Issue
- Potentially unwanted applications
- Warning – Potentially unwanted application found
- Potentially unwanted applications – Software wrappers
- Potentially unwanted applications – Registry cleaner
- Potentially Unwanted Content
Solution
Potentially unwanted applications
A potentially unwanted application (PUA) is a program that contains adware, installs toolbars, or has other unclear objectives. There are some situations where a user may feel that the benefits of a potentially unwanted application outweigh the risks.
For this reason, ESET assigns such applications a lower-risk category compared to other types of malicious software, such as trojans or worms. While installing your ESET product, you can decide whether to enable the detection of PUAs, as shown below:
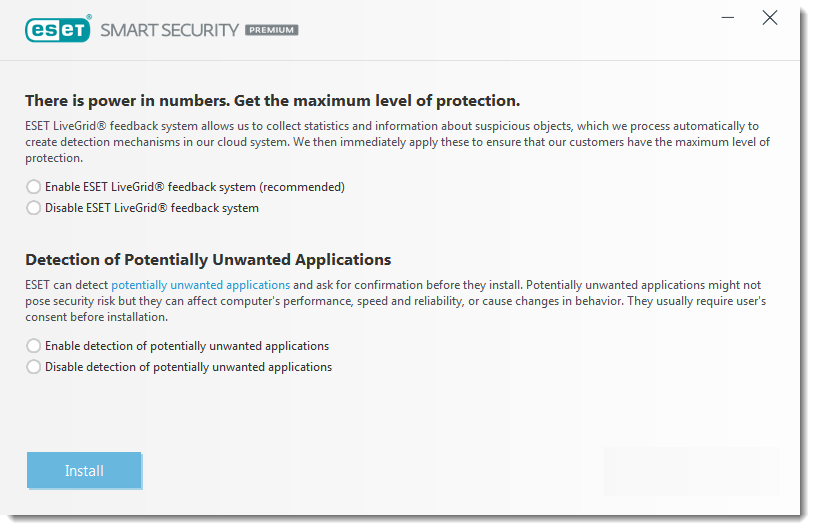
You can modify the PUA configuration settings in your program settings at any time. See the following Knowledgebase article for instructions on switching detection modes:
Configure ESET products to detect or ignore unwanted, unsafe and suspicious applications
Warning – Potentially unwanted application found
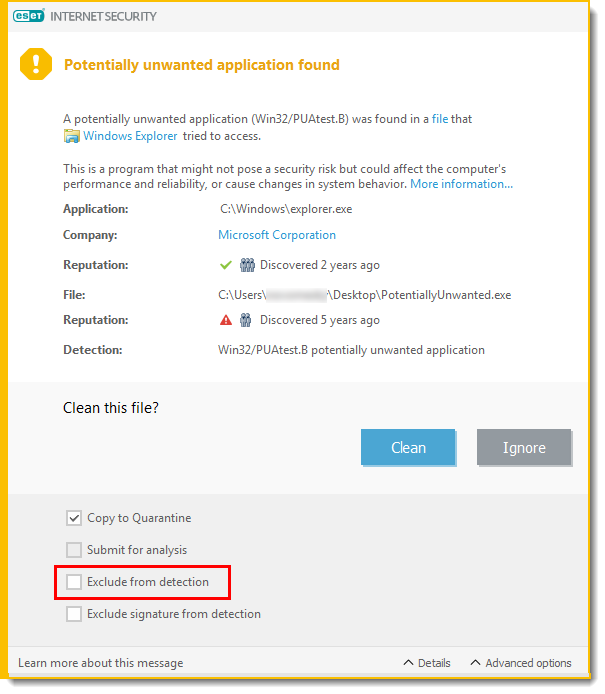
When a PUA is detected, you will be able to decide which action to take:
- Disconnect/Clean: This option ends the action and prevents the PUA from entering your system. You will see the Disconnect option for PUA notifications during download from a website and the Clean option for notifications for a file on disk.
- Ignore: This option enables a PUA to enter your system.
- Exclude from detection: To allow the detected file that is already on the computer to run in the future without interruption, click Advanced options, select the check box next to Exclude from detection and click Ignore.
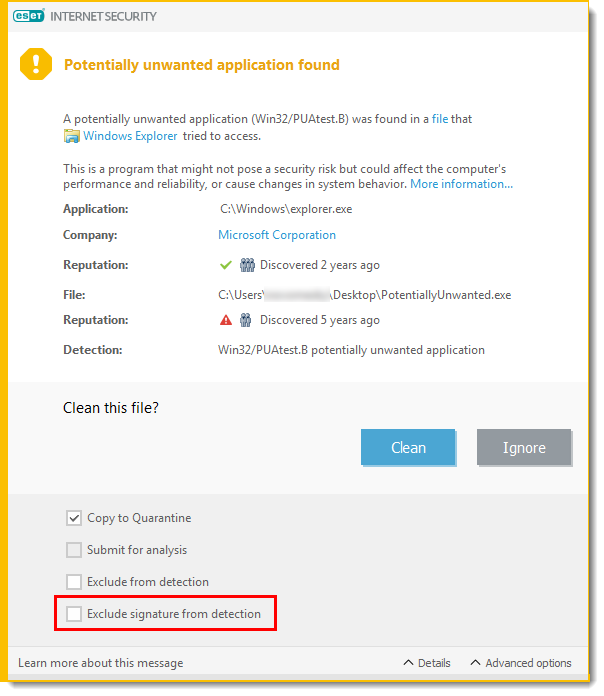
- Exclude signature from detection: To allow all files identified by a specific detection name (signature) to run on your computer in the future without interruption (from existing files or web download), click Advanced Options, select the check box next to Exclude signature from detection and click Ignore.
