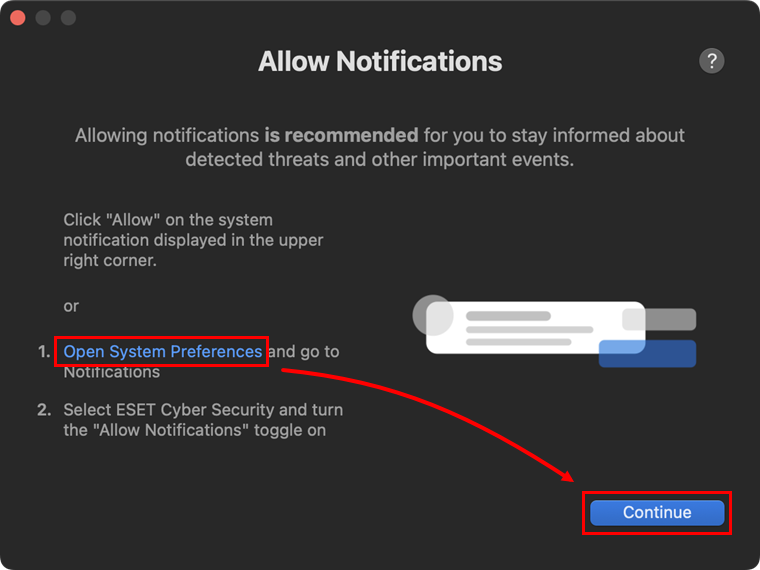
Figure 1-15 -
Click Done.
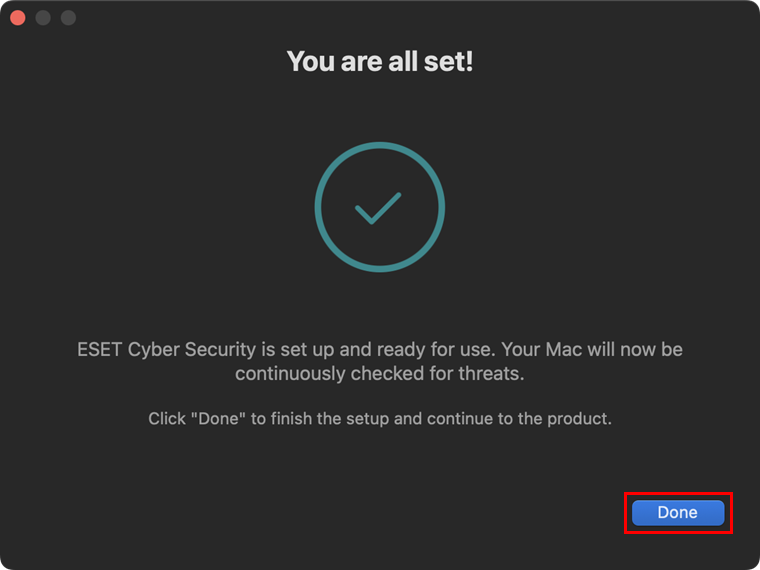
Figure 1-16 -
In the Dock menu, click the ESET icon to view the ESET Cyber Security main program window.
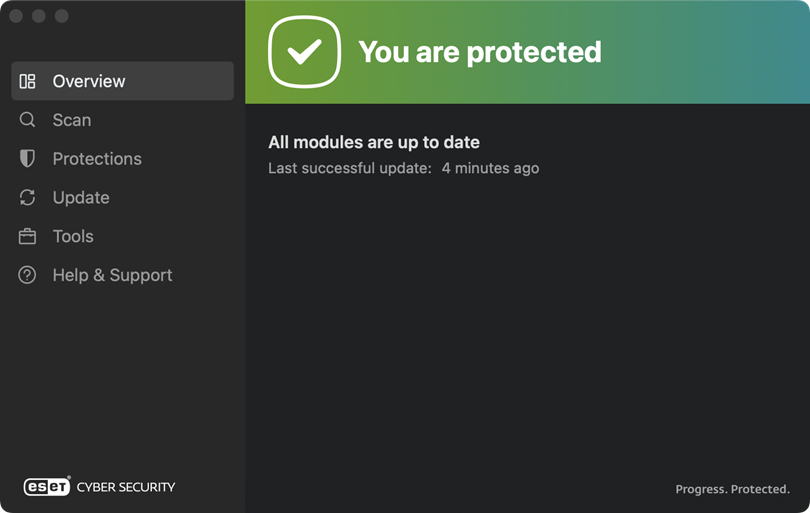
Figure 1-17
Install ESET Cyber Security Pro version 6
-
Uninstall any previously installed antivirus software on your system.
