Issue
Details
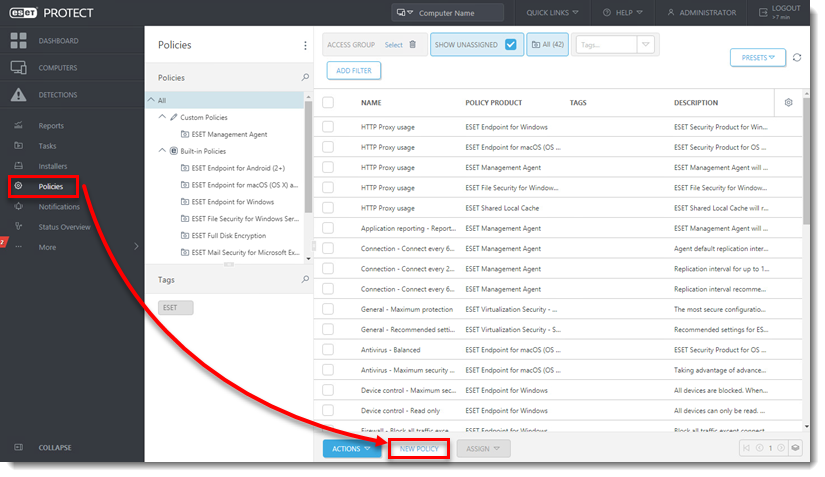
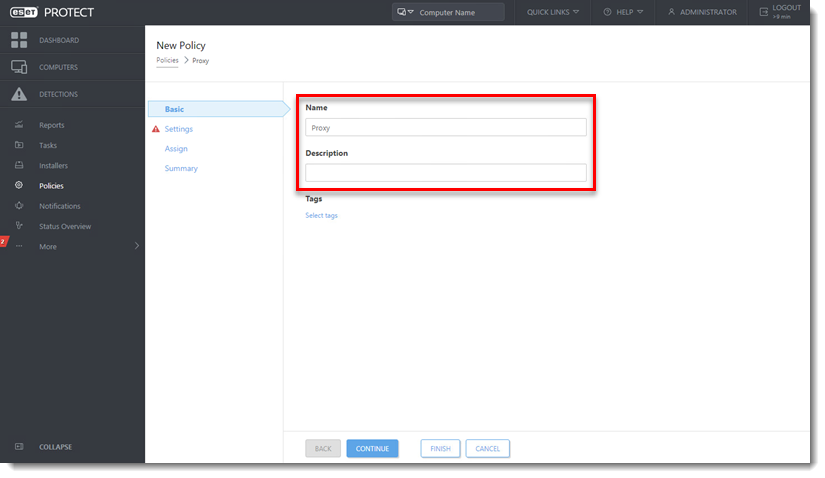
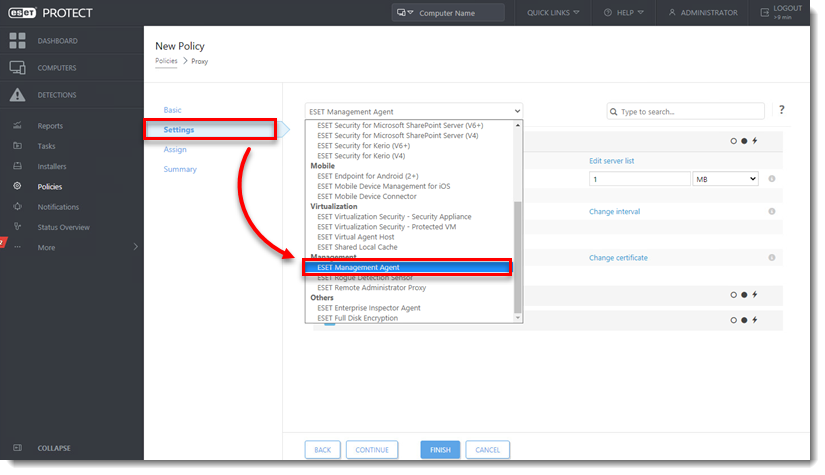
Click to expand
We recommend that you use Apache HTTP Proxy distributed by ESET. It has the correct configuration necessary for:
- Forwarding ESET Management Agents' replication (communication with ESET PROTECT Server)
- Caching ESET detection engine updates and installer files
- Caching ESET LiveGuard Advanced analysis results
If you use your custom Apache HTTP Proxy installation, make sure you have configured it properly. The proper configuration can be found in the file httpd.conf contained in the Apache installer distributed by ESET.
