Issue
- Configure additional antispam settings in ESET Mail Security for Microsoft Exchange Server
- Create a policy in ESET PROTECT with additional antispam settings for ESET Mail Security for Microsoft Exchange Server to protect against ransomware malware (file coder)
- Manually create an ESET PROTECT Policy/configure the settings in ESET Mail Security for Microsoft Exchange Server
- Download and import the ESET PROTECT Policy
- Ransomware dropper filtering example
Details
Click to expand
Using the default Antispam rules, incoming emails are already filtered on the mail server. This ensures that the attachment containing the malicious dropper will not be delivered to the end user's mailbox, and the ransomware cannot execute.
To further help prevent ransomware malware on your Microsoft Exchange server, create the following rules in the latest ESET Mail Security for Microsoft Exchange Server, or create and apply an ESET PROTECT Policy.
Solution
Manually create an ESET PROTECT Policy/configure the settings in ESET Mail Security for Microsoft Exchange Server
- Open the ESET PROTECT or ESET PROTECT On-Prem. In the Quick Links drop-down menu, click Create New Policy.
ESET Mail Security for Microsoft Exchange Server users:
Open the main program window of your ESET Windows product, press the F5 key to access Advanced setup and proceed to Step 3.
-
Click Settings, and in the Select product drop-down menu, select ESET Mail Security for Microsoft Exchange Server (V6+).
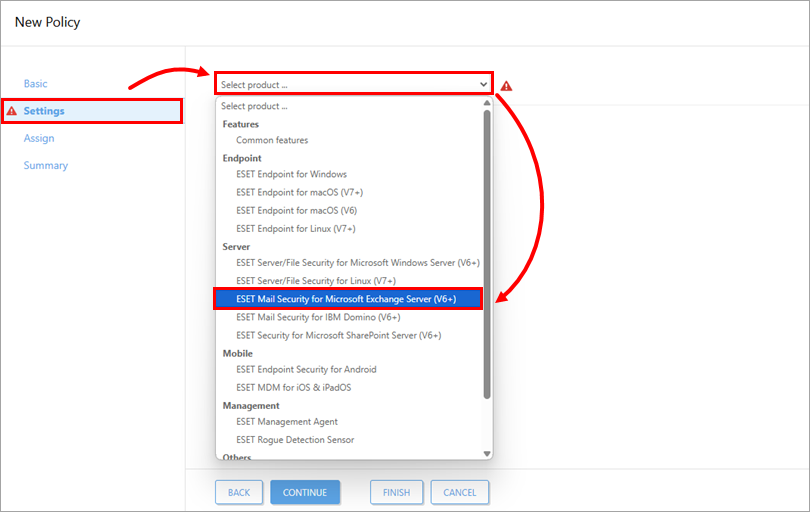
Figure 1-1
-
Click Mail Transport Protection. Expand Mail Transport Protection, and click Edit next to Mail transport protection rules.
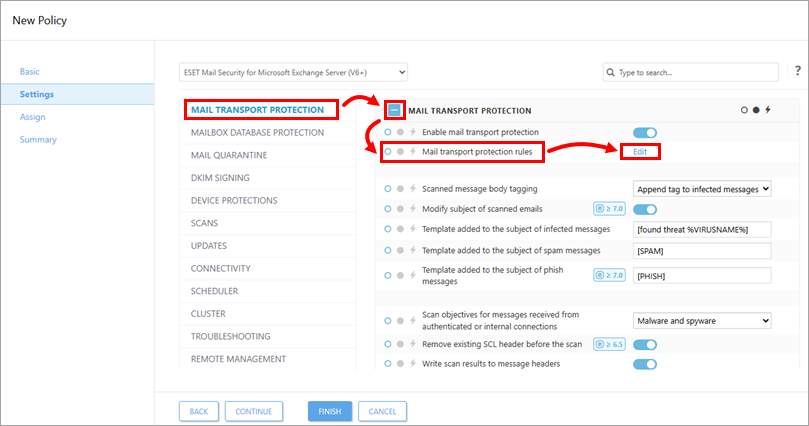
Figure 1-2 -
Click Add to create a rule to quarantine common ransomware droppers.
