Issue
- Add a domain name, email address or IP address to the Approved lists (whitelist) to prevent the ESET Mail Security spam filter from scanning those communications
- Add a domain name, email address, IP address or country to the Blocked lists (blacklist) to have ESET Mail Security mark all communications from those communications as spam
- Add a domain name, email address or IP address to the Ignored lists to continue to scan all communications for spam to protect you from spoofed emails that take advantage of your familiarity with a certain email address except for those specific lists selected to ignore
Details
Click to expand
In ESET Mail Security for Microsoft Exchange (EMSX) version 8.x and later, the whitelist, blacklist and exception lists are controlled by the Approved, Blocked and Ignored lists. These criteria are based on keywords searched in the email addresses, domain names or IP addresses.
Solution
Configure the Approved list
-
Open ESET Mail Security. Click Start → All Programs → ESET → ESET Mail Security.
-
Press the F5 key to open Advanced Setup.
-
In the Server section, click Antispam protection and expand Filtering and Verification.
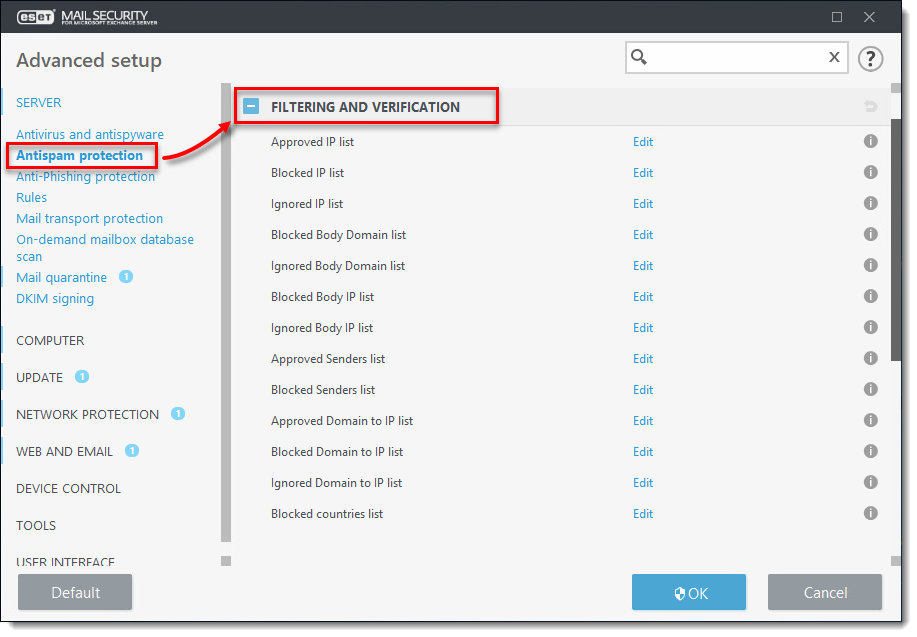
Figure 1-1 -
Next to one of the lists below, click Edit:
- Approved IP list xxx
- Approved Senders list (email)
- Approved Domain to IP list (this whitelists emails originating from IP addresses that are resolved from specific domains)
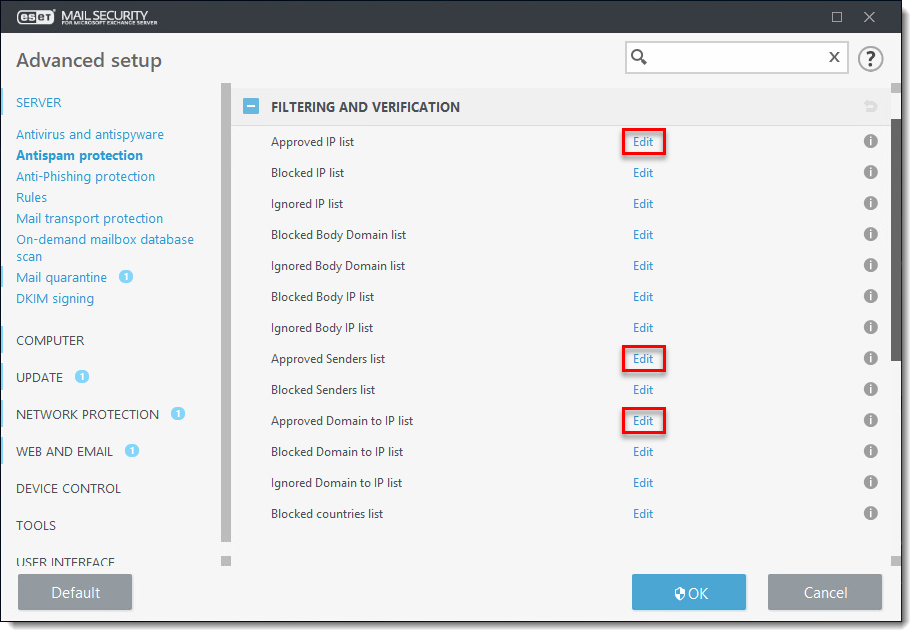
Figure 1-2 -
Click Add and type the domain name, email or IP address you want to add to the Approved list and click OK → OK.