Solution
About HTTP Proxy
In ESET PROTECT On-Prem, the former ERA Proxy component is no longer being used. Instead, Apache HTTP Proxy forwards the information from Agents checking in to ESET PROTECT On-Prem. Users can also use other proxy solutions that comply with requirements. Unlike the former ERA Proxy component, Apache HTTP Proxy only forwards communication from the Agents; it does not cache or open the communication (replication).
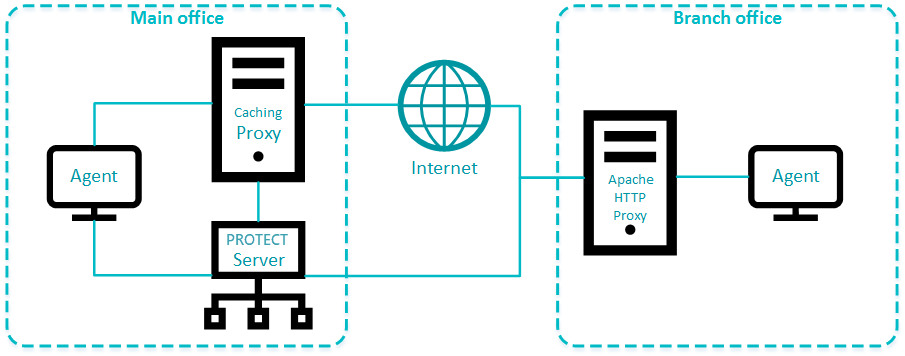
The Apache HTTP Proxy distributed by ESET is by default pre-configured for both replication and caching ESET product downloads and updates, however, some configuration is still needed (see step 6 in the documentation). See the scheme of a single proxy solution for a branch office in Fig. 1-1.
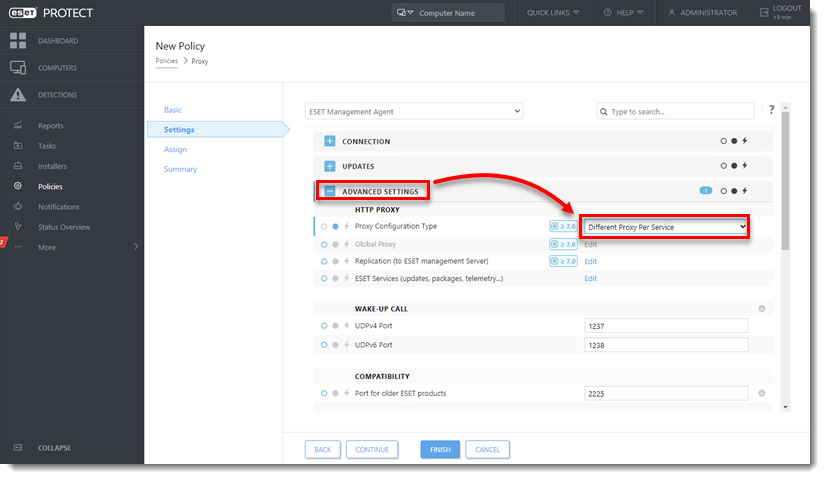
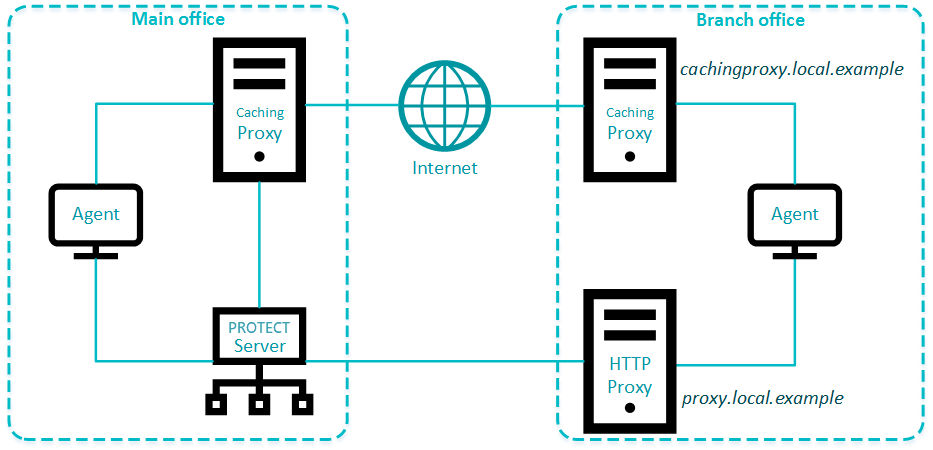
Use different proxy solutions for caching and replication
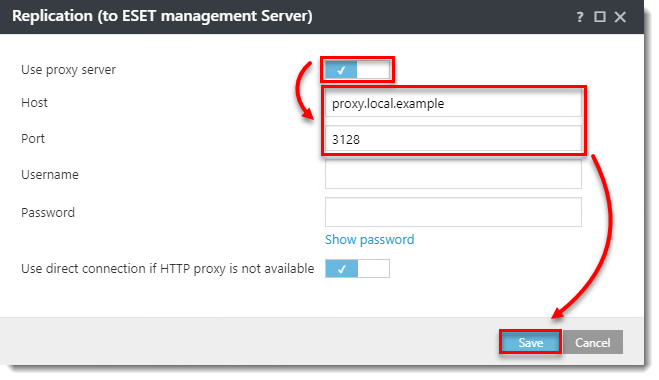
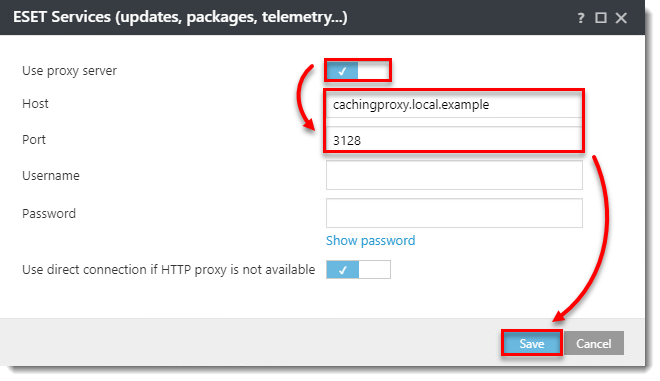
Users in some environments may need to use separate proxy solutions for caching and replication. In the example below one branch office is using a separate proxy for caching and another for replication to the ESET PROTECT Server in the main office.
Configure an Agent to use different proxies
Set up Apache HTTP Proxy for higher security
Apache HTTP Proxy security can be hardened to block all incoming connections except:
- ESET PROTECT On-Prem and ESET related hostnames.
- Change Apache service user to a less privileged user.
- Block all other ports except those required by ESERT PROTECT On-Prem (view the diagram).
-
Set up a separate proxy solution purely for forwarding the Agent - Server communication. In the ESET Management Agent policy click Advanced Settings > HTTP Proxy > Proxy Configuration type, select Different Proxy Per Service and set up the Replication (to ESET management Server) option. When the separate proxy solution is working:
- Remove the ports
443and563from theAllowCONNECTvalues in the proxy settings (httpd.conf) - Remove whitelisted addresses,
ProxyMatchsegments, from the proxy settings (httpd.conf), except your ESET PROTECT Server machine
- Remove the ports
-
-
Use a different proxy solution (not Apache) if it complies with the proxy requirements. ESET does not provide support for other proxy solutions.
