Solution
- Click the appropriate link below to download the installer file for ESET File Security for Microsoft Windows Server 7:
- When the download is complete, double-click the installer file to launch the ESET File Security for Microsoft Windows Server Setup Wizard.
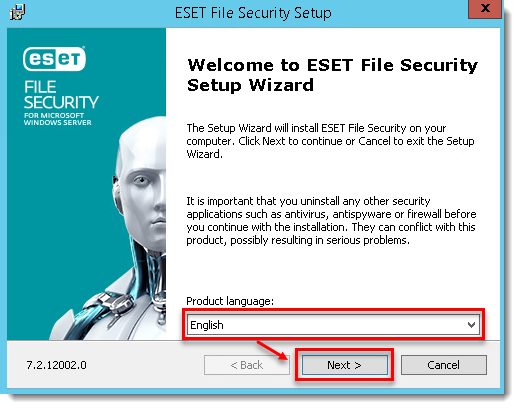
- Select your language and click Next.
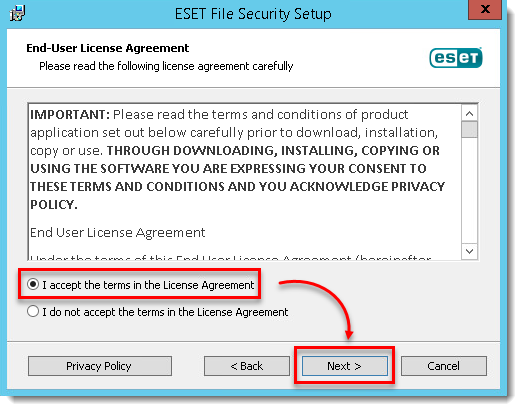
- Select I accept the terms in the License Agreement and click Next.
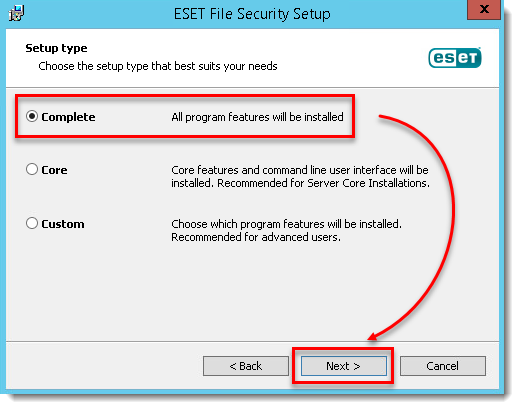
- Select Complete and click Next.
- Verify and update the install location for the ESET File Security Product, Module or Data folders if necessary. Click Install.
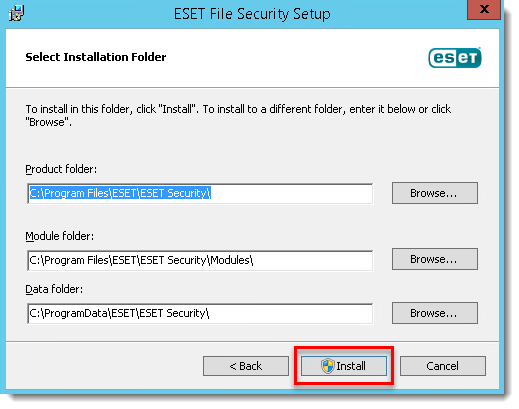
- Click Finish. ESET File Security for Microsoft Windows Server will open automatically.
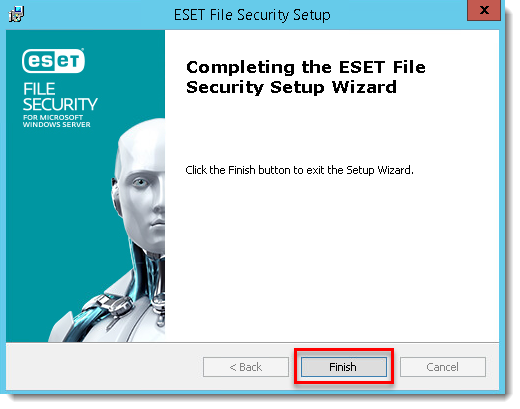
- Once the installation is finished, click Enter a License Key.