-
Download version 6 of ESET Cyber Security Pro and double-click the appropriate installer file to begin the installation.
-
Double-click the Install icon.
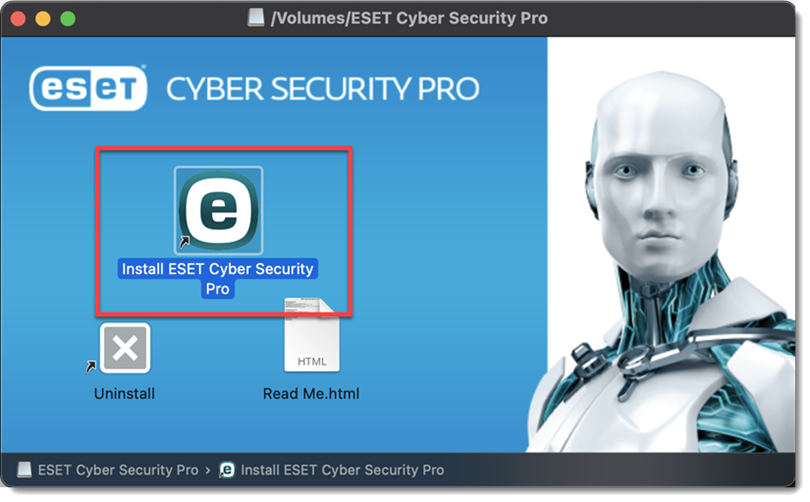
Figure 2-1 -
Click Allow to launch the Installation Wizard.
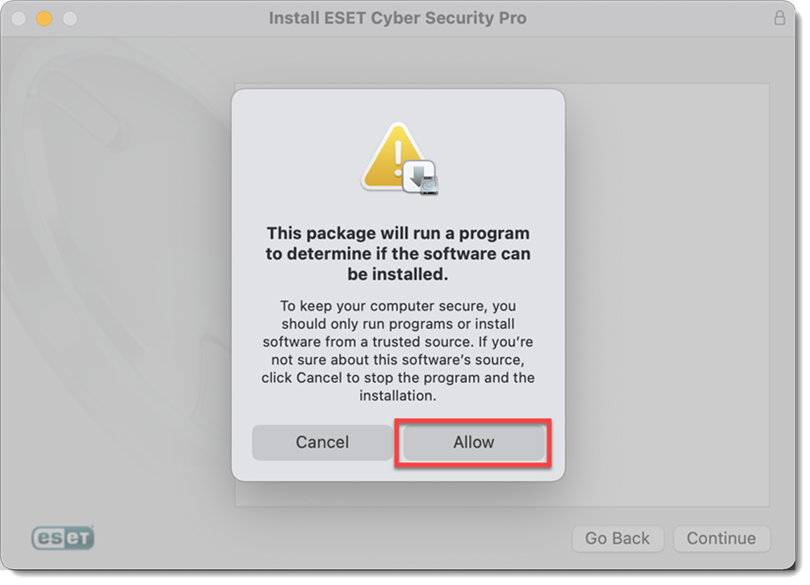
Figure 2-2 -
Click Continue.
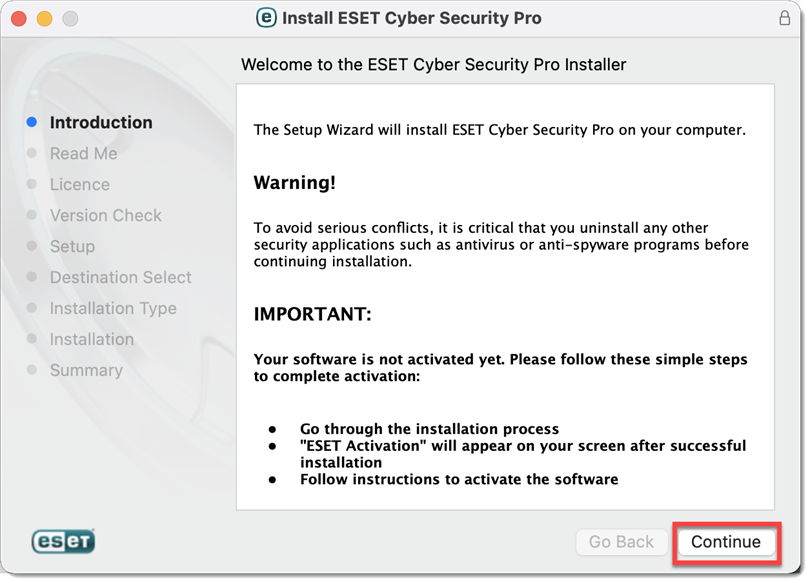
Figure 2-3 -
Click Continue.
