Issue
ESET business products (version 7 and later) include Ransomware Shield. This new security feature is a part of HIPS and protects computers from ransomware. When ransomware is detected on a client computer, you can view the detection details in ESMC Web Console in Detections.
By default, Ransomware Shield blocks all applications with potential ransomware behavior. Suppose a legitimate application or script is automatically running on the managed computer and performing operations that are evaluated as ransomware behavior (moving files across folders, encrypting files and folders). In that case, you may want to exclude it from being blocked by ESET business product.
Solution
ESMC Web Console Policy settings for ESET business products include Audit mode. When Audit mode is enabled, applications with ransomware behavior are allowed to run and are only logged in ESMC Web Console in Detections. The administrator can decide to block the potential detected threat or allow it permanently by adding it to exclusions.
Follow these steps to exclude applications on a managed computer from being detected as ransomware:
-
Open the ESET Security Management Center (ESMC) Web Console.
-
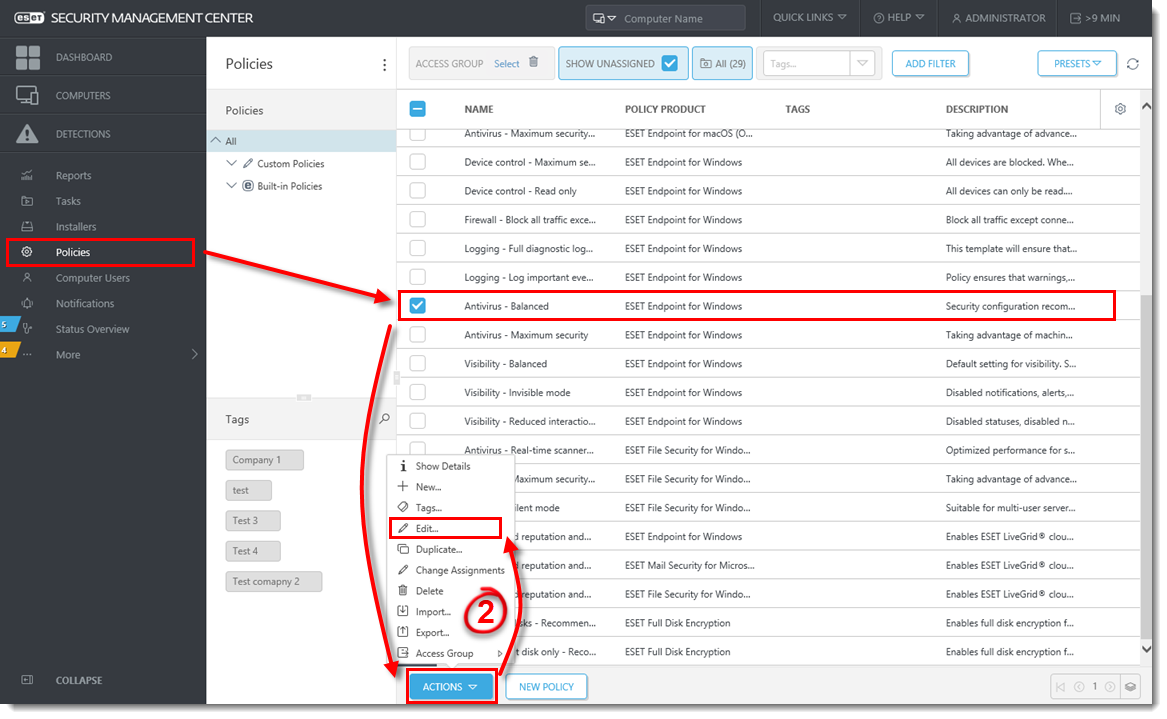
Click Policies, select the policy for ESET business product, and then click Policies → Edit.