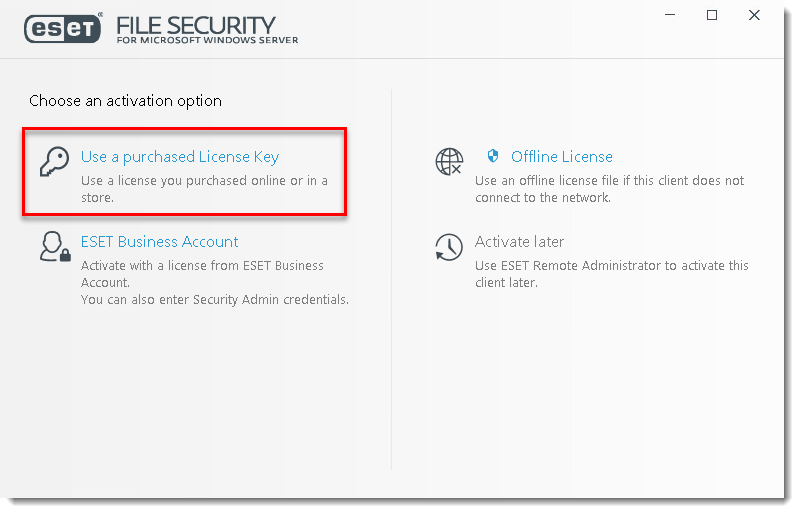
- Type your License Key in the License Key field and click Continue. If you do not have your License Key, click here to have your license information sent to you.
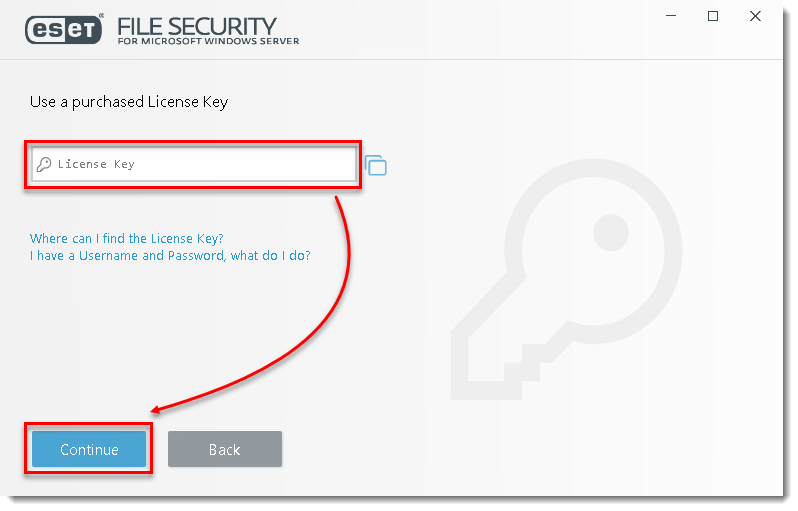
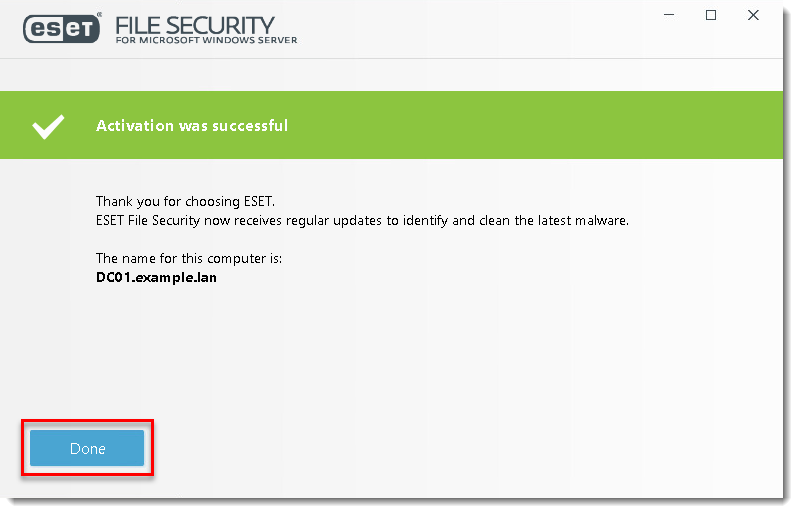
- After Activation was successful, click Done.
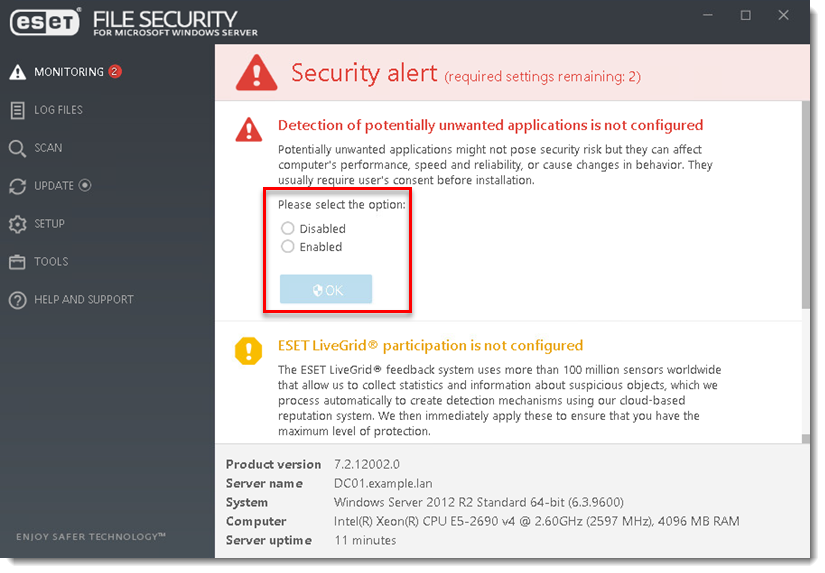
- Select an option for the Detection of potentially unwanted applications and click OK. For more information, see what is a potentially unwanted application?
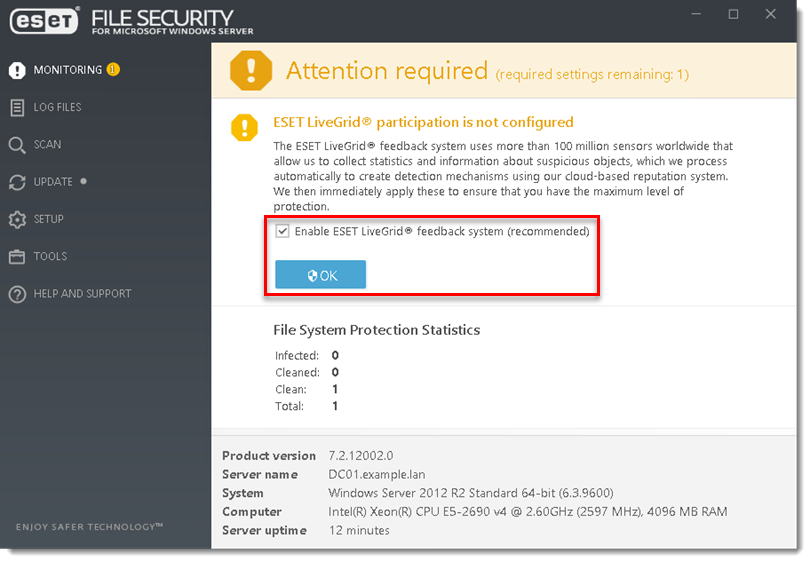
- Select your participation in the ESET LiveGrid feedback system and click OK.
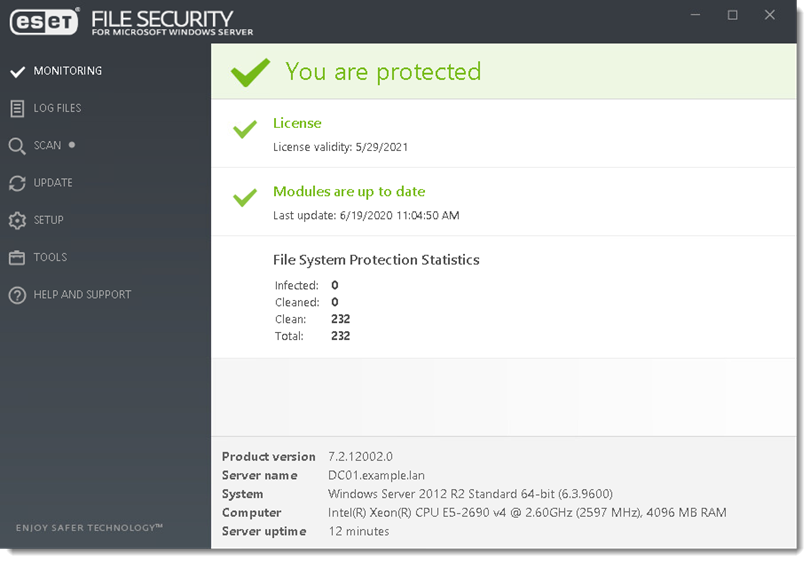
- ESET File Security for Microsoft Windows Server is installed and your computer is fully protected.