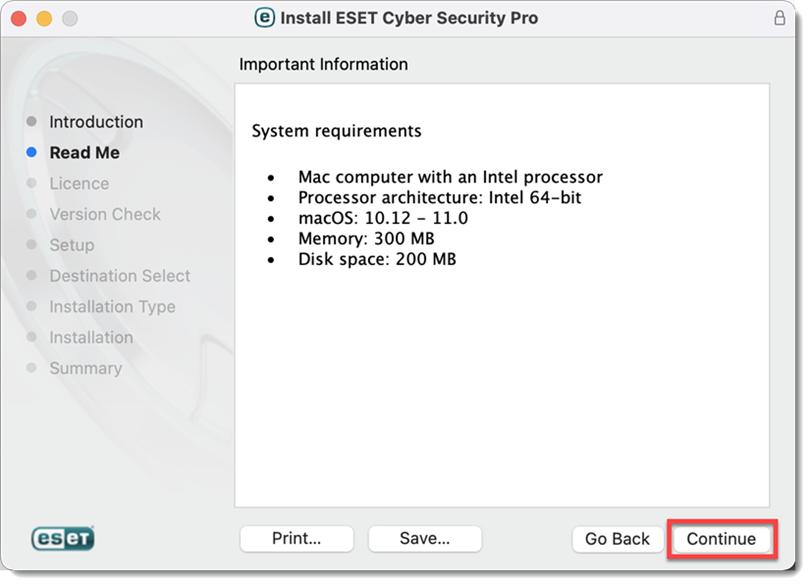
Figure 2-4 -
Click Continue → Agree.
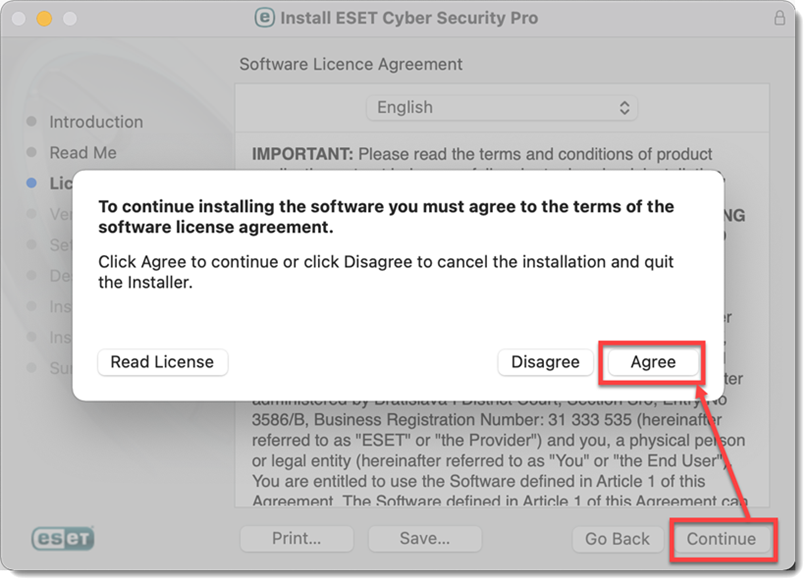
Figure 2-5 -
Click Continue. We recommend you install the latest version if you are notified one is available.