Figure 1-1
Click the image to view larger in new window -
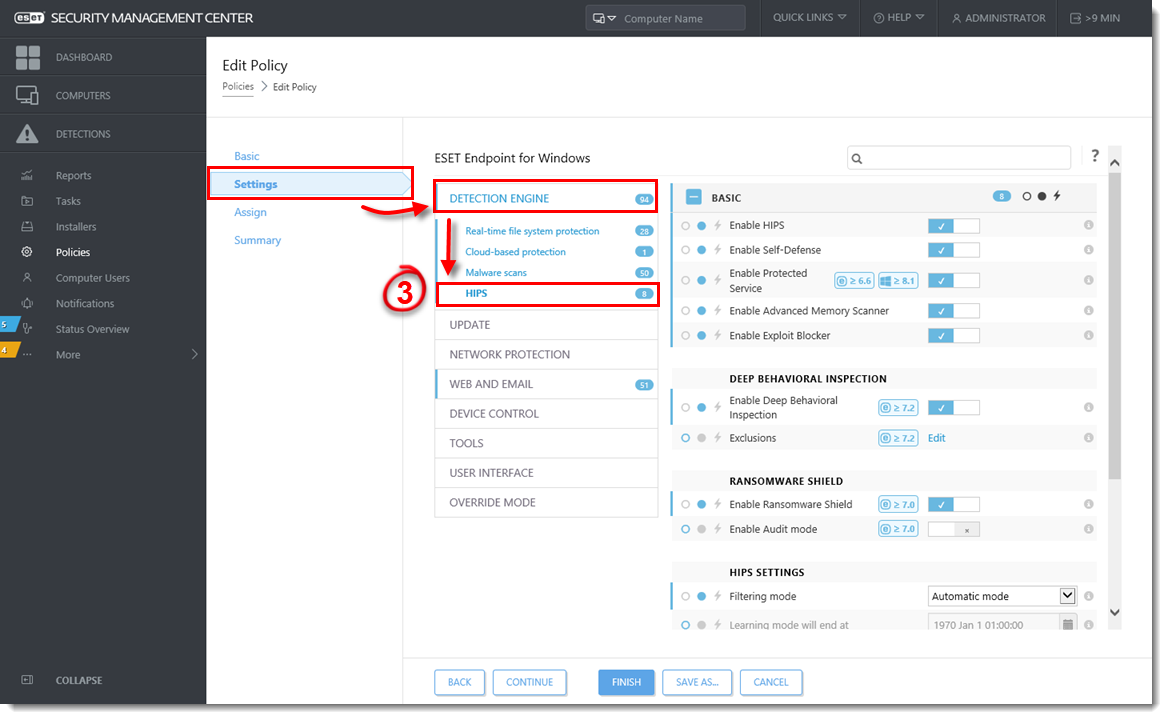
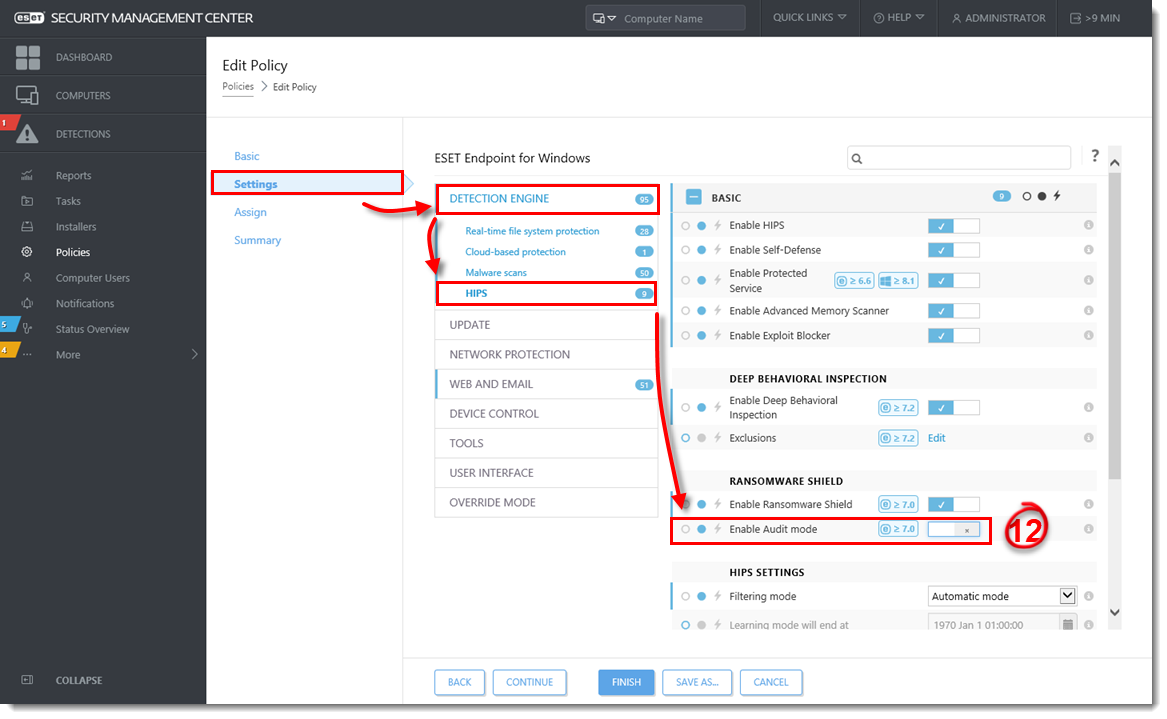
Click Settings → Detection Engine → HIPS.
Figure 1-2
