Issue
-
Your ESET program detects the threat "Autorun.AC" or "Win32Pronny"
-
Files and folders are missing from your network share
- New .exe files called "Porn.exe," "Secret.exe," "Sexy.exe" or "Passwords.exe" are created on your network share
To read more about how Autorun.AC and Win32/Pronny infections are spread and how to avoid them, visit our ESET blog article "My Little Pronny: Autorun worms continue to turn"
Details
INF/Autorun.AC will attempt to utilize autorun features to execute malicious code as well as to hide all files and folders in a network share and replace them with executables that use the same names and icons as the files/folders that were hidden. For example, if you have a Folder named “Accounting” it will be hidden and an executable with the same name will be created. This helps the infection load even if the autorun feature does not because an unsuspecting user will double-click this executable thinking it is their folder.
In addition to replacing existing files, this infection will also create executables with the following names:
- Porn.exe
- Secret.exe
- Sexy.exe
- Passwords.exe
Solution
I. Prepare your network for cleaning (All network computers)
- Disable autorun and removable media. Visit the following Microsoft Knowledge Base article for step-by-step instructions:
- Disable file sharing during the cleaning process to prevent the spread of this infection. Visit the following Microsoft Knowledge Base article for step-by-step instructions:
-
Ensure that you can view hidden files, system files, and file extensions (this will allow you to see any files which may have been hidden by the infection as well as any executables created by the infection). Press the Windows key
 + R, type control folders into the run dialog and press Enter to open the Folder Options window.
+ R, type control folders into the run dialog and press Enter to open the Folder Options window.
- Select the View tab and make sure that Show hidden files, folders and drives is selected. Deselect Hide extensions for known file types and Hide protected operating system files (Recommended). Once you are finished click OK.
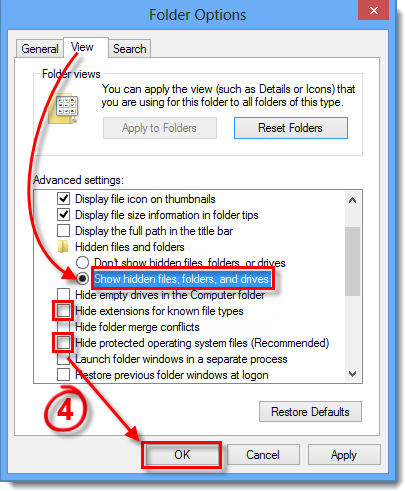
Figure 1-1
II. Remove the infection (Infected computers only)
-
Update your ESET product to the latest virus signature database and perform a computer scan.
-
Once the scan is complete, quarantine and then delete any files identified by your ESET product as infected by Autorun.AC or Win32/Pronny.
-
Check your network share for suspicious files with names like "Porn.exe," "Secret.exe", "Sexy.exe" and "Passwords.exe." If you do not find any such files, continue to step 4. If you do, follow the steps below to disable the User Account(s) that created these files and submit the files to the ESET virus lab for analysis:
-
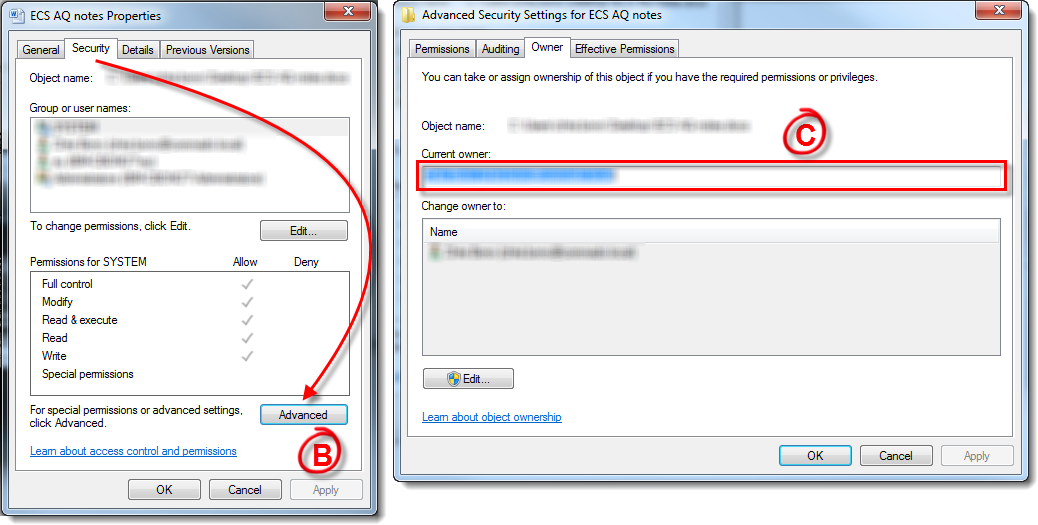
Right-click the suspicious file(s) and select Properties from the context menu.