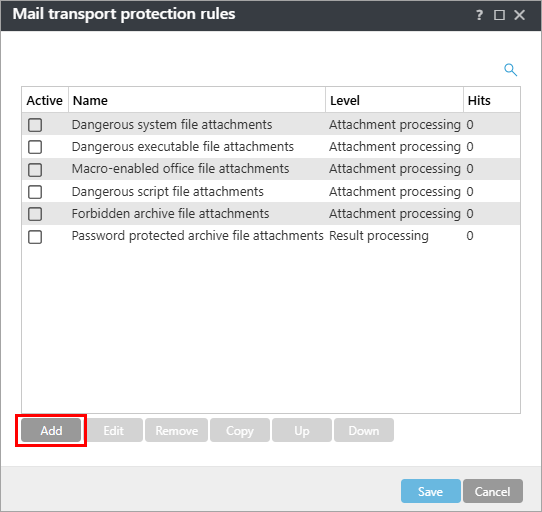
Figure 1-3 -
Type Ransomware droppers into the Name field. Under the Condition type section, click Add.
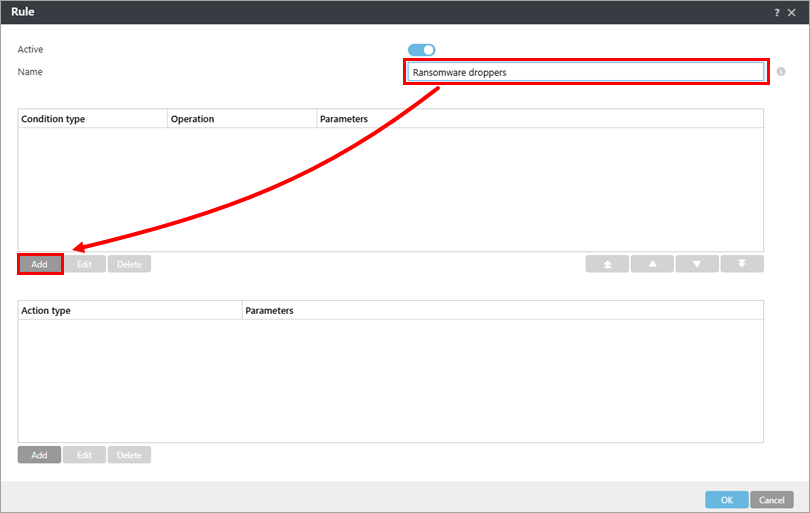
Figure 1-4 -
From the Type drop-down menu, select Attachment name and click Add.
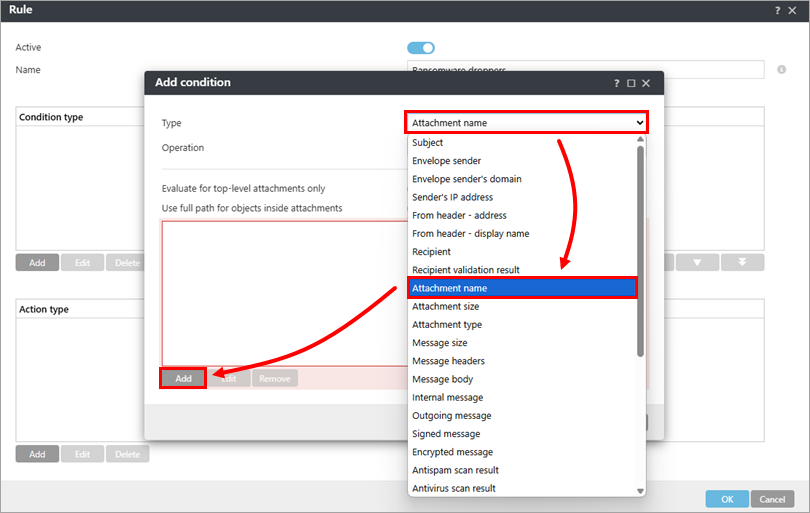
Figure 1-5 -
Click Enter multiple values.
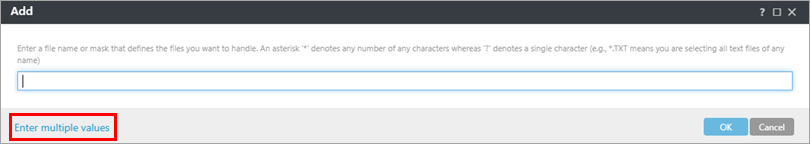
Figure 1-6 -
Type the following file names, pressing Return or Enter after each one and click OK → OK.