Click the image to view larger in new window -
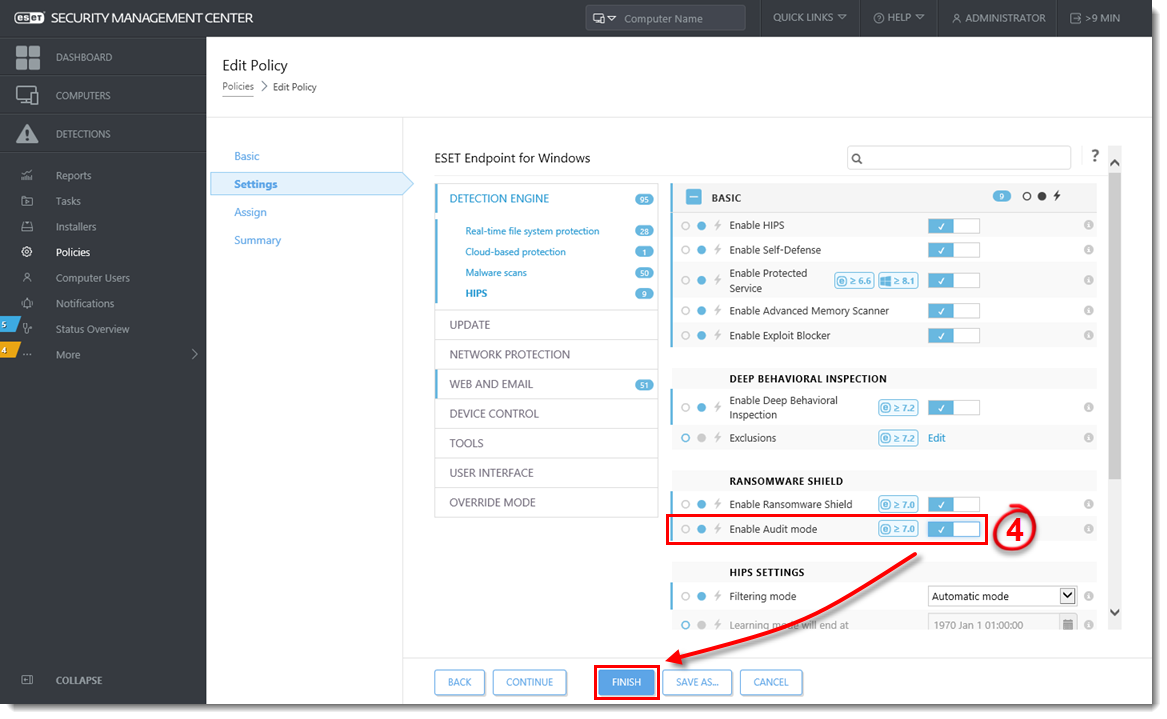
Click the toggle next to Enable Audit mode to enable this setting and click Finish to apply the Policy settings.
