Issue
- Detect client computers without ESET endpoint products installed
Solution
-
Open ESET PROTECT or ESET PROTECT On-Prem in your web browser and log in.
-
Click More → Dynamic Group Templates. Click New Template to create a new Dynamic Group Template. You can also select an existing Dynamic Group Template and click Edit Template to edit it.
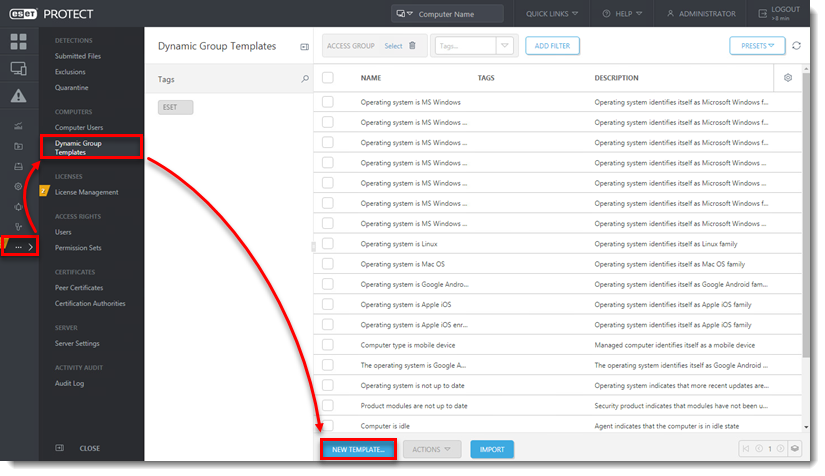
Figure 1-1
-
Type a name for your new Dynamic Group Template into the Name field.
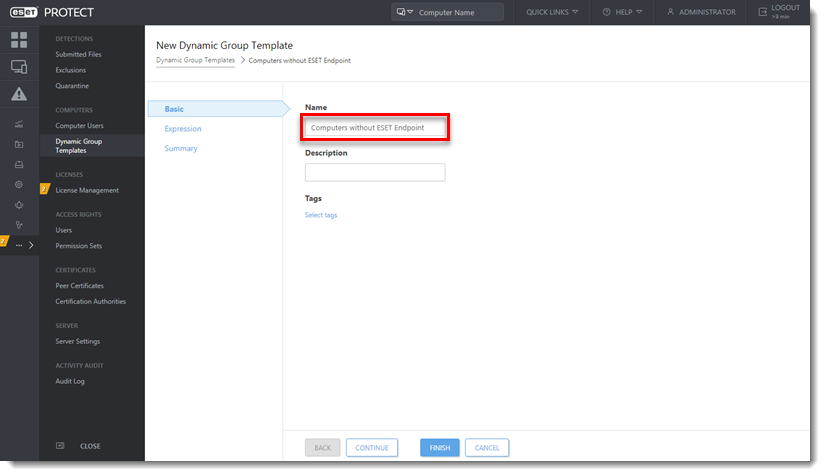
Figure 1-2
-
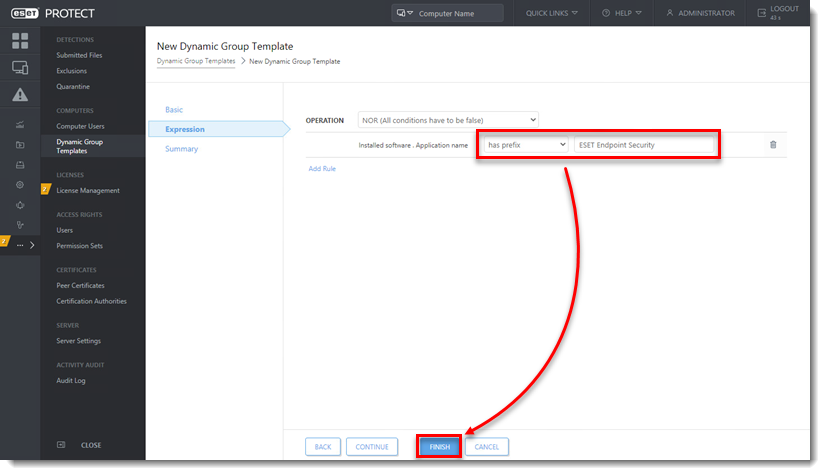
Click Expression, select NOR (All conditions have to be false) from the Operation drop-down menu and click Add Rule. In addition to NOR, you can use the OR (at least one condition has to be true), NAND (At least one condition has to be false), and And (All conditions have to be true) operations to create custom expressions. An expression can contain multiple rules.
