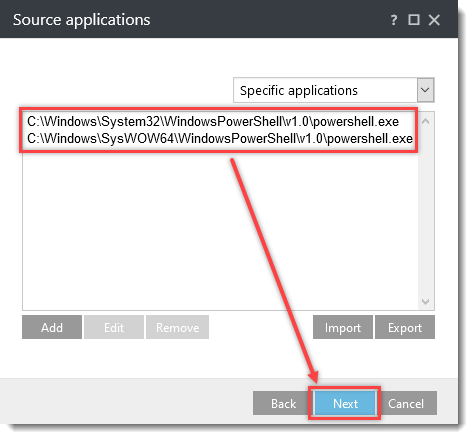
Issue
- You want to configure additional HIPS rules in the following ESET business products for Windows or create a policy in ESET PROTECT or ESET PROTECT On-Prem with additional HIPS settings to protect against ransomware malware (filecoder)
- ESET Endpoint Security
- ESET Endpoint Antivirus
- ESET Mail Security for Microsoft Exchange Server
- ESET File Security for Microsoft Windows Server
- Manually create an ESET PROTECT Policy/configure the settings in ESET business products
- Download and import the ESET PROTECT Policy
Click an image to open the ESET Knowledgebase article for anti-ransomware best practices and additional product configurations:
Details
Click to expand