Figure 1-3
Click the image to view larger in new window -
On the managed computer, run the application with ransomware behavior.
-
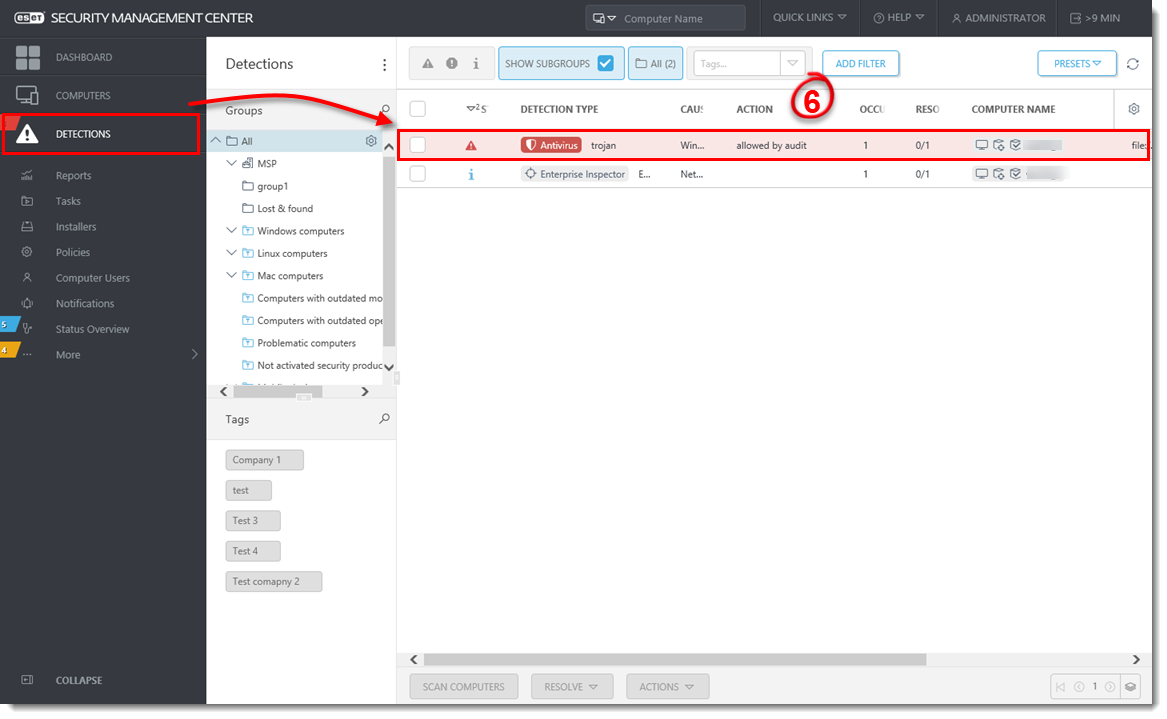
Return to ESMC Web Console and click Detections. You can see the information about the potential ransomware application detected on the client computer. In the Action column, there is a note allowed by audit.