-
Select the Security tab and click Advanced (see Figure 1-2).
- Click the Owner tab and take note of which User Account created the file. Follow the instructions from the appropriate article below to disable the User Account(s) that created the infected file(s):
-
Right-click the suspicious file(s) and select Properties from the context menu.
Figure 1-2
Click the image to view larger in new window
-
-
Submit any suspicious files to the ESET virus lab for analysis by right-clicking them and selecting Advanced options → Submit files for analysis from the context menu. Follow the on-screen instructions to email your samples to ESET.
-
Submit any suspicious files to the ESET virus lab for analysis by right-clicking them and selecting Advanced options → Submit files for analysis from the context menu. Follow the on-screen instructions to email your samples to ESET.
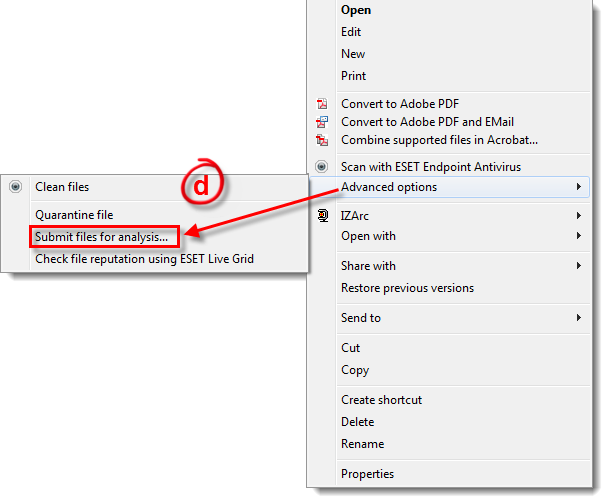
Figure 1-3
-
Restore visibility to the files on your network share that were hidden by the infection:
-
Click Start → All Programs → Accessories. Right-click Command Prompt and choose Run as administrator from the context menu.
-
Windows 8 users: Press the Windows key + Q to open an app search and type cmd into the Search field. Right-click the cmd application when it appears in results and select Run as administrator from the context menu.
-
Windows 8 users: Press the Windows key + Q to open an app search and type cmd into the Search field. Right-click the cmd application when it appears in results and select Run as administrator from the context menu.
-
Type
attrib -h -s "%PathToUnhide%* /s /dinto the command prompt, where "%PathToUnhide% is the location of your network share. Press Enter to run the command.-
For example, the command
attrib -h -s K:mydocs*/s/dwould remove the hidden and system file attributes from files contained in "K:mydocs" and subfolders of "K:mydocs"
-
For example, the command
-
Click Start → All Programs → Accessories. Right-click Command Prompt and choose Run as administrator from the context menu.
III. Restore Network Functionality (All network computers)
-
Restore the settings you changed in step 4 to their prior state: press the Windows key
 + R, type control folders into the run dialog and press Enter to open the folder options window.
+ R, type control folders into the run dialog and press Enter to open the folder options window.
-
Re-enable any disabled user accounts once other computers in your network are clean. Change all user account passwords. ESET also recommends that you change all Admin passwords.
- Restore the Autorun and File and Printer Sharing functionalities.