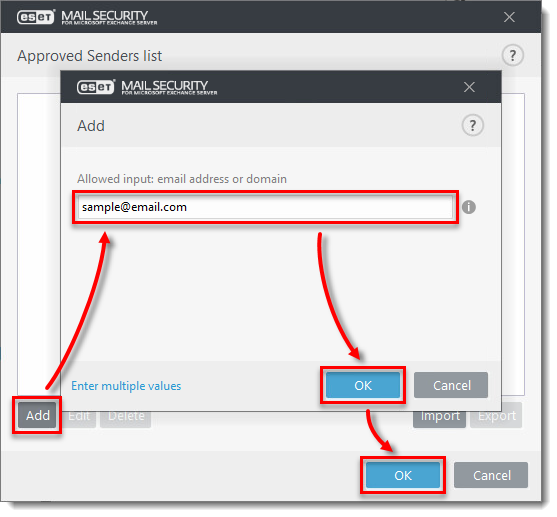
Figure 1-3
Configure the Blocked list
-
Open ESET Mail Security. Click Start → All Programs → ESET → ESET Mail Security.
-
Press the F5 key to open Advanced Setup.
-
In the Server section, click Antispam protection and expand Filtering and Verification.

Figure 2-1 -
Next to one of the lists below, click Edit:
- Blocked IP list
- Blocked Body Domain list (blocks emails that contain the specified domain in the message body)
- Blocked Body IP list (blocks emails that contain the specified IP address in the message body)
- Blocked Senders list (email)
- Blocked Domain to IP list (this blacklists emails originating from IP addresses that are resolved from specific domains)
- Blocked countries list (blocks emails from specified countries)
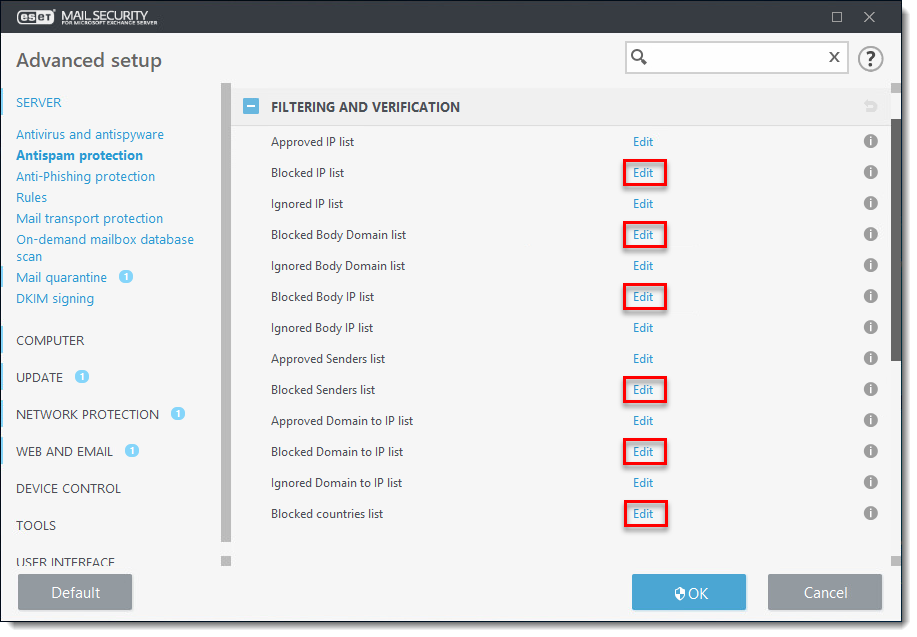
Figure 2-2 -
Click Add and type the domain name, email or IP address you want to add to the Blocked list and click OK → OK.