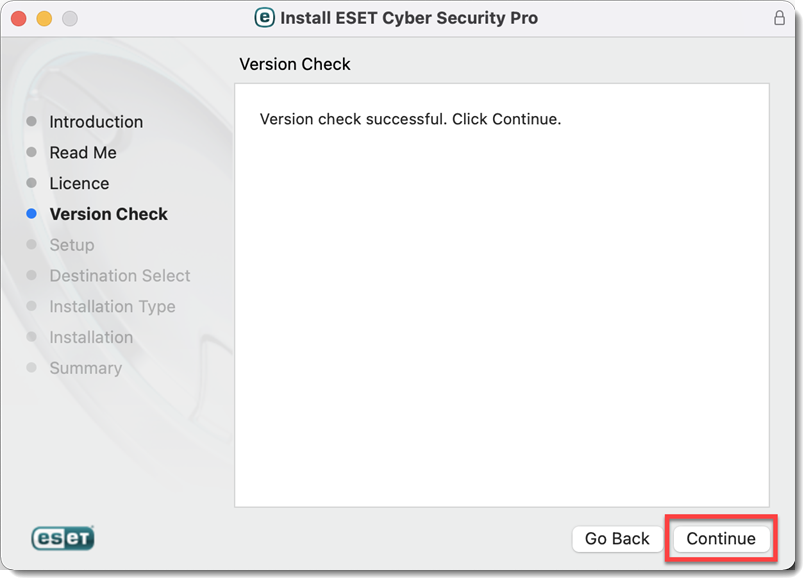
Figure 2-6 -
Select an Installation mode and click Continue.
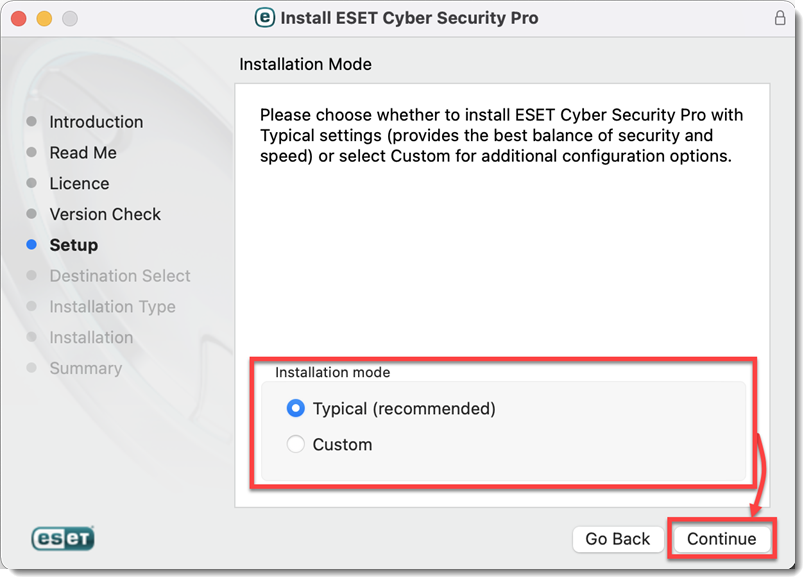
Figure 2-7 -
Select your preference for ESET LiveGrid and click Continue.
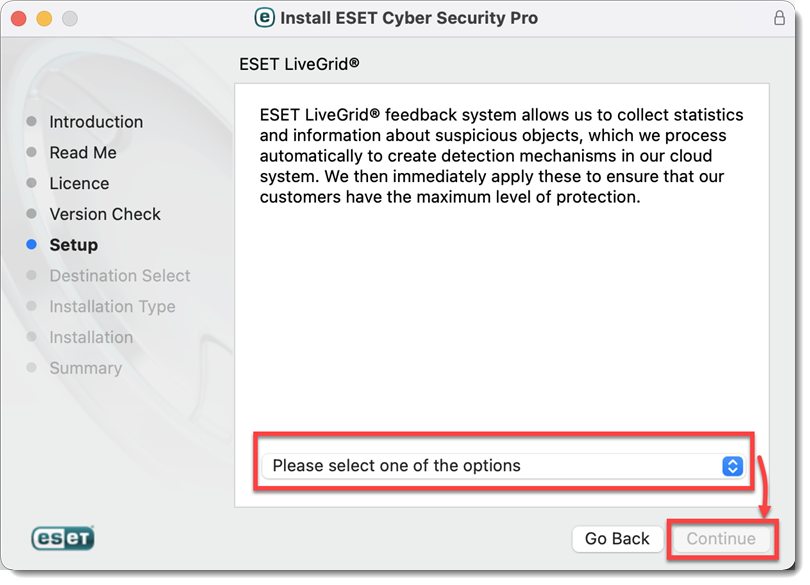
Figure 2-8 -
Select your Potentially Unwanted Applications preference and click Continue.