- *.js/li>
- *.hta
- *.doc
- *.docm
- *.xls
- *.xlsm
- *.ppt
- *.pptm
- *.vbs
- *.bat
- *.wsf
- *.7z
- *.zip
- *.rar
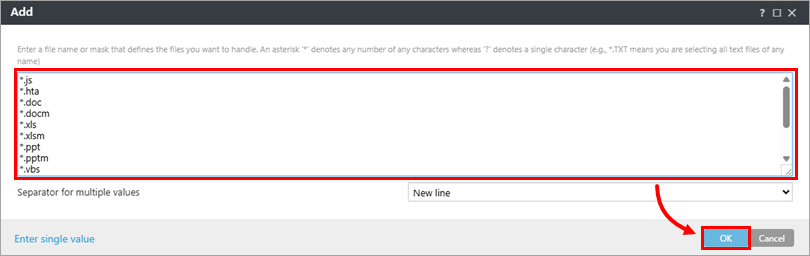
Figure 1-7
-
Click Add under Action type, and in the Type drop-down menu, select your preferred action. In this example, we have selected Quarantine message. Click OK → OK.
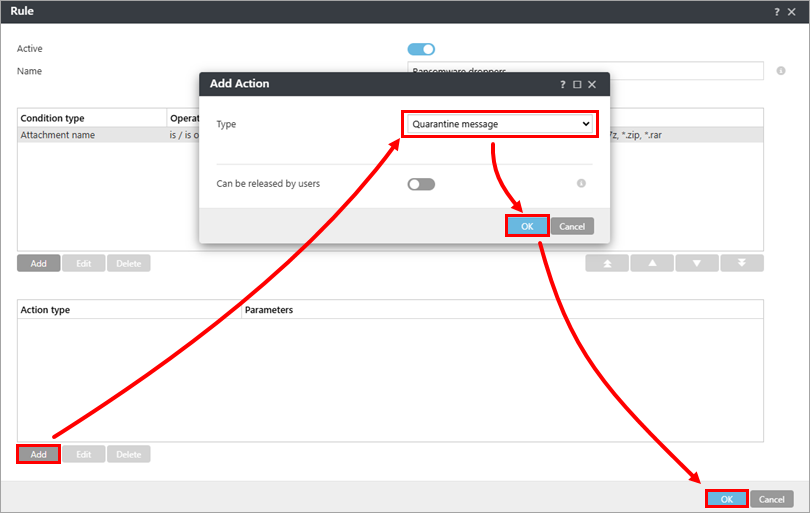
Figure 1-8
-
Select the check box next to Dangerous executable file attachments and click Edit.
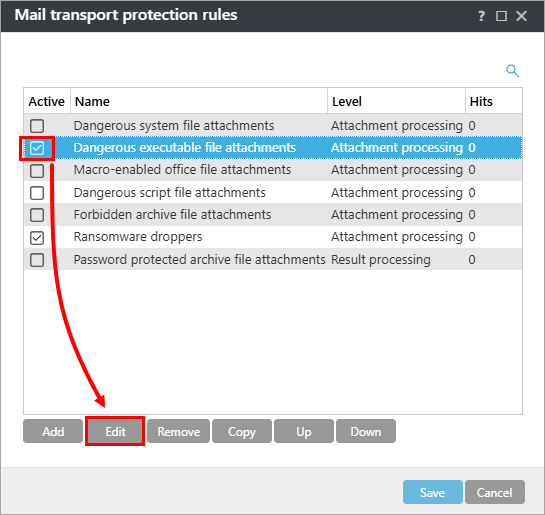
Figure 1-9 -
Select the entry under Condition type and click Edit.
