Issue
- An application is not working or is having connectivity issues after installing ESET Cyber Security
- Review the basics of Firewall rules and application rules
- Change application rules
- Create a rule to block or allow incoming or outgoing internet communication for an application in ESET Cyber Security
- Troubleshooting
Details
Click to expand
The Firewall controls all network traffic to and from the system by allowing or denying individual network connections based on specified filtering rules. It protects against attacks from remote computers and allows you to block specific services.
Solution
Review the basics of Firewall rules and application rules
Firewall rules
The Firewall recognizes three types of network connections: Outbound connections, Inbound connections and Trusted inbound connections; inbound connections originating from a trusted network.
-
Click ESET Cyber Security in the macOS menu bar (at the top of the screen) and click Settings.
Figure 1-1 -
Under Protections, click Firewall.
Figure 1-2 -
The Firewall processes rules in order from the top of the rule stack, which is shown in the Firewall preferences. When a rule matches the current communication, that rule is applied, and no further rules are processed for that connection.
- Global rules are applied first if allowed.
- Application rules are next if defined. When an application rule exists, it matches the application path, and its conditions are applied to the application's communication.
- Fallback rules are processed last.
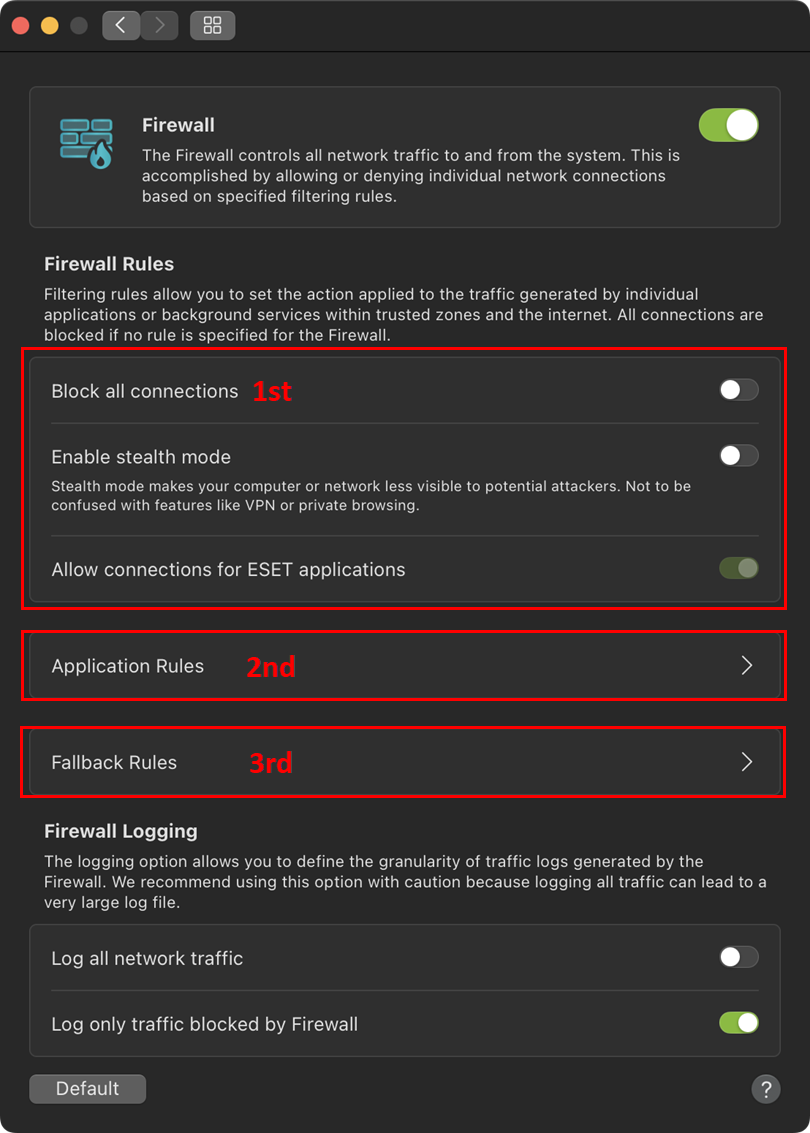
Figure 1-3
-
The Firewall primarily uses application-specific rules, as well as global and fallback rules. Application Rules are based on the application's path, and settings for both inbound and outbound communication for that application are specified.