ESET's Host-based Intrusion Prevention System (HIPS) is included in ESET Endpoint Security, ESET Endpoint Antivirus, ESET Mail Security for Microsoft Exchange Server, and ESET File Security for Microsoft Windows Server. HIPS monitors system activity and uses a pre-defined set of rules to recognize suspicious system behavior.
When this type of activity is identified, the HIPS self-defense mechanism stops the offending program or process from carrying out a potentially harmful activity. By prohibiting the standard execution of JavaScript and other scripts, ransomware cannot download or execute. To further help prevent ransomware malware on your Windows systems, create the following rules in the latest ESET business products with HIPS, or create and apply an ESET PROTECT Policy.
Solution
Manually create an ESET PROTECT Policy/configure the settings in ESET business products
- Open the ESET PROTECT or ESET PROTECT On-Prem. In the Quick Links drop-down menu, click Create New Policy....
If you are using an ESET business product without remote management, open the main program window of your ESET Windows product and press the F5 key to access Advanced setup. Proceed to step 3.
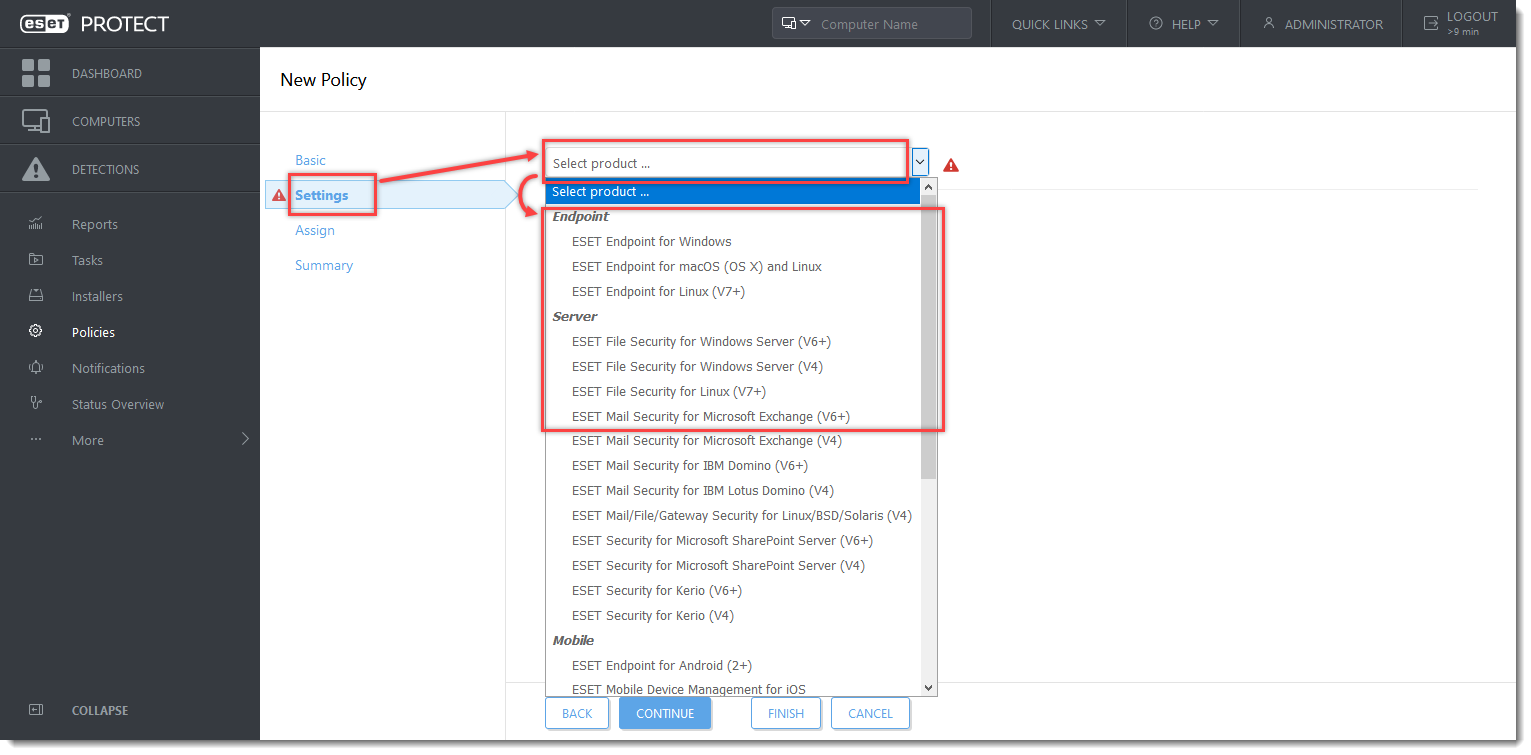
- Click Settings, and in the Select product... drop-down menu, select one of the following ESET business products with HIPS:
-
- ESET Endpoint for Windows.
- ESET File Security for Windows Server (V6+).
- ESET Mail Security for Microsoft Exchange (V6+).
Click the image to view larger in the new window
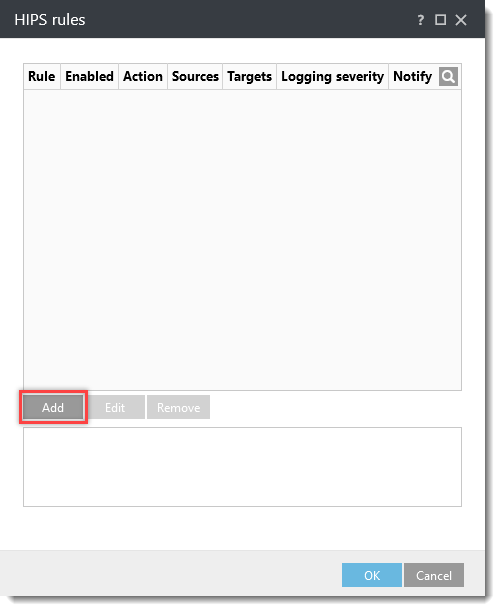
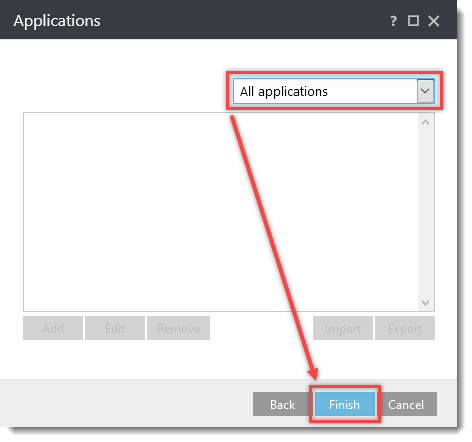
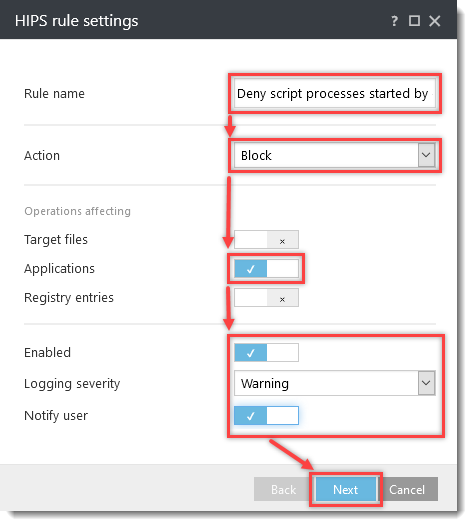
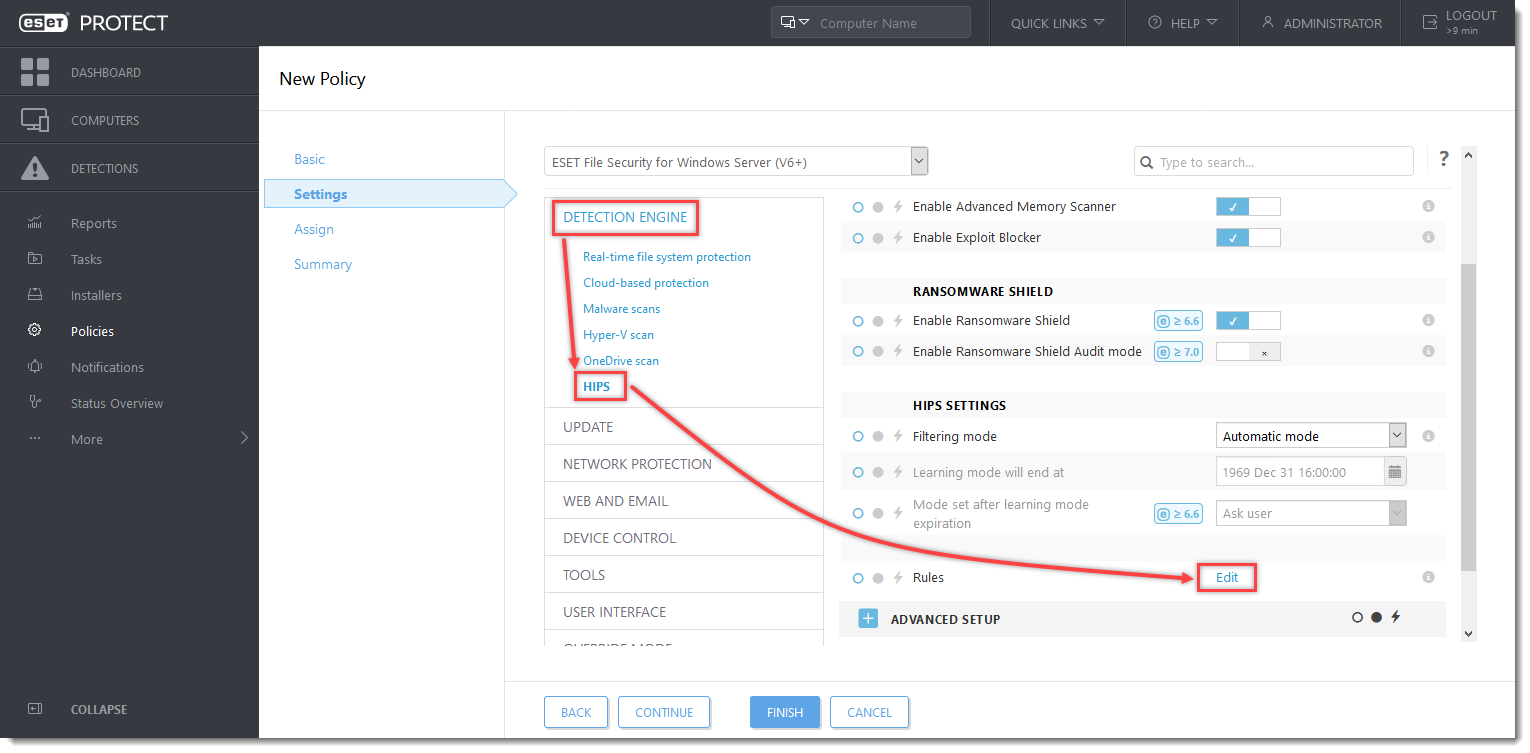
- Click Detection Engine (Computer in ESET Mail Security for Microsoft Exchange Server) → HIPS. Click Edit next to Rules.