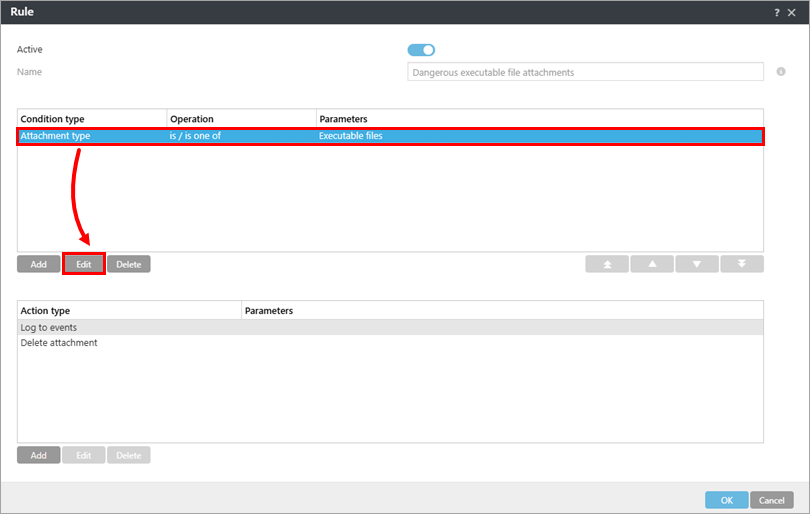
Figure 1-10 -
Click the plus icon
 to expand Executable files, select the check box next to each file type you want to allow in your system environment (selecting the check box will deselect the item from being deleted by the Action type that you chose in step 10 above) and click OK → OK.
to expand Executable files, select the check box next to each file type you want to allow in your system environment (selecting the check box will deselect the item from being deleted by the Action type that you chose in step 10 above) and click OK → OK.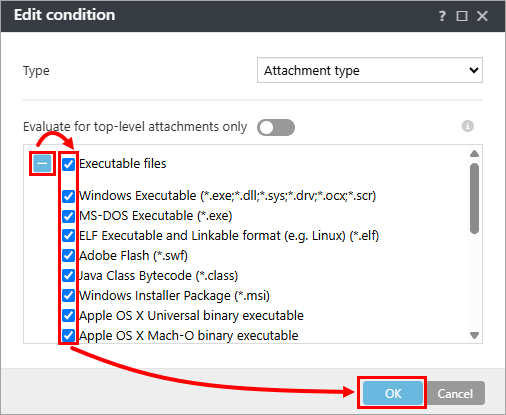
Figure 1-11
The following executable file attachments are processed. If your network environment requires using any of these file formats, you can modify which file formats are blocked. Most businesses may want to deselect the .exe and .msi file formats.
-
- Windows Executable (*.exe, *.dll,* .sys*, *.drv; *.ocx, *.scr)
- MS-DOS Executable (*.exe)
- ELF Executable and Linkable format (for example, Linux) (*.elf)
- Adobe Flash (*.swf)
- Java Class Bytecode (*.class)
- Windows Installer Package (*.msi)
- Apple OS X Universal binary executable
- Apple OS X Mach-O binary executable
- Android executable (*.dex)
-
In the Mail transport protection rules window, click Save. Expand Assign to assign the policy to a client or group; otherwise, click Finish in the New Policy – Settings screen. If assigned, your policy settings will be applied to the target groups or client computers when they check in to ESET PROTECT.
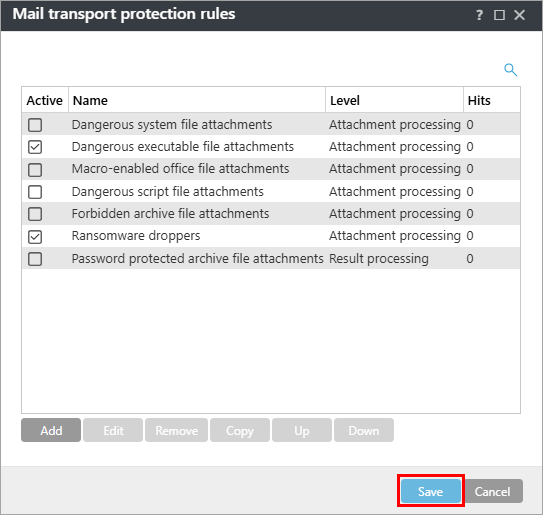
Figure 1-12
ESET Mail Security for Microsoft Exchange Server users:
If you use ESET Mail Security for Microsoft Exchange Server without remote management, click OK → OK.
Download and import the ESET PROTECT Policy
The ESET PROTECT Policy for ESET Mail Security for Microsoft Exchange Server with additional Antispam settings to protect against ransomware malware (file coder) can be downloaded and imported from the link below.
The ESET PROTECT Policy is available only for the latest version of ESET products. Compatibility with earlier versions cannot be guaranteed.