-
By default, the Firewall enables outbound connections, and inbound connections are allowed for Apple applications. Click Fallback Rules to modify the settings.
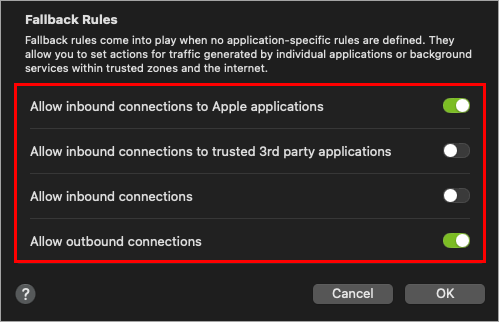
Figure 1-4
Change application rules
Users can define application rules through several options:
-
From the context menu in the Applications table under the Tools section of the main interface.
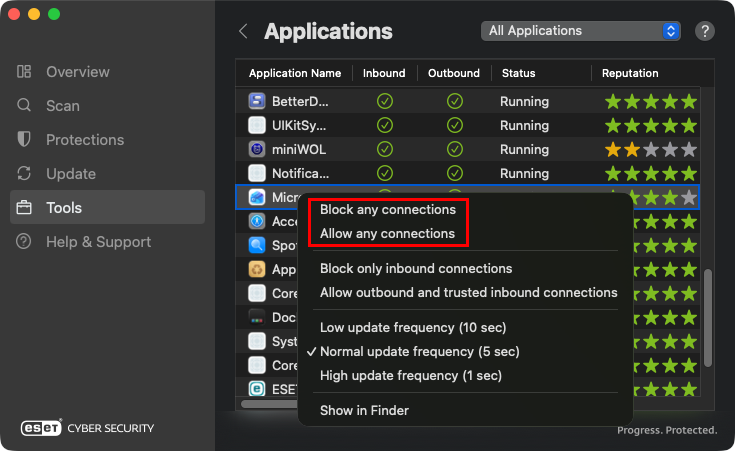
Figure 2-1 -
From the Finder context menu.
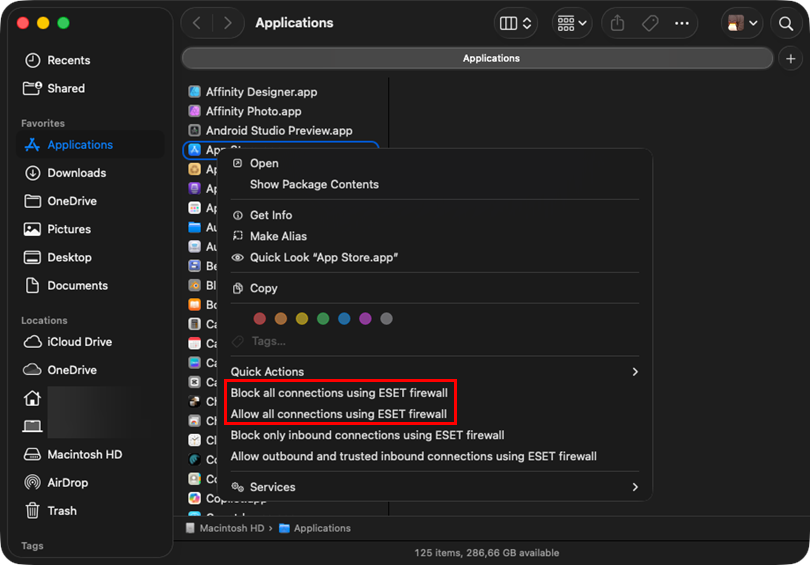
Figure 2-2 -
From the Application Rules setup menu within the Firewall settings.