Click the image to view larger in the new window
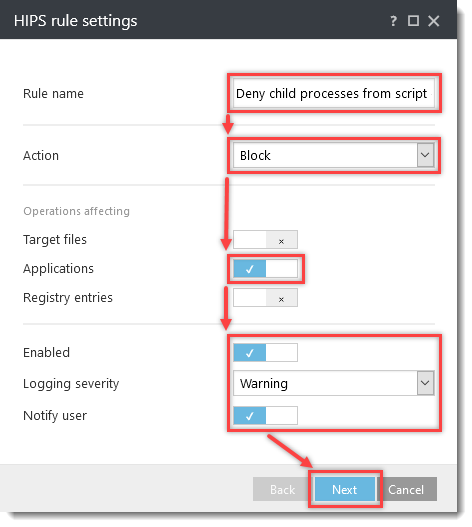
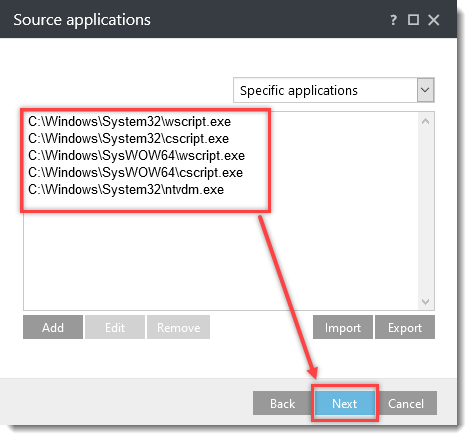
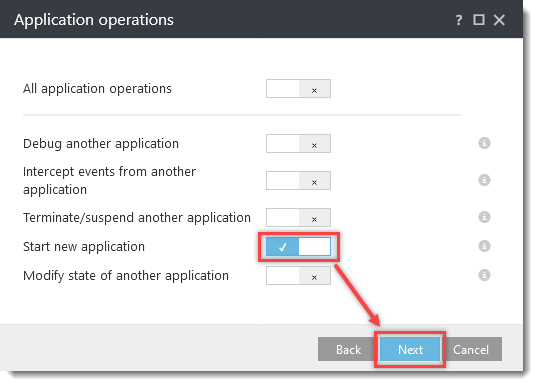
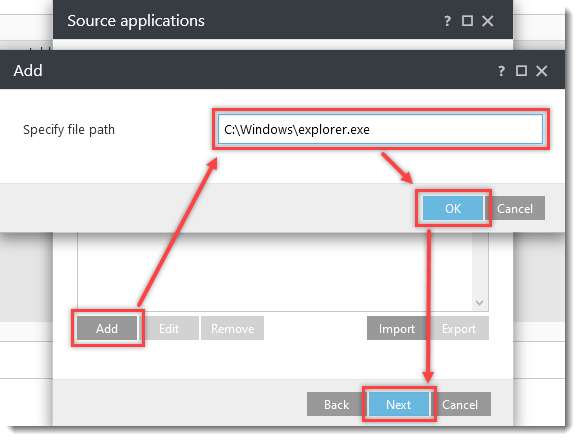
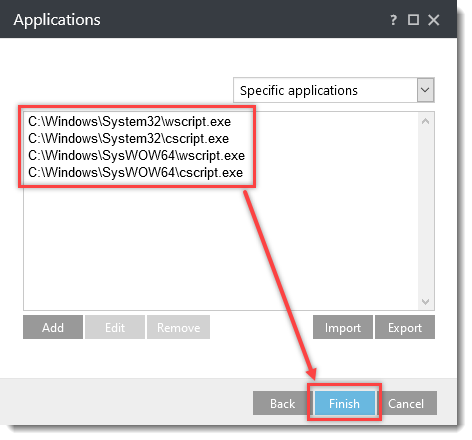
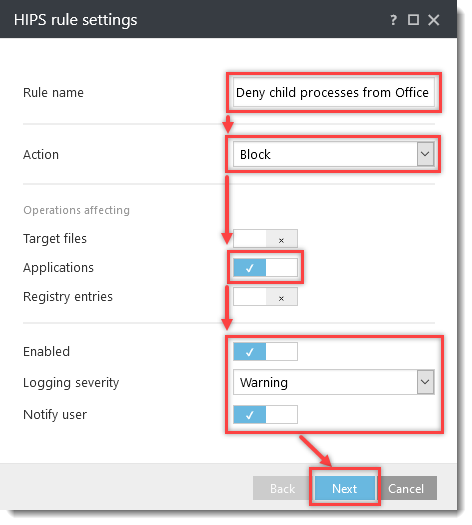
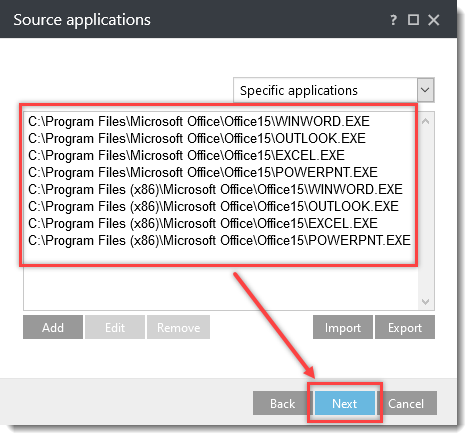
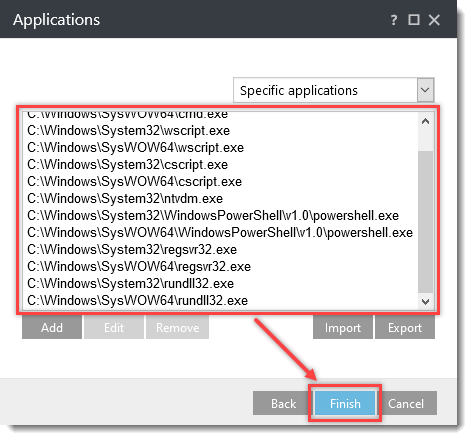
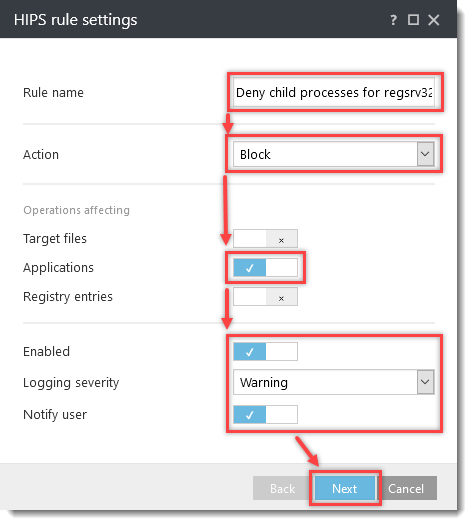