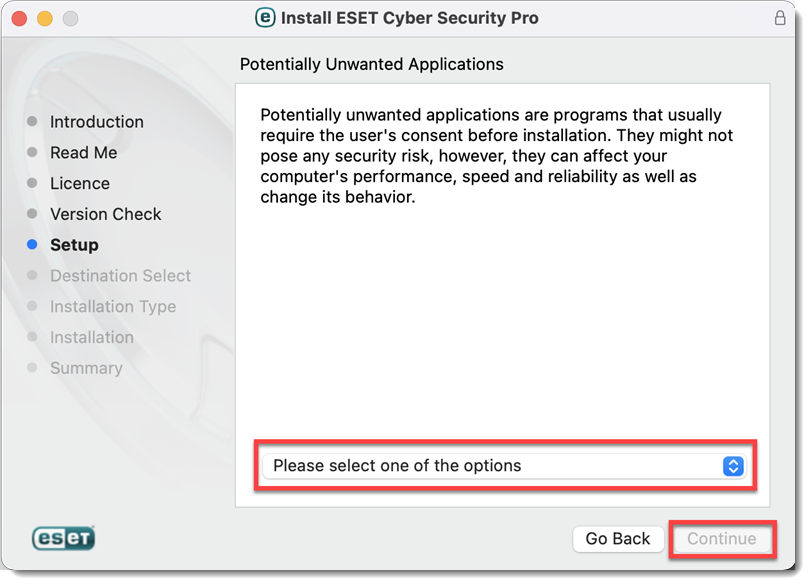
Figure 2-9 -
Click Install.
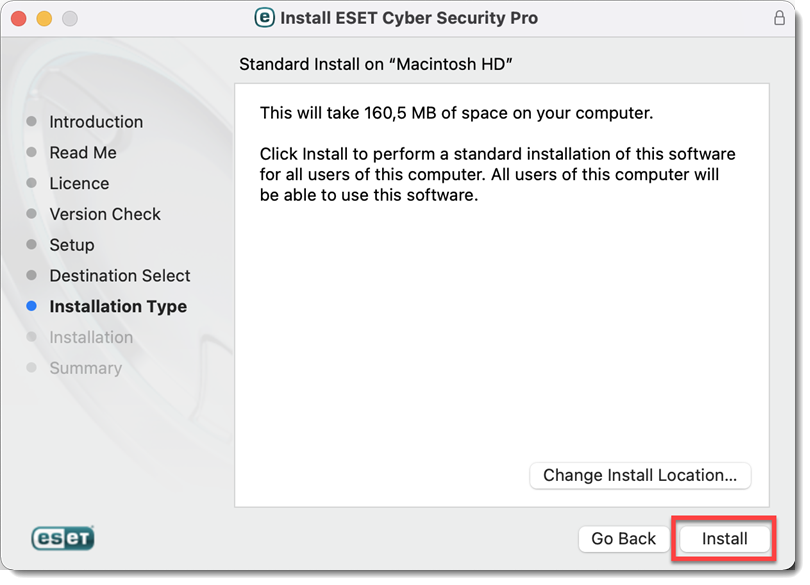
Figure 2-10 -
When prompted, type your administrator Name and Password and click Install Software.
-
The installation may take a few minutes to complete. When The installation was successful screen displays, click Close.
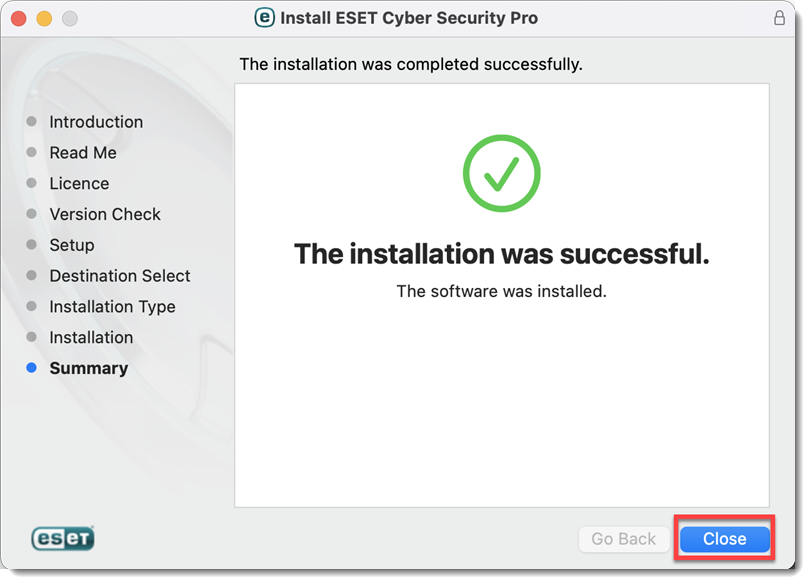
Figure 2-11 -
After the installation, you will receive System Extension Blocked system notification. Allow system extensions for your ESET product for Mac.