Figure 1-4
Click the image to view larger in new window -
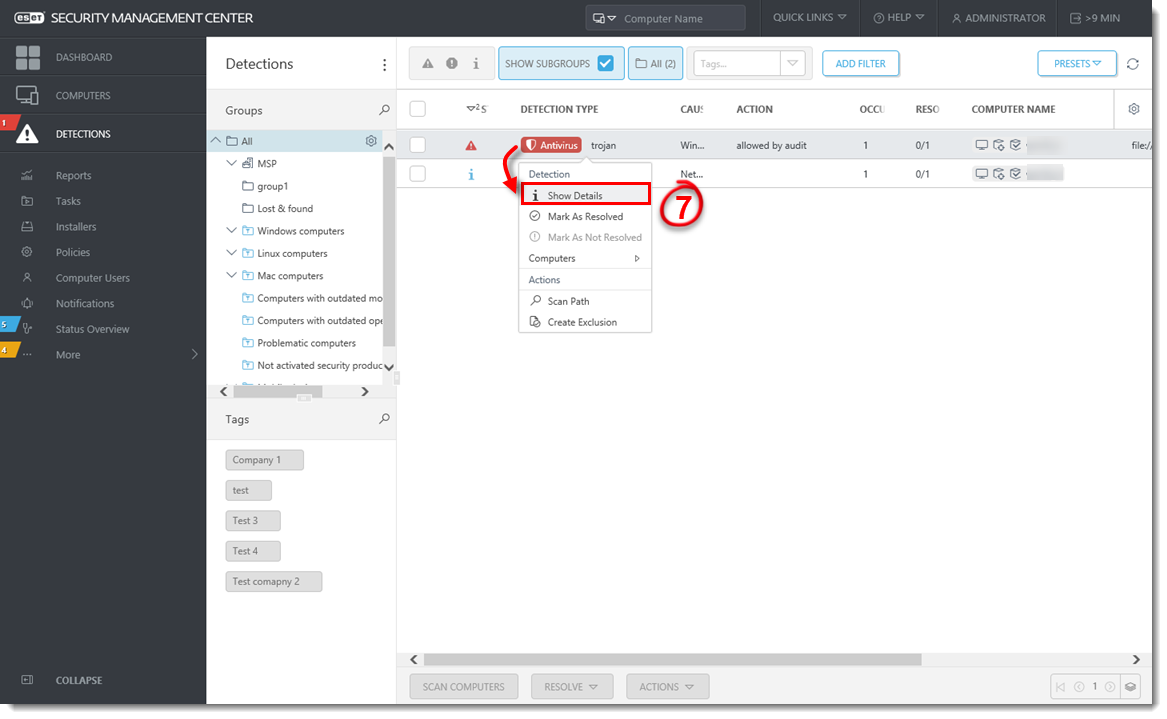
Click the detection and click Show Details. Verify the path to the application in Uniform Resource Identifier (URI) and make sure that you want to exclude the detection. Then click Close.
Figure 1-5
Click the image to view larger in new window -
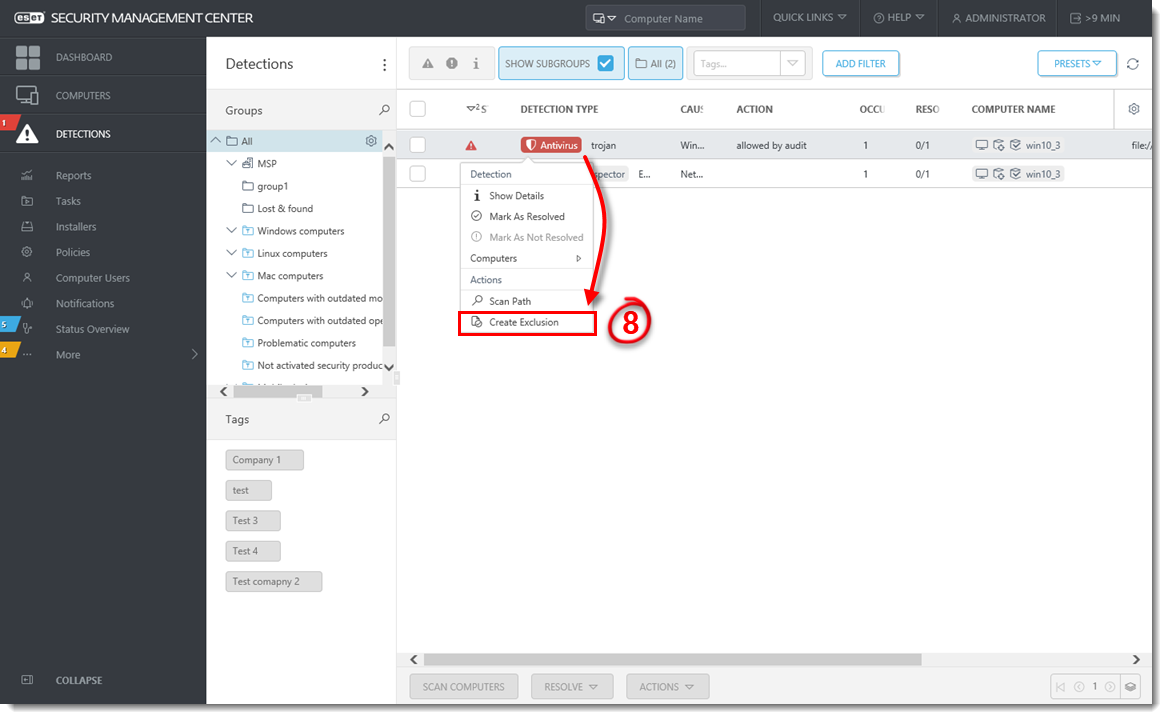
Click the detection and select Create Exclusion.
