Details
VMware Horizon™ (with View) version 6 provides secure remote access to virtualized and remote desktops in corporate networks. With ESET Secure Authentication (ESA), 2FA is added through RADIUS (without requiring a separate RADIUS server to act as an intermediary).
Solution
Introduction
This article describes how to configure a VMware Horizon™ Server version 6 to authenticate users against an ESA Server. Before proceeding, verify that you've installed the RADIUS Server component of ESET Secure Authentication and can access the RADIUS service that allows external systems to authenticate users.
Before your VMware Horizon™ Connection Server can use the ESA Server to authenticate users via RADIUS, it must be set up as a RADIUS client on the ESA Server. Next, your server running the ESA RADIUS service must be setup as a RADIUS Server on the VMware Horizon™ Connection Server. Once these settings are in place, clients can begin logging into your VMware Horizon™ Server using ESA OTPs.
Part I - RADIUS client configuration
To allow the VMware Horizon™ Server to communicate with your ESA Server, you must configure the VMware Horizon™ server as a RADIUS client on your ESA Server:
-
Launch the ESA Management Console (found under Administrative Tools).
-
Navigate to RADIUS Servers and locate the hostname of the server running the ESA RADIUS service.
-
Right-click the hostname and select Add Client from the context menu.
- Configure a RADIUS client (see Figure 1-1).
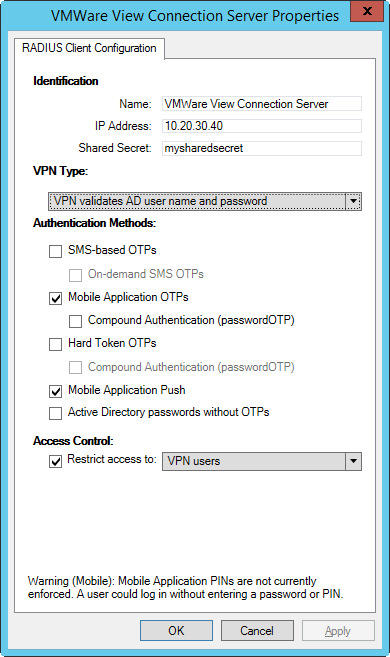
Figure 1-1
Note that the check box next to Mobile Application is selected. The warning may be safely ignored, since VMware Horizon™ will authenticate AD users.
Once ESA has been configured to communicate with your VMware Horizon™ Connection Server, configure the VMware Horizon™ Connection Server to communicate with your ESA RADIUS Server using the steps from Part II below.
Part II - Enabling Two-Factor Authentication using the VMware Horizon™ Connection Server Management Console
You must now enable two-factor authentication so that users are first prompted for their Active Directory credentials, and then prompted for their OTP passcode. This should be done via the VMware Horizon™ web based Management console.
-
Log into the VMware Horizon™ Management Console. The default URL is https://hostname/admin.
-
Navigate to View Configuration → Servers → Connection Servers.
-
Select the Connection Server on which you want to enable 2FA and click Edit.
- Navigate to the Authentication tab. In the Advanced Authentication section, select RADIUS from the 2-factor authentication drop-down menu and then select Create New Authenticator from the Authenticator drop-down menu:
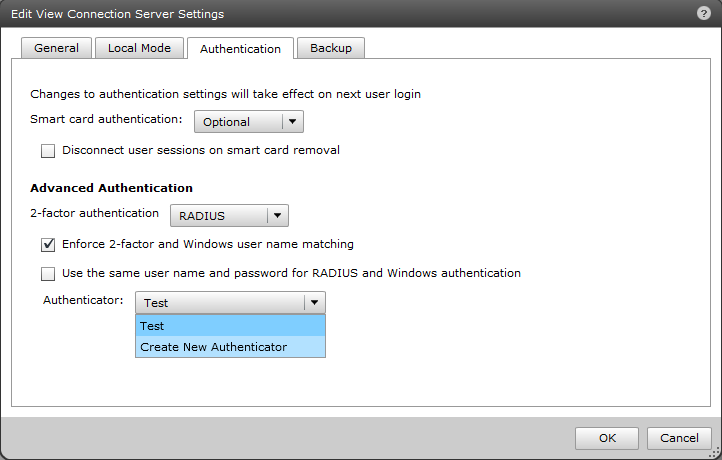
Figure 2-1
-
Set your preferred label and description. Set the hostname/address to thos of your ESA RADIUS server. Ensure that the authentication port is set to 1812.
-
Set the accounting port to 0 (the number zero).
-
Set the authentication type to PAP.
-
Enter the shared secret that you used during configuration of your RADIUS client (see Part 1, Step 1).
-
Set the server timeout to 20 seconds.
- If you want to use automatic RADIUS failover, add a second RADIUS server in the secondary authentication server tab (note that you will need to install ESA RADIUS on that server).
- Test the setup by launching the VMware Horizon View Client and connecting to your VMware Horizon server. In the Username field, enter a user that has been configured to use ESET Secure Authentication 2FA. In the Passcode field, enter a One-time Password (OTP) generated by the user's Mobile application. If authentication is successful, you will be prompted for your Active Directory password. You are now ready to roll out ESET Secure Authentication to other users in your organization.