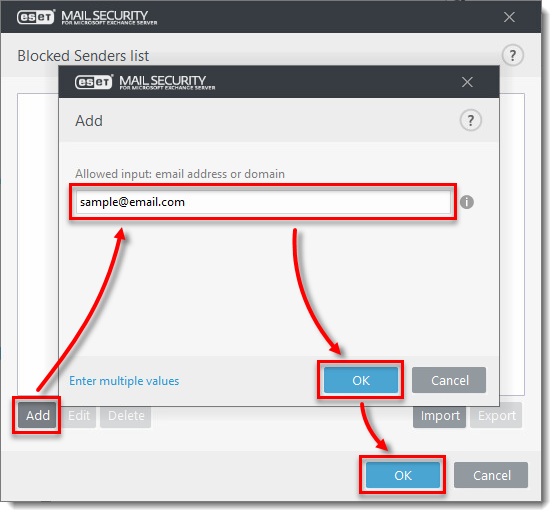
Figure 2-3
Configure the Ignored list
-
Open ESET Mail Security. Click Start → All Programs → ESET → ESET Mail Security → ESET Mail Security.
-
Press the F5 key to open Advanced Setup.
-
In the Server section, click Antispam protection and expand Filtering and Verification.

Figure 3-1 -
Next to one of the lists below, click Edit.
- Ignored IP list (list of IP addresses that will be ignored during classification)
- Ignored Body Domain list (specified domains in the message body will be ignored during classification)
- Ignored Body IP list (specified IP addresses in the message body will be ignored during classification)
- Ignored Domain to IP list (list of domains that resolves to IP addresses that in turn will not be checked during classification)
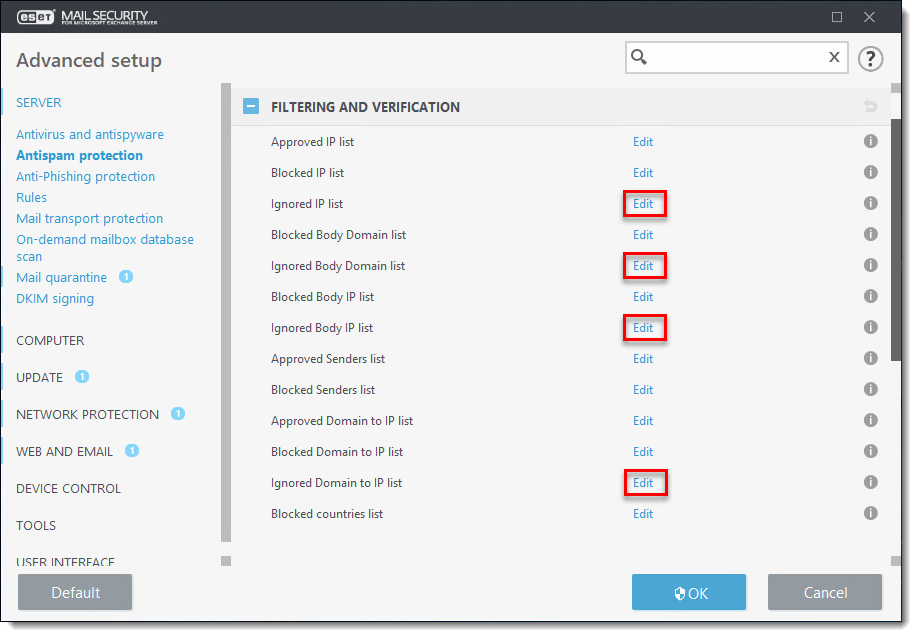
Figure 3-2 -
Click Add and type the domain name, email or IP address you want to add to the Ignored list and click OK → OK.
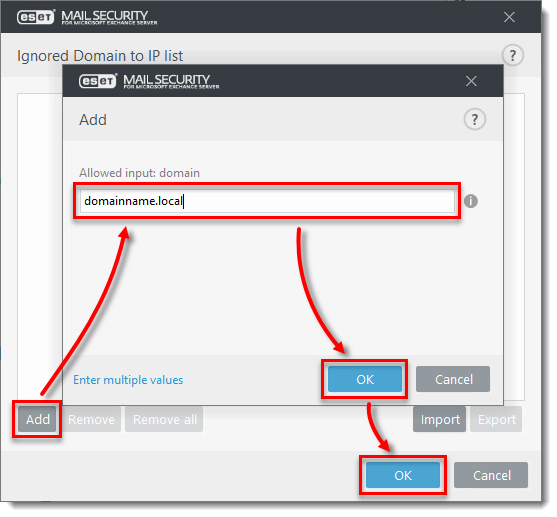
Figure 3-3