Figure 1-6
Click the image to view larger in new window
-
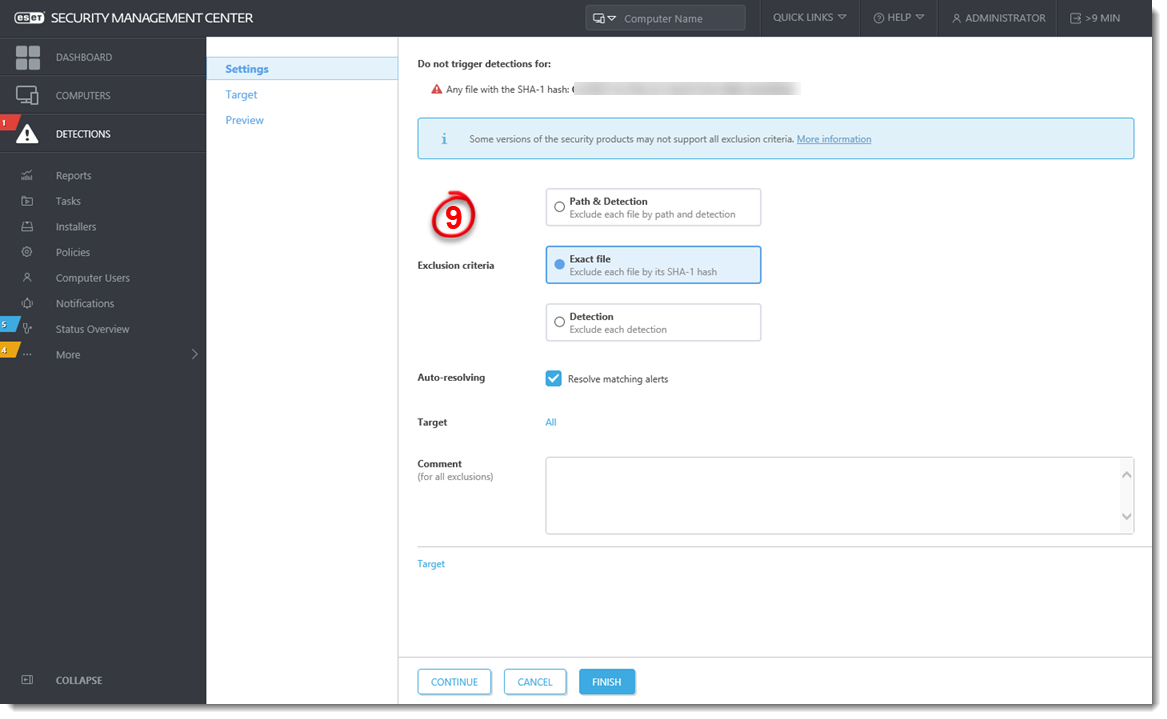
Select the Exclusion criteria. The recommended option is pre-selected based on the detection type. Select the check box Resolve matching alerts to automatically resolve the alerts covered by the exclusion. Optionally, you can add a Comment. Read more about creating exlusions in ESET Online Help.
