Issue
- Allow both internal and external (remote) clients to connect to an ESET PROTECT On-Prem server
- Requirements
- Network configuration steps
- Example scenario
Solution
Requirements
- External clients must be able to communicate with the ESET PROTECT On-Prem server on port 2222
- Internal and external DNS servers must be configured to point to the correct IP address of the ESET PROTECT On-Prem server based on where the client is located
Network configuration steps
-
Create a NAT rule on your firewall/router that points traffic received on port 2222 TCP to the internal IP address of your ESET PROTECT On-Prem server.
-
Add a new DNS record on your internal DNS server that points to the ESET PROTECT On-Prem server (in the example below, a record would be created pointing avserver.example.com to 192.168.0.123).
-
Add a new DNS record via your domain name registrar that will allow clients outside of your internal network to locate the external IP of your ESET PROTECT On-Prem server.
-
Make sure that all necessary ports are open on servers and client workstations.
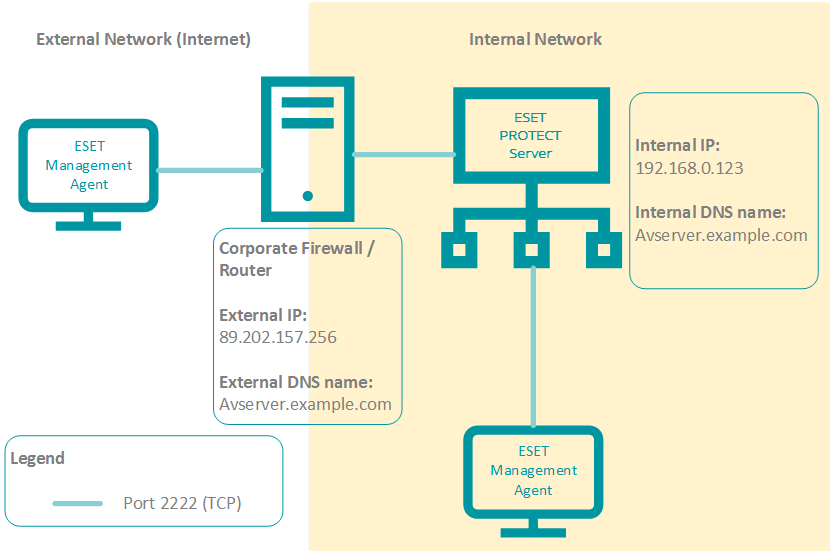
Example scenario
In the example below, the external IP of the Corporate Firewall / Router is 89.202.157.256. The corporate edge device is set to forward traffic on port 2222 to the ESET PROTECT On-Prem server. Therefore, example.com will point avserver.example.com to 89.202.157.256 so that clients external to the corporate network can communicate with the ESET PROTECT On-Prem server.
Click the image to view larger in new window