If additional detection windows with an identical detection name are displayed immediately afterward, click Ignore to close them (any additional windows are related to a detection that occurred before you excluded signature from detection).
Potentially unwanted applications – Software wrappers
A software wrapper is a special type of application modification that is used by some file-hosting websites. It is a third-party tool that installs the program you intended to download but adds additional software, such as toolbars or adware.
The additional software may also make changes to your web browser’s home page and search settings. File-hosting websites often do not notify the software vendor or download recipient that modifications have been made and often hide options to opt-out. For these reasons, ESET classifies software wrappers as a type of PUA to allow users to accept the download or not.
Potentially unwanted applications – Registry cleaners
Registry cleaners are programs that may suggest that the Windows registry database requires regular maintenance or cleaning. Using a registry cleaner might introduce some risks to your computer system.
Additionally, some registry cleaners make unqualified, unverifiable, or otherwise unsupportable claims about their benefits and/or generate misleading reports about a computer system based on the results of a "free scan". These misleading claims and reports seek to persuade you to purchase a full version or subscription, usually without allowing you to evaluate the registry cleaner before payment. For these reasons, ESET classifies such programs as PUA and provides you the option to allow or block them.
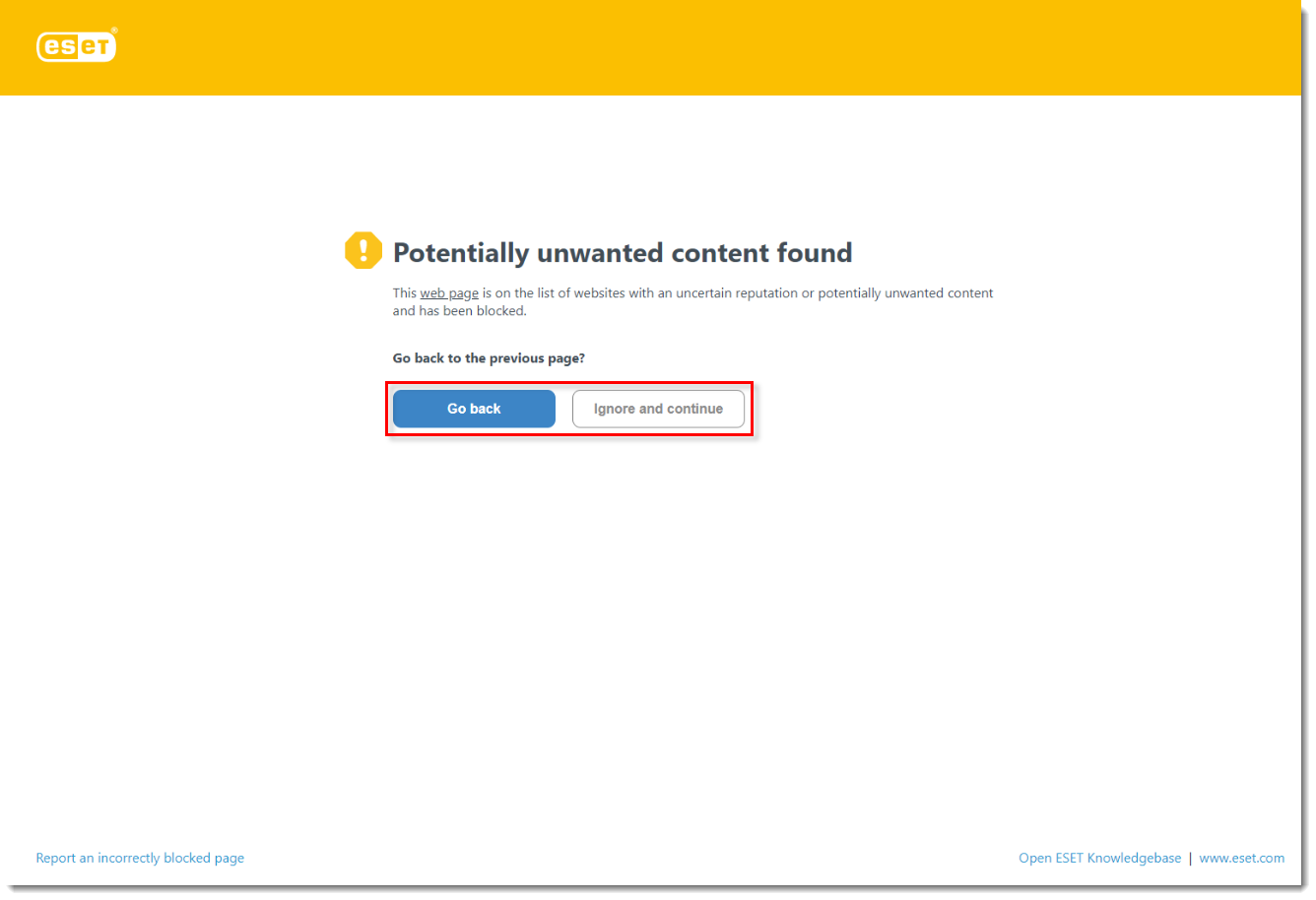
Potentially Unwanted Content
If PUA detection is enabled in your ESET product, websites that have a reputation for promoting PUAs or that have a reputation for misleading users into performing actions that might have negative implications on their system or browsing experience will be blocked as potentially unwanted content.
If you receive a notification that a website you are attempting to visit is categorized as potentially unwanted content, you can click Go back to navigate away from the blocked web page or click Ignore and continue to allow the site to load.