Figure 1-7
Click the image to view larger in new window
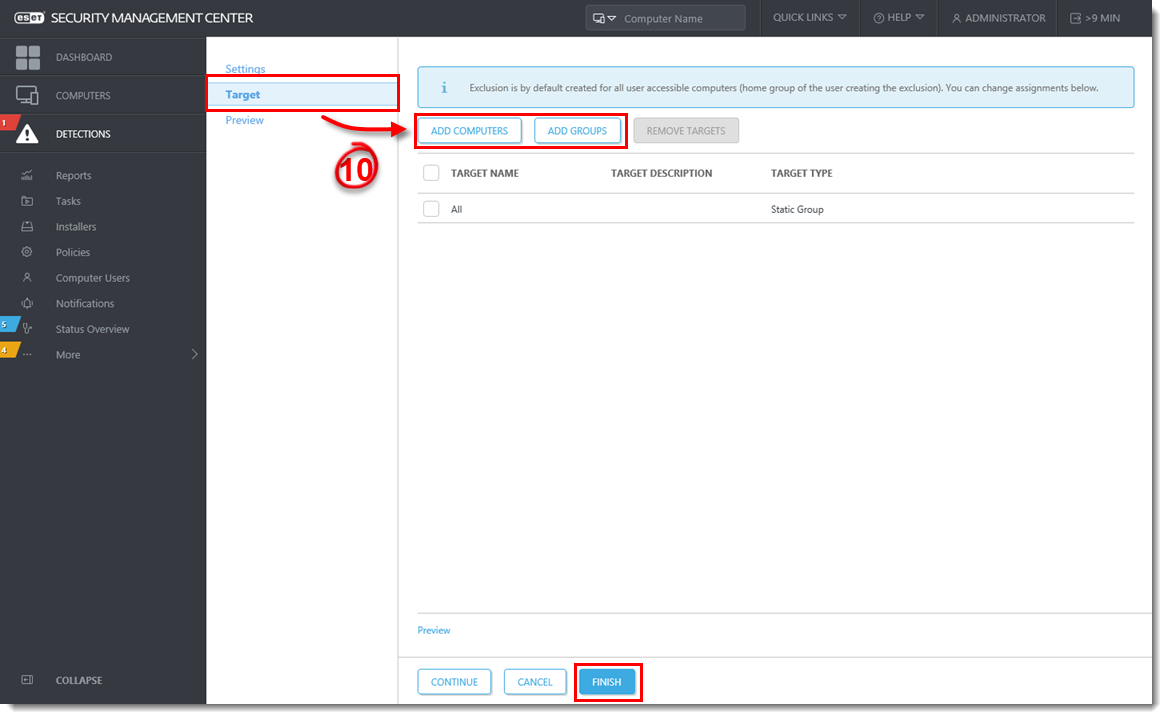
- Click Target and select computer(s) or group(s) where the exclusion will be applied and click Finish.
Figure 1-8
Click the image to view larger in new window - Ransomware Shield no longer detects the excluded application.
- Edit the Policy for ESET business product and click the toggle next to Audit mode to disable it and ensure the automatic ransomware protection of the managed computer.
Figure 1-9
Click the image to view larger in new window