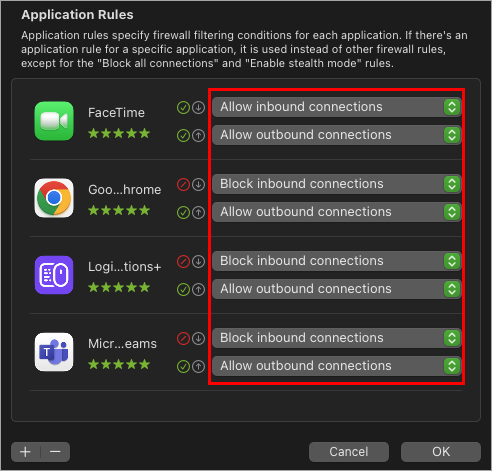
Figure 2-3 -
The context menu in Firewall Logs is under the Logs subsection of the Tools section in the main interface.
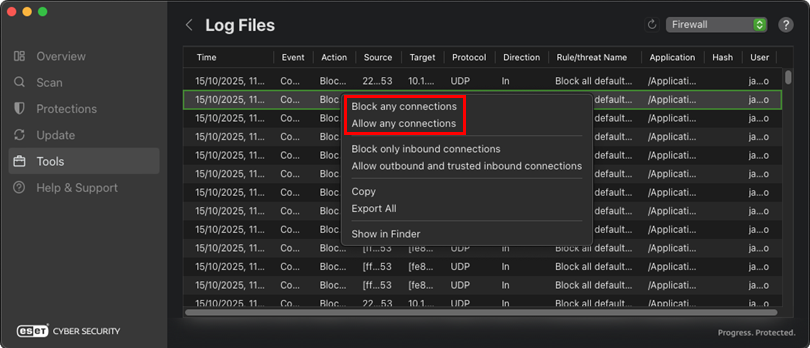
Figure 2-4
Create a rule to block or allow incoming or outgoing internet communication for an application in ESET Cyber Security
-
Click ESET Cyber Security in the macOS menu bar (at the top of the screen) and click Settings.

Figure 3-1 -
Under Protections, click Firewall.

Figure 3-2 -
Click Application Rules.
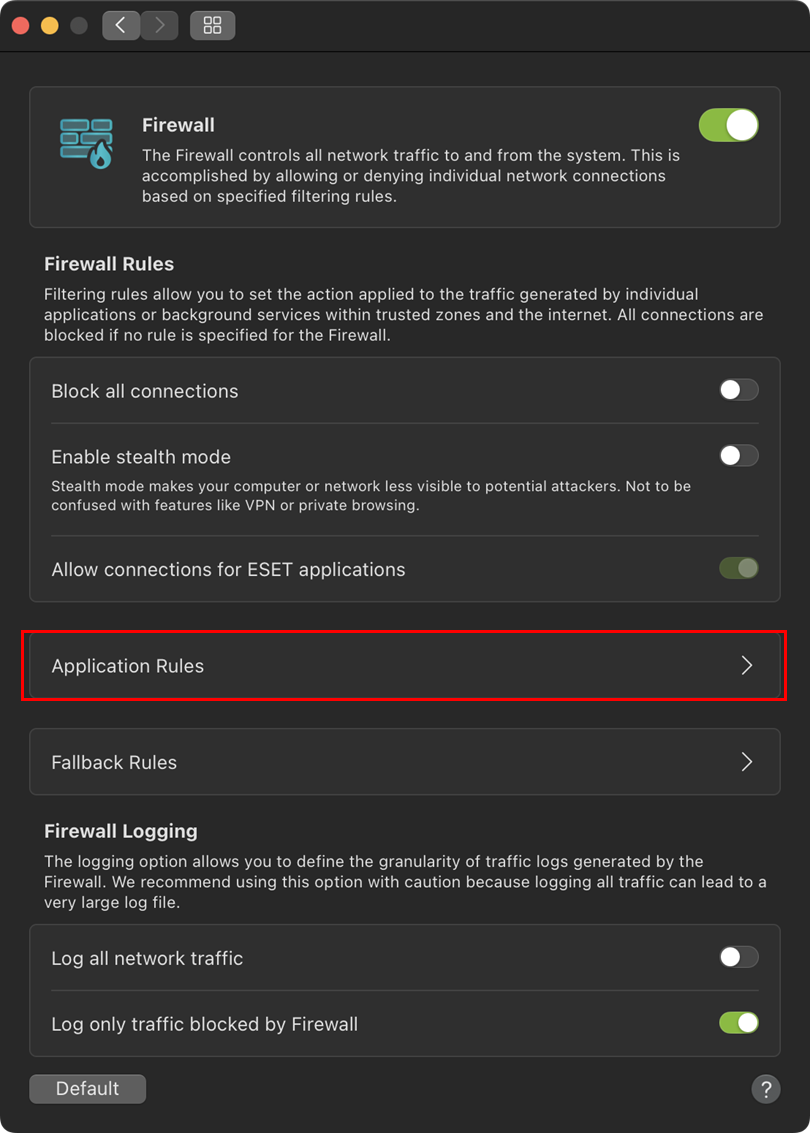
Figure 3-3 -
Click the + (plus) icon to add an application rule.