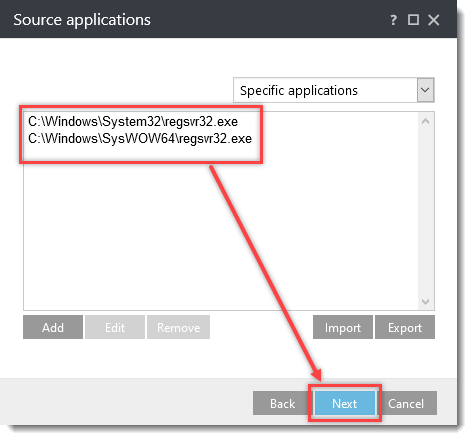
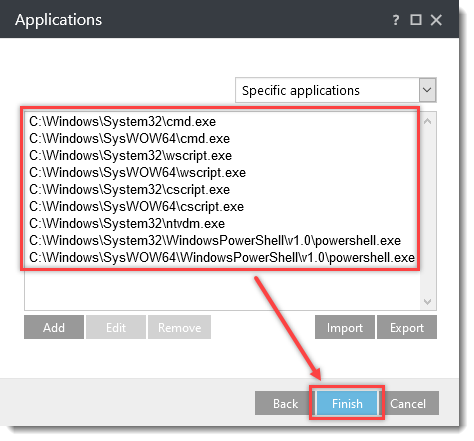
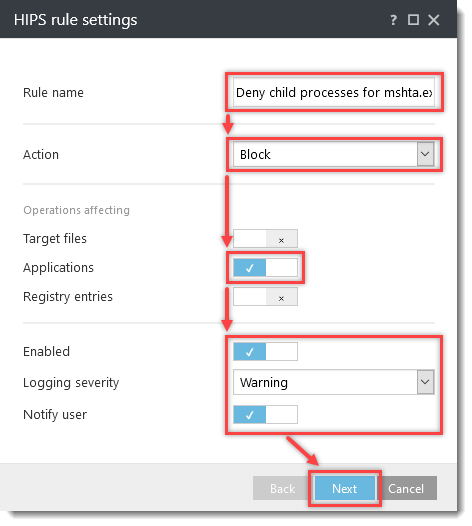
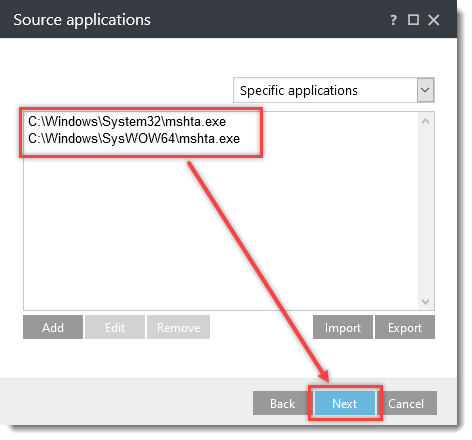
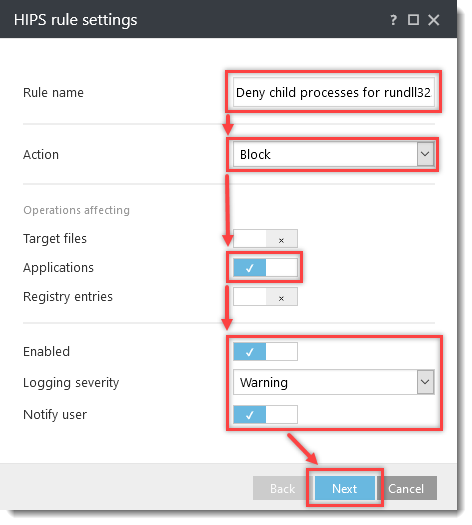
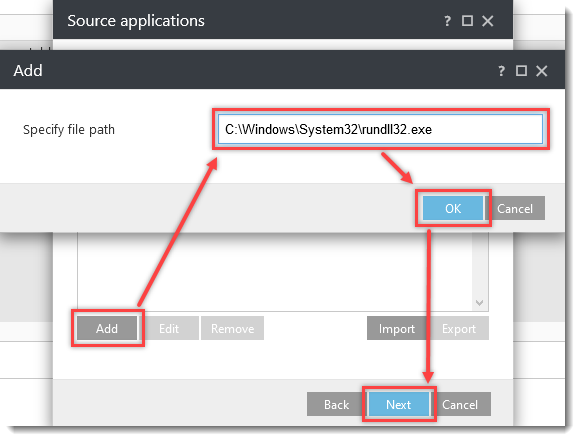
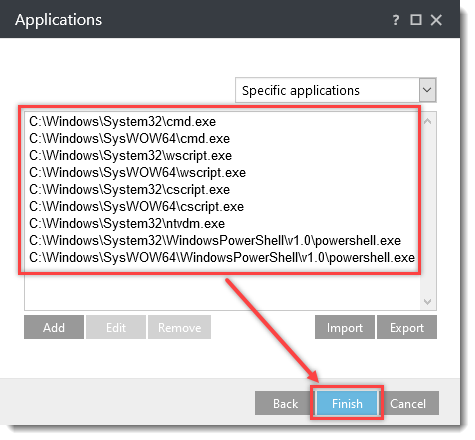
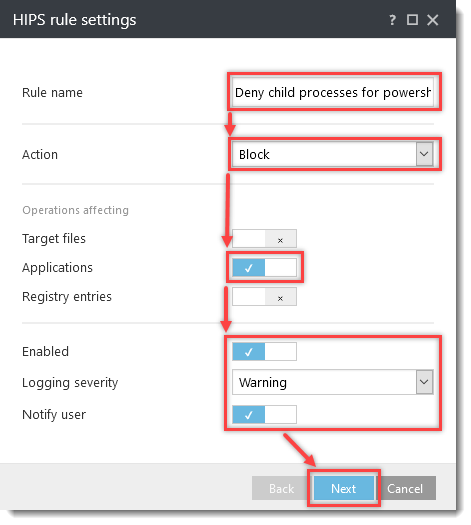
Click the option (I. to VII.) to expand each section below to create the HIPS rules for the suggested processes.
Download and import the ESET PROTECT Policy
The ESET PROTECT Policy for ESET business products with additional HIPS settings to protect against ransomware malware (filecoder) can be downloaded and imported from the links below. The ESET PROTECT Policy is available only for the latest version of ESET products. Compatibility with earlier versions cannot be guaranteed.