Set up a proxy chain
- ESET PROTECT On-Prem does not support proxy chaining when the proxy requires authentication. To enable proxy chaining, add the following to the proxy configuration (
httpd.conf):
ProxyRemote * http://IP_ADDRESS:3128
- When using proxy chaining on the ESET PROTECT Virtual Appliance (VA), the SELinux policy must be modified. Open the terminal on the ESET PROTECT VA and run the following command:
/usr/sbin/setsebool -P httpd_can_network_connect 1
- When using proxy chaining, the firewall must allow communication on the ports in this diagram. Note that proxies communicate with each other at port 3128, but the last HTTP Proxy machine communicates with the ESET PROTECT Server at port 2222. The port numbers mentioned in the documentation are the defaults.
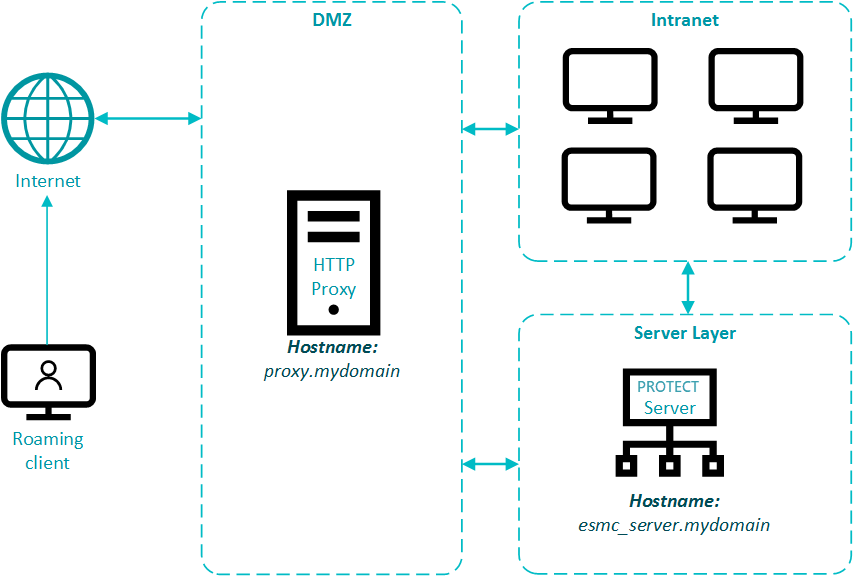
Apache HTTP Proxy in an environment with DMZ
In a more complex infrastructure, with a subnet that separates an internal LAN from untrusted networks (DMZ), it is recommended to deploy the ESET PROTECT Server out of the DMZ. Figure 2-1 illustrates one deployment scenario. When setting up an environment such as this, we recommend adhering to the following guidelines:
- Use hostnames instead of IP addresses in ESET PROTECT On-Prem component settings.
- If client machines can leave the intranet (roaming clients): Use dynamic groups and policies to ensure roaming clients use the server hostname resolvable from the internet only when they are outside of the intranet. Clients that cannot leave the intranet should use a hostname that is resolvable only inside the intranet, to be sure their connection is not routed via the internet.
- Apache HTTP Proxy (when used for replication) does not aggregate connections from Agents and does not save bandwidth. Use Apache HTTP Proxy for replication only if necessary.
- Using Apache HTTP Proxy for caching updates and installers is recommended. Roaming agents should not use a caching proxy when outside of the intranet. This can be achieved by using a hostname for caching proxy which is not resolvable outside of the intranet and allowing a direct connection.
- Firewall: Open only necessary ports (see the list of used ports) for selected hostnames.
- Set up Apache HTTP Proxy for higher security.