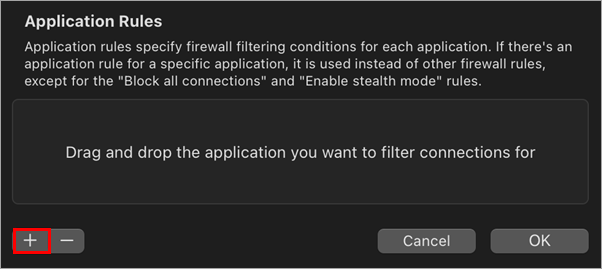
Figure 3-4 -
Select an application from the Applications menu and click Open.
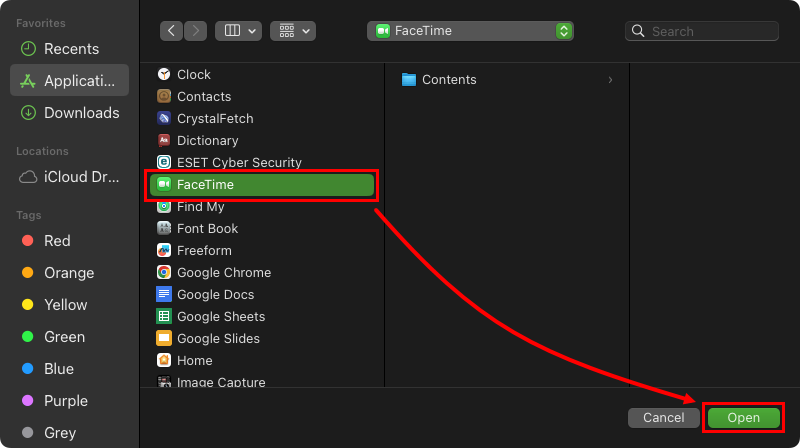
Figure 3-5 -
Select a filtering option for the inbound and outbound settings, and click OK to save the rule.
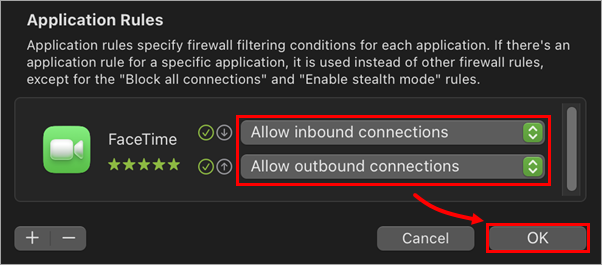
Figure 3-6
Troubleshooting
My third-party application is not working
Suppose a non-Apple application stops working after enabling the Firewall. In that case, it is likely because the application requires inbound connections initiated from the server side, which the Firewall blocks by default for non-Apple applications.
To resolve this issue, enable all inbound communication. If the communication resumes, create a Firewall rule.
An issue is occurring due to the Firewall.
If you experience connectivity problems with ESET Cyber Security installed, you can use Firewall logs to identify and resolve the blocked communication.:
-
Enable logging for blocked connections (enabled by default; you can check in the Firewall settings).
-
Replicate the issue.
-
Identify the blocked communication. For easier analysis, export the Firewall logs as a CSV file and then import them into a spreadsheet program, such as Microsoft Excel, to search for the issue.
-
Create the necessary rule in the Firewall to allow the identified communication.