Issue
- You need to utilize the OpenCTI TAXII2 ingester to ingest the ESET Threat Intelligence feed data
Solution
-
In the OpenCTI dashboard main menu, click Data > Ingestion to open the Connectors section.
-
From the right panel, select TAXII Feeds.
-
Click the plus (+) icon in the bottom right corner of the screen.
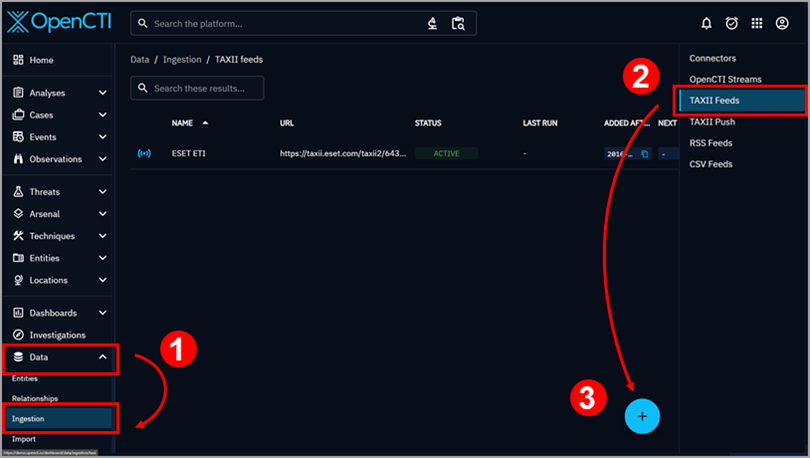
Figure 1-1 -
In the Create a TAXII ingester window, fill in the TAXII feed details described below and then click Create to create a new feed.
- Name: Name of the feed (for example, ETI Botnet feed)
- Description: Fill in a description of the feed (optional)
- TAXII server URL: Copy your URL of ESET Threat Intelligence TAXII 2.x API root (for example, https://taxii.eset.com/taxii2/643f4eb5-f8b7-46a3-a606-6d61d5ce223a)
- TAXII version: TAXII 2.1
- TAXII Collection: Copy your TAXII Collection ID (for example, 0abb06690b0b47e49cd7794396b76b20)
- Authentication type: Select Basic user/password from the drop-down menu
- Username and Password: to get your credentials, activate a TAXII feed
- User responsible for data creation: You can leave this field empty
- Import from date: Select a date no earlier than the previous day
-
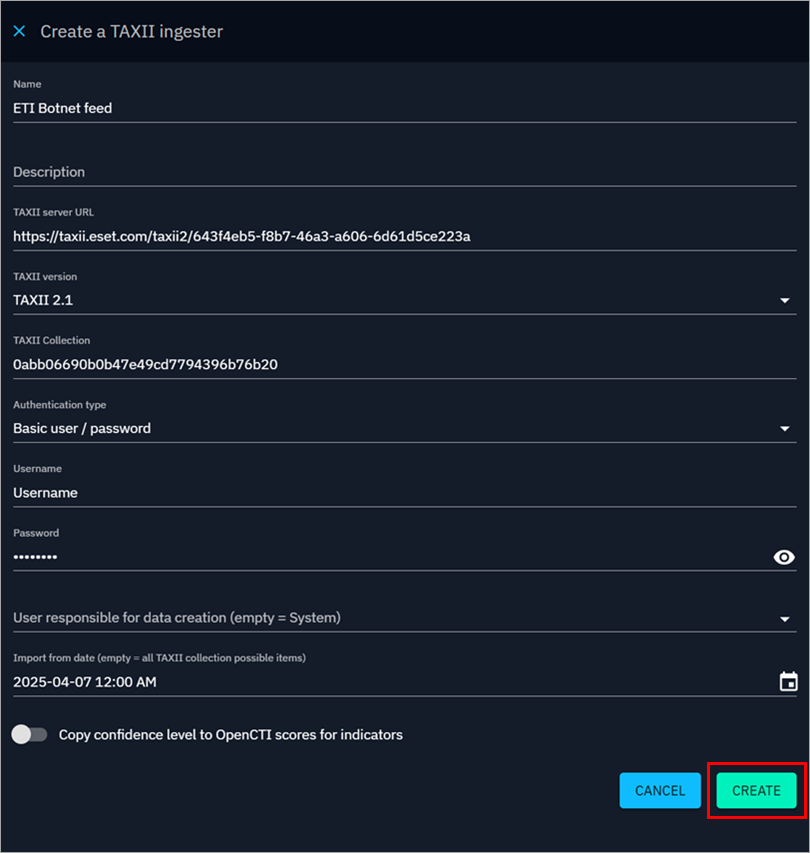
Figure 1-2