-
After allowing system extensions, you need to allow your ESET product to add proxy configurations for Web access protection to work. Click Allow. This option is required by Apple to increase your protection.
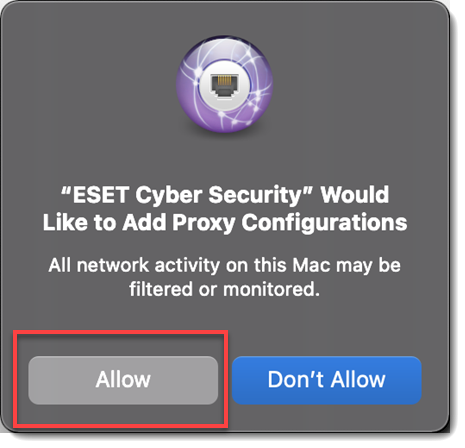
Figure 2-12 -
After allowing system extensions, you will receive Your computer is not protected notification from your ESET product. You need to allow your ESET product access to user protected data to receive full protection. Allow full disk access for your ESET product for macOS.
-
In the License Key field, type or copy/paste your License Key and click Activate. If the activation window does not open automatically, in the menu bar, click the
 or
or  icon. Select Open ESET Cyber Security or ESET Cyber Security Pro and click Activate.
icon. Select Open ESET Cyber Security or ESET Cyber Security Pro and click Activate.If you do not have a License Key or did not receive an email with license information following your purchase, you can retrieve your license information.
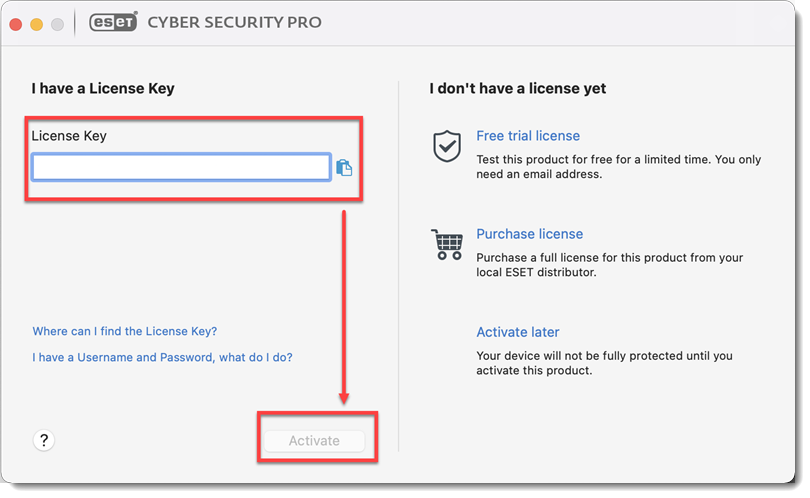
Figure 2-14 -
If your credentials were entered correctly, you will see the Activation was successful screen. Click Done to complete your activation. Your product will now automatically begin downloading the latest modules update.
-
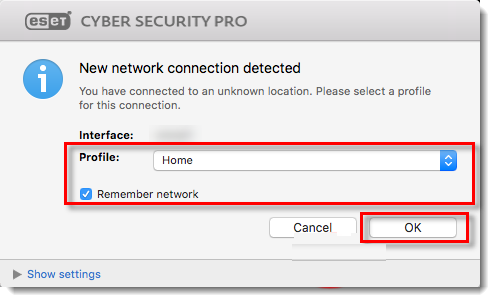
In the New network connection detected window, select the check box next to Remember network, select your preferred Profile from the drop-down menu and click OK.
If you are performing this installation in an office or home environment on a secure network, select Home or Office. Only select Public if you are traveling with your client computer and ESET Cyber Security Pro detects a new network.