Issue
- ESET Secure Authentication Web Console in Active Directory Integration mode displays the Authentication Server as Offline
- Two-factor authentication fails because ESET Secure Authentication components cannot connect to the Authentication Server
- Windows Event Viewer
- ESET Secure Authentication Logs
Details
Click to expand
- ESET Secure Authentication Web Console in Active Directory Integration mode displays the Authentication Server as Offline after applying the November 2022 update of Windows Server
- Custom network hardening can cause the AS status to display "Offline"
Solution
The November 2022 update of Windows Server includes some hardening for Netlogon and Kerberos, due to which the Authentication Server (AS) installed in Active Directory Integration mode appears offline in the ESET Secure Authentication Web Console. Therefore, ESET Secure Authentication components fail to connect to the AS.
Suppose server administrators harden the network security by disabling NTLM authentication and enabling only strong ciphers for Kerberos authentication. In that case, ESET Secure Authentication components will fail to pass network authentication if a weak cipher is used (for example, RC4).
To see if hardening is in place, use either Windows Event Viewer or ESET Secure Authentication logs.
Windows Event Viewer
-
Press the Windows key + R key.
-
Type eventvwr and press the Enter key.
-
Double-click Windows Logs and click Security.
-
In the Actions pane, click Filter Current Log.
-
For Event level, select Information.
-
From Keywords, select Audit Failure and click OK.
-
In the resulting logs, in Task Category, look up Kerberos Service Ticket Operations.
-
Select the matching log to see more information.
See a sample log below. See more info on the failure (0xE) depicted below.
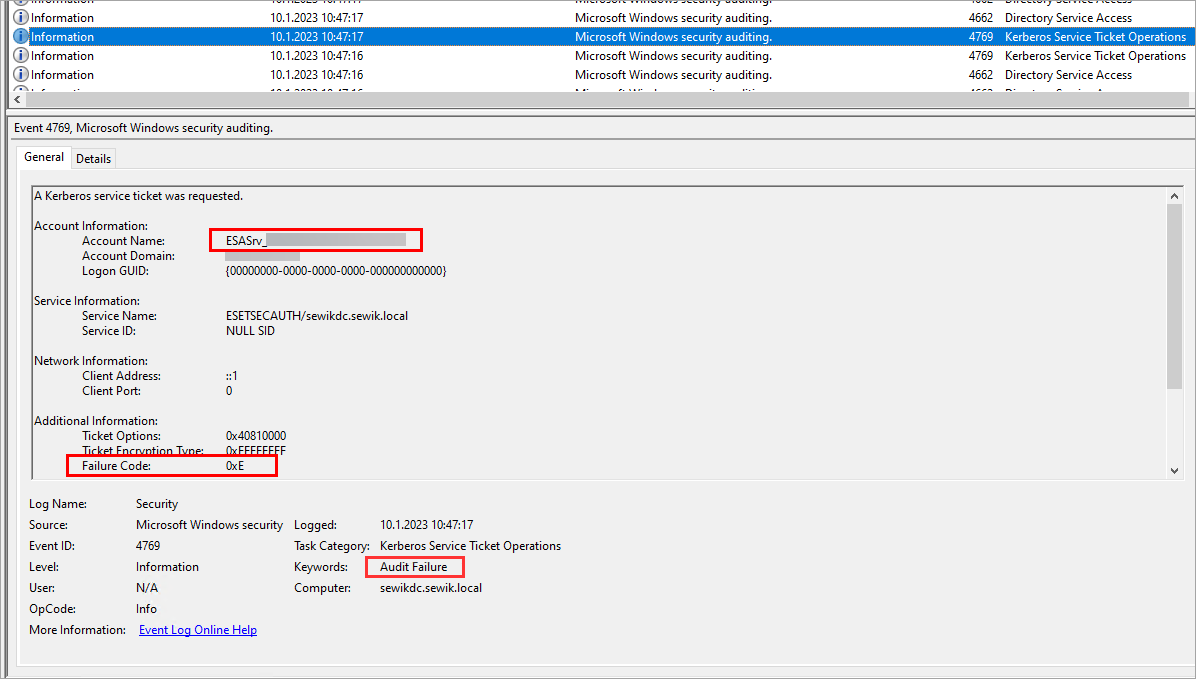
ESET Secure Authentication Logs
If you are using ESET Secure Authentication logs to see if hardening is in place in the EsaCore.log file, look for log entries similar to the ones below:
TRACE EIP.Services.Connector.EipServiceFinder Server error message: SOAP security negotiation with 'net.tcp://esa.mydomain.local:8000/ApiService_Public' for target 'net.tcp://esa.mydomain.local:8000/ApiService_Public' failed.
See inner exception for more details..
System.ServiceModel.Security.SecurityNegotiationException: SOAP security negotiation with 'net.tcp://esa.mydodmain.local:8000/ApiService_Public' for target 'net.tcp://esa.mydodmain.local:8000/ApiService_Public' failed.
See inner exception for more details. ---> System.ComponentModel.Win32Exception: Either the client credential was invalid or there was an error collecting the client credentials by the SSPI.
Where esa.mydomain.local is replaced by the address of your ESA installation.
The above-mentioned issue can occur if ESET Secure Authentication is configured to use weak ciphers via the msDS-SupportedEncryptionTypes attribute.
Figure 2-1 depicts such a setting found in the Active Directory Users and Computers (ADUC) management tool:
-
In ADUC, navigate to <your_active_directory_domain> → ESET Secure Authentication.
-
Find the ESET Secure Authentication Core Service user – its name is made up of ESASrv_ and the computer name. For example, ESASrv_PH2012R2NODC.
-
Double-click the user and select Attribute Editor.
-
Find
msDS-SupportedEncryptionTypes.
Figure 2-1
To remedy the issue, set the msDS-SupportedEncryptionTypes attribute used for ESET Secure Authentication to 0x3F. That value covers AES ciphers (D, E).
Alternatively, enable Kerberos AES 128bit or Kerberos AES 256bit encryption support for ESET Secure Authentication in the Account tab, which is an equivalent for enabling D and E ciphers.