-
Download the Additional HIPS Protection ESET PROTECT Policy for:
-
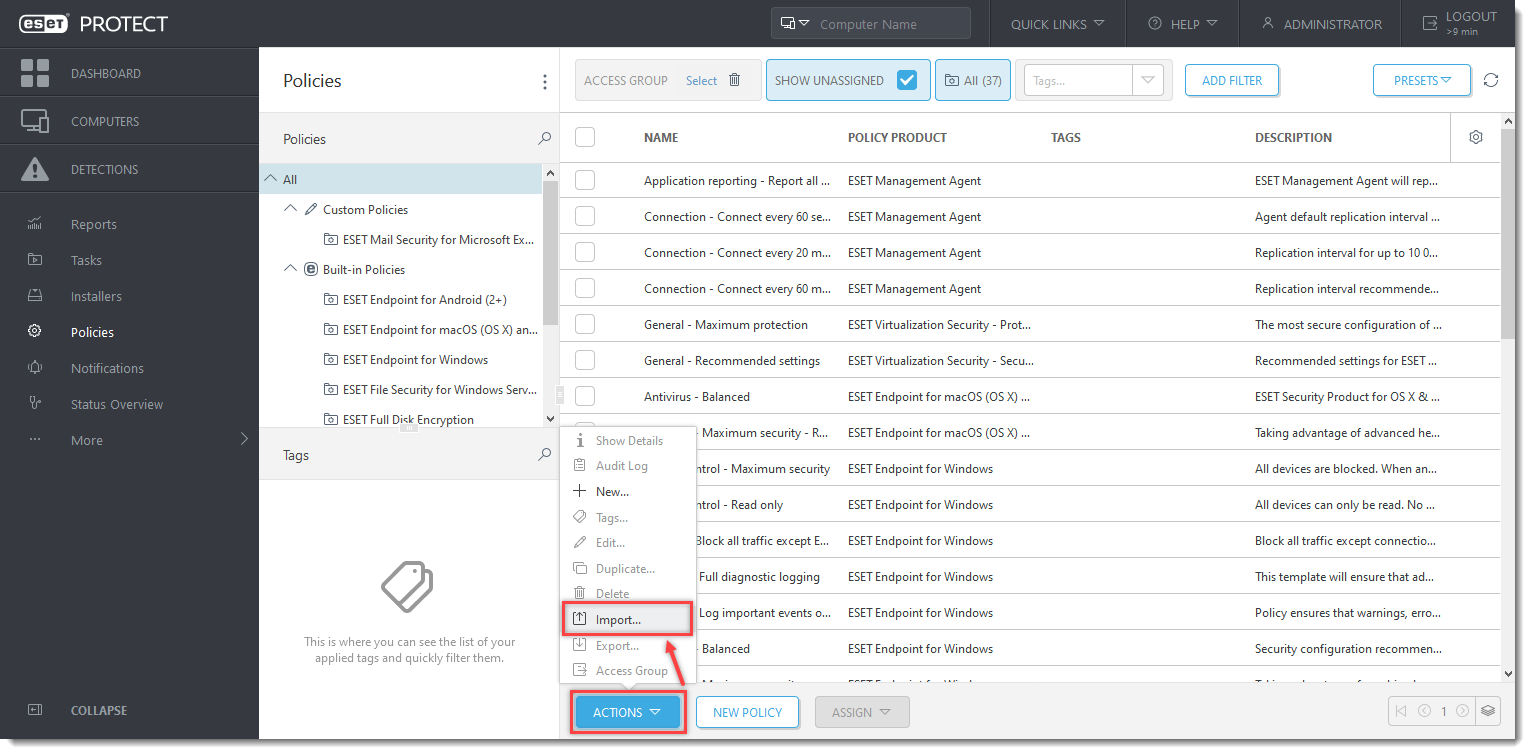
Open the ESET PROTECT or ESET PROTECT On-Prem. In the main menu, click Policies.
- Click Actions → Import....
Click the image to view larger in the new window
- Click Choose file to upload, select the downloaded policy, and click Import.
- Assign the policy to a client or assign the policy to a group. Policy settings will be applied to the target groups or client computers once they check in to ESET PROTECT or ESET PROTECT On-Prem.