-
Download the Additional Ransomware Protection ESET PROTECT Policy.
-
Open the ESET PROTECT or ESET PROTECT On-Prem. In the main menu.
-
Click Configuration → Actions → Import.
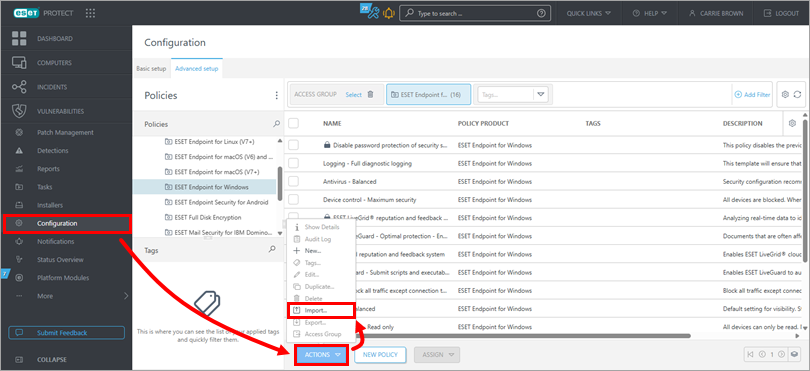
Figure 2-1 -
Click Choose file to upload, select the downloaded policy and click Import.
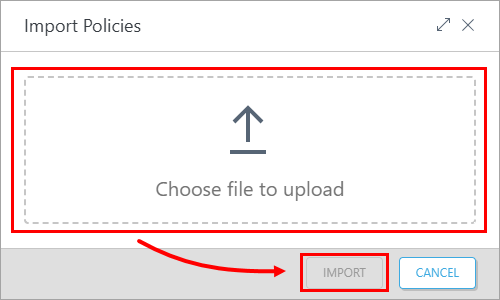
Figure 2-2 -
Assign the policy to a client or assign the policy to a group. Policy settings will be applied to the target groups or client computers when they check in to ESET PROTECT.
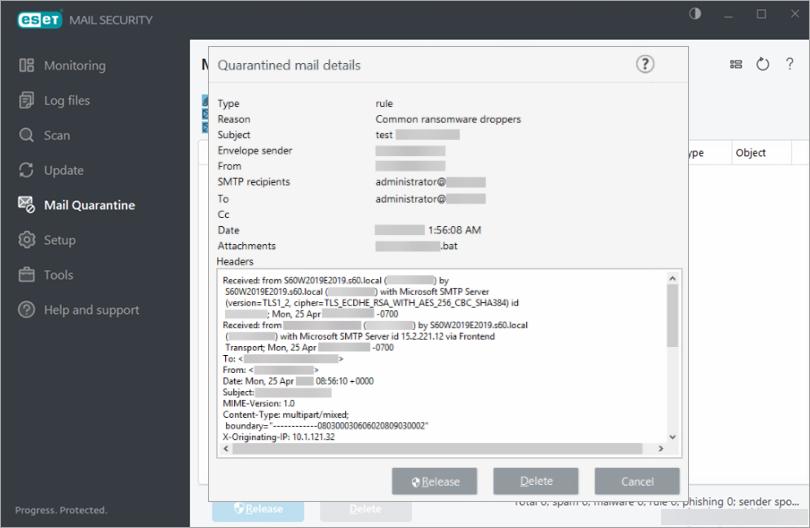
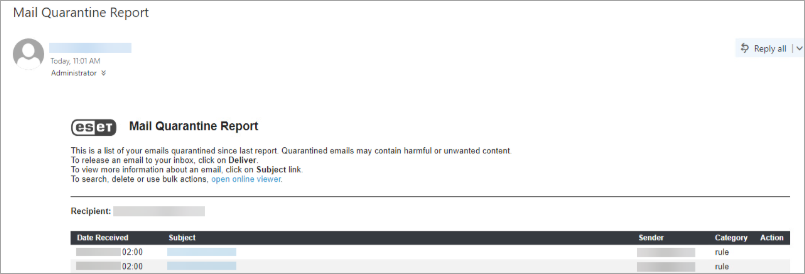
Ransomware dropper filtering example
The following is an example of the Ransomware dropper policy filtering a ransomware dropper, along with a corresponding mail quarantine report: