Problema
- Seu produto ESET detecta a ameaça Filecoder.WannaCryptor ou uma variante dessa ameaça
- Certifique-se de que seu sistema esteja corrigido contra o exploit EternalBlue
Solução
A ESET detecta e bloqueia essa ameaça e suas variantes (como o WannaCryptor.D). A ESET identifica essa ameaça como Filecoder.WannaCryptor.
Em sistemas não protegidos pela ESET, um exploit do Windows chamado EternalBlue pode ser usado para introduzir o WannaCryptor. Recomendamos enfaticamente que você siga as sugestões abaixo para garantir o mais alto nível de segurança em seu computador:
- Certifique-se de que ESET Live Grid está ativado em seu produto ESET
- Assegure-se de que seu software ESET esteja atualizado para a versão mais recente e que esteja executando o mecanismo de detecção mais atualizado
- Avise os colegas que recebem frequentemente e-mails de fontes externas - por exemplo, departamentos financeiros ou de Recursos Humanos
- Faça backup de seus dados regularmente. Em caso de infecção, isso o ajudará a recuperar todos os dados. Não deixe o armazenamento externo usado para backups conectado ao seu computador para eliminar o risco de infecção dos backups. Se o seu sistema exigir atualizações do Windows para receber a correção para essa exploração, crie novos backups após aplicar a correção
- Desative ou restrinja o acesso ao Remote Desktop Protocol (RDP), consulte Práticas recomendadas do Remote Desktop Protocol contra ataques
- Desativar macros no Microsoft Office
Para obter informações mais detalhadas sobre como você pode usar a ESET para proteger seus sistemas contra infecções de ransomware, consulte Melhores práticas de proteção contra o malware Filecoder (ransomware).
Certifique-se de que seu sistema esteja corrigido contra o exploit EternalBlue
A ESET lançou uma ferramenta gratuita para ajudar a determinar se sua máquina Windows está corrigida contra o EternalBlue.
Siga as etapas abaixo para verificar se há vulnerabilidades em seu sistema usando o ESET EternalBlue Checker:
-
Clique duas vezes no arquivo baixado para executar a ferramenta.
-
Se a ferramenta encontrar uma vulnerabilidade em seu sistema devido à falta de patches da Microsoft, será exibida a mensagem Seu computador está vulnerável.
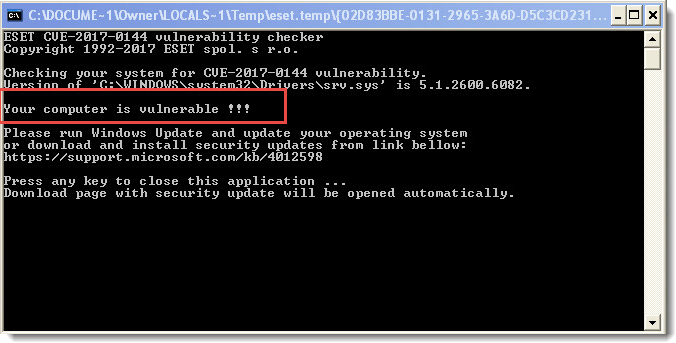
Figura 1-1 -
Pressione qualquer tecla para abrir a página de atualização do Microsoft Windows. Clique em Catálogo do Microsoft Update.
-
Na página do Catálogo do Microsoft Update, localize seu sistema operacional na coluna Products e clique no botão Download ao lado do seu sistema.
-
Clique no link na janela Download para fazer o download da atualização de segurança do seu sistema.
-
Depois que a atualização de segurança tiver sido instalada, reinicie o computador.
-
Depois que o computador for reiniciado, execute o ESET EternalBlue Checker novamente para verificar se a atualização de segurança foi instalada corretamente e se seu sistema não está mais em risco. Se a atualização de segurança foi instalada corretamente, será exibida a mensagem Seu computador está seguro, a atualização de segurança da Microsoft já está instalada.
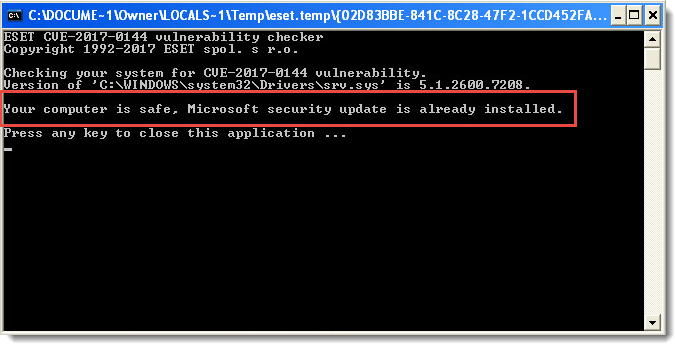
Figura 1-2