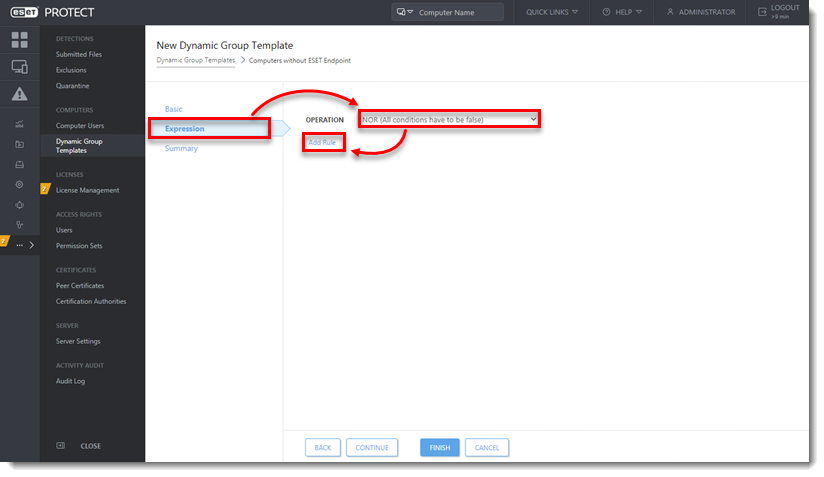
Figure 1-3 -
You can create rules to sort devices by a variety of criteria. Some criteria appear in multiple sections but sort devices using the same logic.
View Dynamic Group Criteria
Activation
Active detections
Computer
Device identifiers
Functionality/Protection problems
Functionality/Protection status
Functionality/Protection status of computer
Hardware
HW inventory/Chasis
- Description
- Identifier
- Manufacturer—Group devices based on the manufacturer
- Serial number
- Type
- Device manufacturer
- Device model
- Firmware type
- Firmware version
- Serial number
- Trusted Platform Module (TPM) Version
HW inventory/Display
- Description
- Identifier
- Manufacturer
- Serial number
HW inventory/Display adapter
- Architecture type
- Description
- Identifier
- Manufacturer
- Memory size [MB]
- Memory type
- Refresh rate (max) [Hz]
HW inventory/Input device
- Description
- Identifier
- Manufacturer
- Type
HW inventory/Mass storage
- Description
- Hardware Encryption Status
- Identifier
- Manufacturer
- Serial number
- Storage capacity [MB]
- Type
HW inventory/Network adapter
- Connection name
- Description
- Identifier
- MAC address
- Manufacturer
- Type
HW inventory/Printer
- Description
- Identifier
- Location type
- Marking type
- Printing type
- Resolution (horizontal - vertical) [pixels per inch]
HW inventory/Processor
- Architecture type
- Clock speed [MHz]
- Description
- Identifier
- Manufacturer
- Number of cores
- Number of logical cores
HW inventory/RAM
- Architecture type
- Capacity [MB]
- Clock speed [Hz]
- Description
- Identifier
- Manufacturer
- Serial number
HW inventory/Sound device
- Description
- Identifier
- Manufacturer
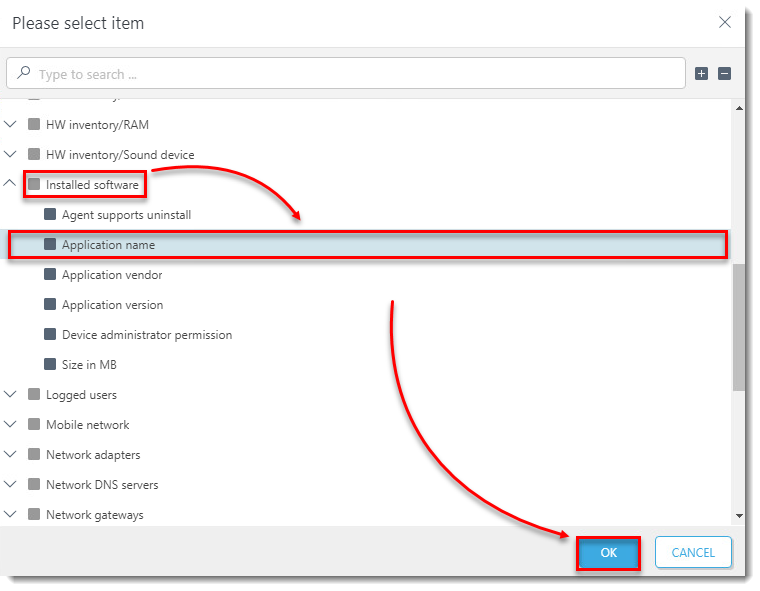
Installed software
- Agent supports uninstall—Group computers with agent versions that support the agent uninstall task
- Application name—Group devices that have a specific application installed or not installed
- Application vendor—Group devices with software from a specific vendor installed
- Application version—Group devices with a specific version of an application
- Device administrator permission—Group devices based on whether you have administrator permissions on them or not
- Size in MB—Group devices based on the amount of drive space in MB that is used by software
Last boot time
- Last boot time
Logged users
Mobile network
Network adapters
Network DNS servers
Network gateways
Network IP addresses
Network WINS servers
OS edition
OS locale
Peer certificate
Performance
Quarantine
Spam top domains
Spam top recipients
Spam top senders
Storage devices
Storage devices capacity
Time zone
For example, expand Installed software, select Application name and click OK.